In July 2024, ESET Research noticed suspicious activity on the system of a trade group in the United States that operates in the financial sector. While helping the affected entity remediate the compromise, we made an unexpected discovery in the victim’s network: malicious tools belonging to FamousSparrow, a China-aligned APT group. There had been no publicly documented FamousSparrow activity since 2022, so the group was thought to be inactive. Not only was FamousSparrow still active during this period, it must have also been hard at work developing its toolset, since the compromised network revealed not one, but two previously undocumented versions of SparrowDoor, FamousSparrow’s flagship backdoor.
Both of these versions of SparrowDoor constitute marked progress over earlier ones, especially in terms of code quality and architecture. One of them resembles the backdoor that researchers at Trend Micro called CrowDoor and attributed to the Earth Estries APT group in November 2024. The other is modular and significantly different from all previous versions. This campaign is also the first documented time FamousSparrow used ShadowPad, a privately sold backdoor, known to only be supplied to China-aligned threat actors.
We further discovered that, as part of this campaign, the threat actor managed to breach a research institute in Mexico just a couple of days prior to the compromise in the US.
While setting up tracking based on what we discovered in these attacks, we uncovered additional activity by the group between 2022 and 2024, which we’re still investigating. Among others, it targeted a governmental institution in Honduras.
This blogpost provides an overview of the toolset used in the July 2024 campaign, focusing on the undocumented versions of the SparrowDoor backdoor that we discovered at the US victim.
Key points of this blogpost:
- ESET researchers discovered that FamousSparrow compromised a trade group for the financial sector in the United States and a research institute in Mexico.
- FamousSparrow deployed two previously undocumented versions of the SparrowDoor backdoor, one of them modular.
- Both versions constitute considerable progress over previous ones and implement parallelization of commands.
- The APT group was also observed using the ShadowPad backdoor for the first time.
- We discuss Microsoft Threat Intelligence’s attribution claims linking FamousSparrow to Salt Typhoon.
FamousSparrow is a cyberespionage group with ties to China, active since at least 2019. We first publicly documented the group in a 2021 blogpost when we observed it exploiting the ProxyLogon vulnerability. The group was initially known for targeting hotels around the world, but has also targeted governments, international organizations, engineering companies, and law firms. FamousSparrow is the only known user of the SparrowDoor backdoor.
Even though FamousSparrow seemed inactive at the time of our discovery, we attribute this activity to the group with high confidence. The deployed payloads are new versions of SparrowDoor, a backdoor that appears to be exclusive to this group. While these new versions exhibit significant upgrades in code quality and architecture, they can still be traced back directly to earlier, publicly documented versions. The loaders used in these attacks also present substantial code overlaps with samples previously attributed to FamousSparrow. Notably, they use the same reflective loader shellcode as the libhost.dll loader sample described in a report from February 2022 published by the UK National Cyber Security Centre (NCSC). Its configuration also shares the same specific format, except for the encryption key which is instead hardcoded in the loader and backdoor. XOR encryption has also been replaced with RC4.
Additionally, C&C server communications use a format very similar to that used in previous SparrowDoor versions.
In 2021, Kaspersky researchers wrote about a threat actor they track as GhostEmperor. Despite some infrastructure overlap with FamousSparrow, we track them as separate groups. In August 2023, Trend Micro noted that some FamousSparrow TTPs overlap with those of Earth Estries. We have also observed code overlaps between SparrowDoor and that group’s HemiGate. These are discussed in more detail in the Plugins section. We believe that the two groups overlap at least partially, but we do not have enough data to fully assess the nature and extent of the link between the two groups.
FamousSparrow and Salt Typhoon
Before we dive into the analysis of FamousSparrow’s toolset, we want to discuss our position on the links between FamousSparrow and Salt Typhoon made by Microsoft Threat Intelligence.
