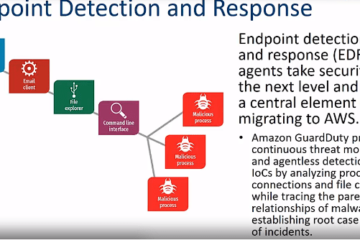
Fileless malware has emerged as one of the more sophisticated types of threats in recent years. This sneaky menace operates in the shadows, exploiting system vulnerabilities often without leaving a trace on traditional file storage.
In this blog, our aim is to define fileless malware, explore some real-world examples (including digging deeper about PowerShell-based attacks), and provide actionable insights for defenses.
What is Fileless Malware?
Fileless malware represents a breed of cyber threats that exist solely in a computer’s memory, avoiding the need for conventional file storage. By leveraging existing system tools and applications, attackers can infiltrate, compromise, and manipulate systems with alarming stealth. Threat actors have increasingly used fileless malware, though malicious code that exists only in memory isn’t a very new idea, with early examples like Code Red worm in 2001.
The ultimate malware is fileless, but it’s important to note that initial stages of the attack may use files. While fileless malware avoids placing the malicious executables on the file system, these kinds of attacks can use scripts or documents to download the payload.
In-Memory Exploitation:
Traditional malware relies on executable files, but fileless malware exploits vulnerabilities in memory processes. The infamous Poweliks Trojan from 2014 serves as a stark example, highlighting the potential of attacks that reside only in the registry. Poweliks exploited a vulnerability in Microsoft Word, using an email with an attached Word document to create a hidden autostart registry key, which allowed it to survive system re-boots and maintain persistence. Later stages of the attack executed JScript code, then a PowerShell script, and finally the malicious code of Poweliks.
Living-off-the-Land Attacks:
Fileless malware often employs living-off-the-land attacks, harnessing legitimate system tools like PowerShell and Windows Management Instrumentation (WMI) for nefarious purposes. These LotL attacks fly under the radar, making detection a formidable challenge.
As an example, the sneaky backdoor POSHSPY described by Mandiant leverages both PowerShell and WMI. By using only legitimate system processes, the malicious code can only be detected through enhanced logging or in memory.
Digging Into Examples of Fileless Malware Attacks
- Exploit Kits: Exploit kits are malicious tools or software packages that cybercriminals use to automate the process of exploiting vulnerabilities in software or web applications. They often target known vulnerabilities in browsers, plugins, or operating systems, attempting to deliver malware to the victim’s system. Exploit kits are commonly distributed through malicious websites or compromised legitimate sites.
- Legitimate Admin Tools: The LotL method helps evade detection as the activities may appear normal. Attackers can use legitimate programs or system tools, co-opting these trusted applications for malicious purposes. Instead of relying on external malware, attackers leverage native tools that are already present on the victim’s system. Examples include PowerShell (more about PowerShell below), Windows Management Instrumentation (WMI), or command-line utilities.
- Registry Resident Malware: Registry resident malware is a type of malicious software that embeds itself within the Windows Registry, a central database storing configuration settings for the operating system. By doing so, the malware can achieve persistence, ensuring it remains on the system even after reboots. The registry provides an attractive target for attackers seeking to establish a foothold in the system.
- Memory-Only Malware: Memory-only malware operates exclusively in a computer’s volatile memory (RAM) without leaving any traces on the hard drive. This type of malware avoids traditional file-based detection, making it challenging to identify and analyze. Memory-only malware often leverages techniques like code injection to execute malicious code directly in the system’s memory.
- Fileless Ransomware: Fileless ransomware is a variant of ransomware that executes in a way that minimizes or entirely avoids creating files on the victim’s system. Instead of encrypting files stored on the hard drive, fileless ransomware may encrypt files in-memory or leverage other techniques to extort the victim. Ransomware attackers use this approach to bypass traditional security measures focused on file-based detection, so they can encrypt the victim’s data and demand a ransom payment.
