XDR, or Extended Detection and Response, is a cutting-edge initiative for detecting and responding to cyber threats comprehensively. It offers holistic protection against cyber attacks, misuse, and unauthorized access. XDR is a game-changer in the realm of security as it seamlessly integrates data across different layers including endpoints, servers, cloud workloads, and networks.
What is XDR?
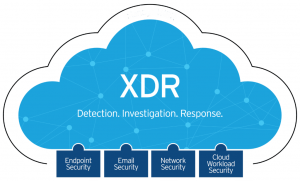
XDR facilitates the integration of endpoint and workload security capabilities with enhanced visibility into the network and cloud environments, thereby reducing blind spots, swiftly detecting threats, and automating remediation based on contextual insights.
Let’s delve deeper into understanding “what is XDR?”
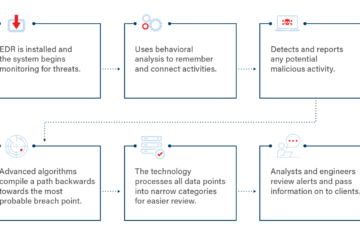
What is XDR: How does XDR work?
XDR represents an effective approach to threat detection and response. In today’s landscape, where threats abound across all data, XDR solutions offer immediate protection. With XDR, cybersecurity teams can:
- Track threats from any location within the organization.
- Enhance operational efficiency for technology users.
- Proactively and swiftly identify hidden threats.
- Conclude investigations more efficiently.
- Reduce false positives by correlating and validating alerts.
- Integrate pertinent data for expedited and accurate incident triage.
- Support user and technology behavior analysis seamlessly.
Cyberattacks can be thwarted, and security processes can be streamlined and fortified through the adoption of XDR platforms. This allows companies to focus on strategic initiatives with the assurance that their data and applications are safeguarded. You now have a grasp of “what is XDR” and its operational dynamics.
What is XDR: What are the benefits of XDR?
The capabilities of endpoint XDR transcend those of traditional EDR offerings, delivering multiple tangible advantages for fortifying an organization’s IT landscape. These include:
Perfect visibility and context provision.
XDR outshines EDR and third-party security services by delivering comprehensive visibility into the security environment. It empowers security analysts with insights on every aspect of a threat, from its inception to its full scope. XDR enables swift responses to threats.
Automation enhancement.
Through automation, XDR streamlines the detection, response, and eradication of manual steps in security processes. This is a pivotal method to manage vast volumes of security data and execute intricate tasks for IT teams.
Comprehensive endpoint protection.
With AI-driven antivirus and threat intelligence integration, XDR aids in blocking malware, exploits, and file-less attacks effectively. It serves as an indispensable tool for IT professionals.
Prioritization of critical alerts.
IT professionals often grapple with numerous alerts generated daily. Leveraging XDR’s data analysis and correlation capabilities, crucial threats can be promptly identified and prioritized.
Swift threat detection and response.
Thanks to robust security posture, XDR solutions facilitate quicker threat detection and response, ensuring enhanced cybersecurity resilience.
Operational efficiency.
With XDR, threats are viewed holistically across the entire environment. It streamlines centralized data collection and response, tightly integrating them into the environment and broader security ecosystem.
What is XDR: What are the common pitfalls to avoid?
While the XDR platform is a robust security strategy, selecting a solution that leverages its capabilities optimally is crucial for maximizing its efficacy. When choosing a platform, watch out for the following pitfalls:
Lack of integration.
XDR is only effective when seamlessly integrated within the IT environment. Complex integrations consume time for IT teams and diminish the utility of your XDR solution.
Operational complexity.
Ensure that IT and security teams can collaborate seamlessly. If not, the time saved by implementing XDR might be offset by the effort required to learn and set up the platform.
Inadequate automation.
Automation is a core capability of XDR. It enables the platform to adapt effectively to evolving conditions and execute targeted responses beyond merely blocking traffic to affected devices.
What is XDR: What sets XDR apart from EDR?
XDR is a broader concept compared to EDR. While EDR provides a singular viewpoint, XDR enables telemetry and behavioral analysis across multiple security layers, offering security teams a comprehensive overview. EDR often falls short in detecting a full spectrum of attacks, a gap that XDR addresses effectively. EDR tends to involve time-consuming and complex investigations.
In addition to providing visibility into compromised endpoints, EDR necessitates alerting security teams when an attack progresses across endpoints. Here, XDR emerges as the preferred solution by providing a holistic view of activity across the system, thereby eliminating visibility gaps.
What is XDR: Final Thoughts?
Have all your queries about “What is XDR?” been addressed?
If so, trust Open EDR for the best solution tailored to your needs. Reach out to them at openedr.com.
See Also
What is EDR
Definition of EDR
FAQ Section
A: XDR or Extended Detection and Response is a cybersecurity solution that enhances the threat visibility, detection, and response capabilities of an organization by unifying various security tools under its nexus.
A: XDR offers the right approach to tackle sophisticated and complex threats and cyberattacks effectively and promptly. With advanced data analysis, machine learning, and the efficiency of detecting and isolating stealthy and covert attacks.
A: XDR is a concept that uses existing security tools siloed under a unified mechanism to improve threat visibility and adds comprehensive response action to counter sophisticated cyber-attacks effectively.
A: It’s generally observed that medium to large organizations with sensitive data require XDR security solutions to counter cyber threats more effectively. By implementing XDR, organizations can detect persistent threats and other covert attacks.