In September 2024, the Wall Street Journal published an article (the article is behind a paywall) reporting that internet service providers in the United States had been compromised by a threat actor named Salt Typhoon. The article relays claims by Microsoft that this threat actor is the same as FamousSparrow and GhostEmperor. It is the first public report that conflates the latter two groups. However, as we already stated, we see GhostEmperor and FamousSparrow as two distinct groups. There are few overlaps between the two but many discrepancies. Both used 27.102.113[.]240 as a download server in 2021. Both groups were also early exploiters of the ProxyLogon vulnerability (CVE-2021-26855) and have used some of the same publicly available tools. However, besides these publicly available tools, each threat actor has its own custom toolset.
Since that initial publication, researchers at Trend Micro have added Earth Estries to the list of groups that are linked to Salt Typhoon. As of this writing, Microsoft, who created the Salt Typhoon cluster, has not published any technical indicators or details about TTPs used by the threat actor, nor provided an explanation for this attribution. To avoid further muddying the waters, we will keep tracking the cluster of activity we see as directly linked to SparrowDoor as FamousSparrow until we have information necessary to reliably assess these attribution claims.
Based on our data and analysis of the publicly available reports, FamousSparrow appears to be its own distinct cluster with loose links to the others mentioned in this section. We believe those links are better explained by positing the existence of a shared third party, such as a digital quartermaster, than by conflating all of these disparate clusters of activity into one.
Technical Analysis
In order to gain initial access to the affected network, FamousSparrow deployed a webshell on an IIS server.
While the specific exploit used to deploy the webshells remains unknown, both victims were found to be running outdated versions of Windows Server and Microsoft Exchange, making them vulnerable to several publicly available exploits.
The threat actor behind the campaign utilized a combination of custom tools, malware, and tools shared by China-aligned APT groups, along with publicly available resources. The final payloads used in the attacks were SparrowDoor and ShadowPad. An overview of the compromise chain deployed in the attacks can be seen in Figure 1.
The initial step involved the threat actor downloading a batch script from an HTTP server at 43.254.216[.]195. This script contained a base64-encoded .NET webshell that was decoded using certutil.exe and saved to a file named s.ashx. This webshell was then copied to the DotNetNuke installation directory. The webshell itself was generic and encrypted data using a hardcoded key.
The threat actor then used the webshell to spawn an interactive remote PowerShell session, gather information about the host and Active Directory domains, and escalate privileges using the BadPotato technique. They also downloaded PowerHub, an open-source post-exploitation framework, to further their access to the compromised systems.
The attacker then used PowerShell’s Invoke-WebRequest to download files comprising SparrowDoor’s trident loader from a server under their control. The loader used a trident loading scheme to execute SparrowDoor, with a legitimate executable for DLL side-loading and encrypted payload files.
The SparrowDoor malware observed in this campaign showed advancements in code quality and architecture compared to older versions. The backdoor now parallelizes time-consuming tasks to handle new commands efficiently. The behavior of SparrowDoor varied based on command line arguments, with different arguments triggering specific actions such as establishing persistence or performing process hollowing.
In conclusion, the FamousSparrow campaign demonstrated a sophisticated attack chain that leveraged vulnerabilities in outdated software to deploy webshells and execute advanced malware like SparrowDoor. The threat actor’s use of custom tools and techniques from other APT groups highlights the complexity and coordination involved in such cyberattacks. The backdoor is also launched immediately with that same argument using the StartServiceA or ShellExecuteA API.