- Stolen Credentials: Stolen credentials refer to the unauthorized acquisition of usernames and passwords belonging to individuals or organizations. Cybercriminals often gain access to these credentials through various means, such as phishing, credential stuffing attacks, or data breaches. Once obtained, stolen credentials can be used to gain unauthorized access to accounts, networks, or sensitive information.
Understanding these terms is crucial for individuals and organizations to enhance their cybersecurity posture. Each represents a different facet of cyber threats, and addressing these challenges requires a combination of technological defenses, user awareness, and proactive security measures.
Fileless Attacks Using PowerShell
Let’s dig deeper into how attackers use PowerShell for fileless attacks, commonly referred to as “PowerShell-based fileless attacks.” PowerShell is a legitimate and powerful scripting language embedded in Windows operating systems. In these attacks, cybercriminals leverage PowerShell to execute malicious commands directly in memory without leaving traditional artifacts on the file system. POSHSPY which we mentioned above is one example of an attack that used a PowerShell payload.
Here’s some examples of how PowerShell can be used in fileless malware attacks:
- PowerShell as an Attack Vector: Cybercriminals exploit PowerShell as an attack vector because it is pre-installed on Windows systems, making it readily available for malicious activities. PowerShell allows attackers to execute commands, scripts, and even download and run payloads directly in memory, making detection challenging.
- Living-off-the-Land Attacks: PowerShell is often used in living-off-the-land attacks, where attackers leverage legitimate tools already present on the system for malicious purposes. Instead of relying on traditional malware files, attackers use PowerShell to carry out various stages of the attack, such as reconnaissance, lateral movement, and data exfiltration.
- PowerShell Commands and Techniques: Attackers craft PowerShell commands and scripts to evade detection by traditional antivirus and endpoint protection solutions. Techniques like obfuscation, script block logging evasion, and encoded command payloads are commonly employed to make the malicious PowerShell activities more challenging to identify.
- Code Injection: In some cases, fileless malware using PowerShell may inject its code directly into the memory space of legitimate processes, further obfuscating its presence. This technique allows the malware to operate without relying on traditional executable files that can be detected by signature-based antivirus solutions.
- Post-Exploitation Activities: PowerShell is frequently used for post-exploitation activities, such as privilege escalation, lateral movement within a network, and the execution of additional payloads. By leveraging PowerShell, attackers can carry out sophisticated and multi-stage attacks, complicating the detection and response process.
- Detection Challenges: Detecting PowerShell-based fileless attacks requires advanced security measures that can monitor PowerShell activity, analyze script behavior, and identify patterns indicative of malicious intent.
Given the prevalence of PowerShell in legitimate system administration tasks, distinguishing between normal and malicious PowerShell activity is a significant challenge. If you’re using Intezer, our autonomous incident response processes extract PowerShell and other scripts, using AI to detect any malicious activities.
10 Stages of a Fileless Malware Attack
Fileless malware attacks typically unfold in several stages, often following a stealthy and sophisticated progression. While the specific tactics and techniques can vary, the following stages provide a general framework for understanding how fileless malware operates:
- Initial Compromise and Delivery: The attack begins with the delivery of the fileless malware to the target system. This can occur through various vectors such as phishing emails, malicious websites, or compromised software.
- Vulnerability Exploitation: The malware exploits vulnerabilities in the system, commonly targeting software, applications, or the operating system itself. This can involve leveraging known or zero-day vulnerabilities to gain a foothold.
- In-Memory Execution and Injection: Instead of writing malicious code to disk, fileless malware injects its code directly into the system’s memory. This technique helps the malware evade traditional antivirus and endpoint detection solutions.
- Privilege Escalation: The malware seeks to escalate its privileges to gain increased access to the system or network. This may involve exploiting vulnerabilities or leveraging legitimate tools to escalate from user to administrator privileges.
- Lateral Movement and Network Propagation: The fileless malware may move laterally within the network, attempting to spread to other systems. It can use various techniques, such as exploiting shared resources or using legitimate network administration tools for malicious purposes.
