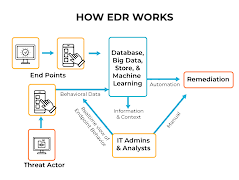
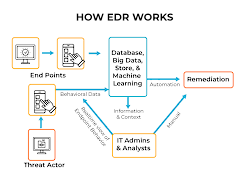
Welcome to the world of Endpoint Detection and Response (EDR)! This comprehensive endpoint security system is your go-to solution for real-time tracking, data collection, automated response, and analysis capabilities. Also known as Endpoint Threat Detection & Response (ETDR), EDR is a vital tool in today’s cybersecurity landscape.

Let’s Dive Deeper into EDR Security Performance
Anton Chuvakin of Gartner coined the term to highlight the emerging security systems capable of identifying and analyzing malicious activities on endpoints. EDR heavily relies on automation to help security teams swiftly recognize and combat attacks.
Essential Functions of an EDR system to determine when to use EDR include:
- Monitoring and collecting endpoint activity data to detect vulnerabilities.
- Analyzing data for threat patterns.
- Automatically responding to recognized threats to contain or remove them, while notifying security personnel.
- Providing forensic tools and analysis capabilities to investigate potential threats and suspicious behaviors.
When to use EDR? – Key Considerations for an EDR Solution
Here are some crucial features to look for when considering EDR:
Incident triaging flow – By automatically prioritizing suspicious events, an EDR solution can help prevent alert fatigue and enable better investigation prioritization.
Threat hunting – Proactive threat detection for identifying threats and potential intrusions.
Data aggregation and enrichment – Providing context to distinguish between false positives and genuine threats.
Integrated response – Quick analysis and response to security incidents.
Multiple response options – Ensuring appropriate responses to events, including eradication and quarantine capabilities.
Endpoint Detection and Response (EDR) Best Practices – Understanding How EDR Works
Explore these best practices to grasp the essence of EDR and its implementation:
Integrate with Other Tools
While EDR is crucial for endpoint protection, it should be complemented with other solutions like patch management, antivirus, firewalls, encryption, and DNS protection as part of a holistic security strategy.
EDR should seamlessly integrate with your existing SIEM (Security Information & Event Management) solution, providing centralized security operations and faster response times.
Utilize Network Segmentation
In addition to EDR, network segmentation plays a vital role in enhancing security. Segmented networks restrict endpoint access to specific services and data repositories, reducing the impact of successful attacks.
Ethernet Switch Paths (ESPs) can further bolster network security by concealing the network structure from potential attackers.
Choose the Right Provider for Your Business
Selecting the ideal EDR solution involves assessing functionality, cost, and compatibility with your organization’s needs. Research multiple providers to find the perfect fit for your security requirements.
Consider these questions before deciding when to use EDR:
- Is the EDR solution compatible with your current operating systems and applications?
- Does the solution integrate well with third-party security tools?
Integration is key to a successful security strategy, but remember to tailor your choices to fit your specific needs and conditions.
Human Talent is Essential for EDR Success
While EDR can automate threat detection, human analysts are crucial for interpreting and responding to alerts effectively. Establishing a prioritization strategy and minimizing false positives are vital for efficient EDR deployment.
Whether through internal staff or external service providers, having skilled analysts to assess and act on EDR-generated data is essential for optimal security.
In Conclusion – Embracing EDR for Enhanced Security
Endpoint Detection and Response (EDR) is your shield against cyber threats, providing continuous monitoring and rapid response capabilities for endpoint security. EDR solutions capture and analyze endpoint device behavior to detect and mitigate potential attacks.
For comprehensive protection and visibility over your digital assets, EDR security solutions like Open EDR offer unmatched security features. Contact us to learn more about EDR and elevate your company’s security posture. Visit for more
See Also:
What is XDR
FAQ Section
A: EDR is your ally for real-time visibility, proactive threat detection, incident response, and enhanced security.
A: EDR is not just for large organizations; small businesses can benefit from its security enhancements.
A: While EDR is powerful, it’s best used in conjunction with other security solutions for comprehensive protection.
A: Regular maintenance and monitoring are essential for optimal EDR performance.