| Command ID | Description | Received data | Sent data |
| 0x32341122 | Initial connection. | No message | Empty |
| 0x32341123 | Send host information. | Empty | · IP address, · unique ID, · OS build number, · OS major version number, · OS minor version number, · computer name, and · username. |
| 0x32341124 | Start interactive shell session (parallel). | Empty | See the Interactive shell subsection. |
| 0x32341127 | Sleep, then move to the next server in the configuration. | Minutes to sleep. | No response |
| 0x32341128 | Uninstall backdoor and clean up. | Empty | No response |
| 0x32341129 | Get current network configuration. | Empty | Network configuration structure. |
| 0x3234112A | Set network configuration. | Network configuration structure. | No response |
| 0x3234112B | Execute loader with the command line argument 11 and terminate the current process. | Empty | No response |
| 0x3234112D | File I/O (parallel). | Operation ID. | See the File operations section. |
| 0x32341131 | Get information about connected drives. | Empty | Array of 26 bytes representing the drive type of all drives from A: to Z: as returned by GetDriveTypeW. |
| 0x32341132 | List files. | Directory path. | File information, one response per file. See the File listing section. |
| 0x32341135 | Create directory. | Directory path. | No response |
| 0x32341136 | Move or rename file. | · Source path length, · source path, · destination path length, and · destination path. |
No response |
| 0x32341137 | Delete file. | File path. | No response |
| 0x32341138 | Start proxy. | Empty | See the Proxy subsection. |
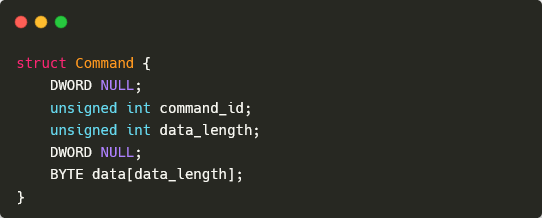
All communication between SparrowDoor and its C&C server uses the same base packet format, as shown in Figure 2. The data section format varies based on the specific command sent, and may be empty. Responses typically use the command ID to link back to the original command, except in certain cases where we will explain the exceptions.
Interactive shell
When the interactive shell command is received, SparrowDoor initiates a new thread and socket for processing. It acknowledges the command with ID 0x32341125 and the victim’s unique ID before spawning a cmd.exe process. Communication between the shell and C&C server occurs via named pipes, with \\.\pipe\id2<address> used for receiving commands and \\.\pipe\id1<address> for output. The command ID 0x32341126 is used for command execution and output relay.
Changing the C&C configuration
Modifying the C&C configuration involves encrypting the received structure and overwriting a portion of the encrypted file. The configuration is reloaded either by moving to the next server or relaunching the backdoor.
File operations
File operations, executed in parallel threads, involve read and write commands. SparrowDoor reads files in chunks and writes data only if the size exceeds the current file size.
The C&C server sends the data in 4 kB chunks with the command ID of 0x32341130.
File Listing:
When the file listing command is received, the backdoor acknowledges it with the command ID 0x32341133. It then uses the FindFirstFileW and FindNextFileW API functions to iterate through files in the target directory. For each file, SparrowDoor sends a message with the command ID 0x32341132 and the information described in Figure 3. Once the iteration is complete, a message with command ID 0x32341134 is sent to indicate the successful completion of the file listing operation.
Proxy:
The backdoor can act as a TCP proxy between the C&C server and another machine. It sends an acknowledgment message with the original command ID and the victim’s unique ID. The server then sends command ID 0x32341139 to initiate the proxy. The proxy functionality is achieved by creating two sockets and using Winsock structures and events to relay packets between the parties.
Modular SparrowDoor:
The modular version of SparrowDoor sends the command header separately from the body, which is RC4 encrypted with the key iotrh^%4CFGTj. It implements commands related to managing the C&C configuration and uninstalling the backdoor. Information about the host machine is sent automatically after the initial connection. Other commands are related to handling plugins, though no such plugins have been observed yet. The commands implemented in the modular version are listed in Table 3.
Plugins:
Installed plugins are stored in a C++ list, with each entry containing a bitmask and a handler function address. The bitmask determines which command IDs are handled by the plugin. Five different command IDs can invoke plugin commands in this version of SparrowDoor. The plugin commands follow a similar path in the code, with minor differences in the handshake process. The commands are parallelized using the same method described in the Commands section. The backdoor sends the response ID, unique host ID, and received data on a new socket. The data seems to operate similarly to the operation ID discussed in the File operations section. Once the handshake is completed, all five commands utilize the same function to handle the plugin command. This function takes the command ID and data from the C&C server, then searches through installed plugins to assign the command to the appropriate handler. This process continues until the backdoor receives a command message that is improperly formatted.