- Persistence and Registry Modifications: To ensure long-term access and survivability, fileless malware often establishes persistence mechanisms. This can involve modifying the Windows Registry or creating scheduled tasks to ensure the malware persists across system reboots.
- Command and Control (C2) Communication with External Servers: The malware establishes communication with external command and control servers operated by the attackers. This enables the malware to receive instructions, updates, and exfiltrate sensitive data.
- Execution of Malicious Actions and Data Exfiltration: The fileless malware may exfiltrate sensitive data from the compromised system. This can include personally identifiable information, intellectual property, or other valuable data. In the case of ransomware, the data is encrypted while the attacker attempts to extort payment from the victim.
- Covering Tracks with Anti-Forensic Techniques: To evade detection and analysis, the malware employs anti-forensic techniques. This may include deleting log entries, altering timestamps, or obfuscating its presence in the system.
- Post-Exploitation Activities or Further Exploitation: The attackers may exploit the compromised system for additional malicious activities, such as launching secondary attacks, installing additional payloads, or using the compromised system as a launching point for attacks on other targets.
Understanding these stages is crucial for developing effective cybersecurity strategies to detect, prevent, and respond to fileless malware attacks. Implementing a multi-layered defense approach, including advanced endpoint protection, network monitoring, and user education, is essential to mitigate the risks associated with fileless malware.
How to Protect Against Fileless Malware
Before we look closer at more advanced techniques for investigating suspicious behavior and detecting fileless threats, you’ll want to make sure you have your basic security measures in place. Most organizations implementing cybersecurity best practices will find these five areas help prevent or detect fileless attacks:
- Endpoint Security Solutions: Make sure you have advanced endpoint protection tools with behavioral analysis and heuristic detection capabilities to identify and mitigate fileless malware threats.
- Strong Tier 1 SOC Analysis: Invest in an autonomous SOC solution or a strong managed service that will have the knowledge of identifying and escalating fileless attacks from the very first stage. Getting strong analysis from your Tier 1 SOC is crucial in order to differentiate between normal administrative activity and living-on-the-land attacks.
- Regular Software Updates: Patch those vulnerabilities! Keep your operating systems, applications, and security software up-to-date to patch vulnerabilities and reduce the risk of exploitation.
- Least Privilege Principle: Implement the principle of least privilege to restrict user access, minimizing the impact of fileless malware on your organization. Minimizing the number of people who have admin accounts to key systems, for example, reduces the risk if an attacker steals someone’s credentials.
- Application Whitelisting: Utilize application whitelisting to control the execution of scripts and processes, preventing unauthorized actions by fileless malware.
What about monitoring and incident response for fileless threats though? Let’s look at how you can automate investigations into suspicious behavior, detecting evasive fileless threats hiding in memory or abusing legitimate tools.
Automating Memory Forensics to Protect Against Fileless Malware
Memory forensics is not just a tool; it’s a crucial pillar in the foundation of resilient cybersecurity.
As fileless malware continues to exploit vulnerabilities in memory, organizations must embrace advanced techniques like automating memory forensics. By integrating memory analysis into their cybersecurity strategy, businesses can proactively detect and respond to in-memory threats, fortifying their defenses against the ever-evolving landscape of cyber threats.
Intezer’s unique ability to autonomously collect and analyze malicious code and scripts makes it a powerful tool against fileless attacks. Intezer continuously monitors your alerts, investigating unusual activities and automatically scanning the memory of potentially infected endpoints. By immediately conducting a scan on any impacted live endpoints, Intezer can quickly identify machines that are infected and which ones contain no traces of an in-memory threat. This allows teams to get answers quickly, prevent a threat from spreading, and ensure business operations can continue securely and uninterrupted.
Fileless malware poses a clear and present danger to organizations of all sizes. By understanding its intricacies and adopting a multi-layered security approach, businesses can fortify their defenses against this elusive adversary. Staying proactive, vigilant, and informed is paramount in the ongoing battle against fileless malware. As cyber threats continue to evolve, so must our defenses.
Try Intezer for free or book a demo to learn more.