By default, only one plugin is installed, with a bitmask of 0x10000. This plugin manages the installation of new plugins sent by the C&C server. The plugins are transmitted as PE files and are not stored on disk. This, along with the limited function set in the base backdoor, is likely an attempt to avoid detection. Upon receiving a new plugin, it is manually mapped in memory and its fmain export is executed. This function returns a structure containing the function address that provides the bitmask for the plugin and the handler function’s address. If no installed plugin matches the bitmask, the new plugin is added to the list.
Furthermore, older samples with code similarities to this modular version, specifically in handling plugins, have been identified. These samples relate to the backdoor known as HemiGate, as detailed in an August 2023 article by Trend Micro. This suggests that HemiGate may represent an earlier iteration of the modular backdoor, with plugins resembling those used in the current modular version. The summary of the plugins found in HemiGate is provided in Table 4.
The connection between these findings indicates an overlap between the FamousSparrow cluster and Earth Estries. The presence of HemiGate predating SparrowDoor suggests that the modular and parallelized versions of SparrowDoor are possibly being developed simultaneously. The former is loaded using a legitimate version of VLC’s Cache Generator (vlc-gen-cache.exe), which has been renamed to dph.exe and imports functions from the latter. Since VLC plugins can be native DLLs, its cache generator naturally contains code to load and execute such libraries.
Network infrastructure
The ShadowPad C&C server utilizes a self-signed TLS certificate with a SHA-1 fingerprint of BAED2895C80EB6E827A6D47C3DD7B8EFB61ED70B, attempting to mimic those used by Dell. This follows the format described by Hunt Intelligence in an article from February 2024. While this pattern can help track ShadowPad servers, it is not tied to any specific threat actor. One of the C&C servers used by SparrowDoor (45.131.179[.]24:80) had a TLS certificate on port 443 with the same Common Name (CN) as the certificate used by the ShadowPad C&C server mentioned earlier. This server was also the only one present in both versions of SparrowDoor.
In this campaign, we identified three unique SparrowDoor C&C servers, all operating on port 80. The modular sample was set up with amelicen[.]com as its third C&C server, which initially pointed to the IP address mentioned in the previous paragraph. One of the C&C servers configured in the modular sample (43.254.216[.]195:80) was also utilized by the SparrowDoor loader. This raised questions as SparrowDoor typically uses plain TCP, yet files were downloaded over HTTP. The gap of nearly two weeks between the downloads on June 30, 2024, and the compilation of the modular SparrowDoor on July 12, 2024, leaves uncertainty regarding whether the service listening on that port changed during that time or if the SparrowDoor C&C server incorporates functionality to serve files over HTTP.
Conclusion
Despite being presumed inactive between 2022 and 2024 due to lack of activity and public reporting, FamousSparrow has shown continued development of its flagship backdoor, as evidenced by two new versions of SparrowDoor discovered on a US network compromised in July 2024, as well as on a machine in Mexico. Further investigation revealed additional activity by the group during this period, including targeting a governmental institution in Honduras. This newfound activity suggests that FamousSparrow is not only operational but actively developing new versions of SparrowDoor.
We will remain vigilant in monitoring and reporting on FamousSparrow’s activity and will also continue to track discussions regarding potential connections between FamousSparrow and Salt Typhoon.
For inquiries regarding our research published on WeLiveSecurity, please reach out to us at threatintel@eset.com. ESET Research provides private APT intelligence reports and data feeds. sentence to make it more concise:
Please ensure that you have completed all the necessary steps before submitting your application.
Ensure all steps are completed before submitting your application. sentence: “The cat lazily stretched out on the windowsill in the warm sunlight.”
Revised sentence: “Basking in the warm sunlight, the cat leisurely stretched out on the windowsill.” Rewrite the sentence. sentence to make it more concise: “The company is currently in the process of implementing new software to improve efficiency.”
“The company is implementing new software for efficiency.” sentence to make it more concise:
“Please let me know if you have any questions or need further clarification.”
“Please inform me of any questions or need for clarification.” sentence:
The cat is sleeping on the windowsill.
Rewritten sentence:
The cat is curled up on the windowsill, fast asleep. Please rewrite the sentence for me to improve its clarity.