Hey there, are you ready to dive deep into the world of protecting digital assets in our ever-evolving digital landscape? In a world where cyber threats are constantly evolving in sophistication and severity, it’s essential to understand the importance of endpoint detection and response (EDR) in securing your digital assets. Let’s explore the definitions, benefits, and distinctions of EDR from antivirus programs, along with some best practices. So grab a seat, get comfy, and let’s explore this fascinating field together!
Endpoint Detection and Response Benefits


Endpoint detection and response (EDR) has become a critical defense mechanism against cyber threats in the rapidly evolving cybersecurity landscape. So, you might be wondering, What is endpoint detection and response? Simply put, it’s a cybersecurity method that monitors and responds to threats targeting the network’s endpoints.
Endpoints refer to any device like computers, servers, or mobile devices that interact with your network. These endpoints are often targeted by hackers seeking unauthorized access or exploiting software vulnerabilities.
Understanding What is endpoint detection and response reveals that EDR works by constantly monitoring these devices for any signs of malicious activity. By analyzing data from various sources like log files, network traffic, and system registries using advanced algorithms and machine-learning techniques, EDR can proactively detect potential threats. Unlike antivirus software that relies on signatures for detection, EDR actively searches for indicators of compromise across endpoints.
Early detection and rapid response are the primary goals of EDR. To achieve this, it’s crucial to understand What is endpoint detection and response. EDR enables security teams to take swift action by identifying anomalies in real-time and providing detailed insights into potential threats.
Compared to traditional antivirus software, EDR is more proactive as it employs behavioral analysis to detect threats rather than relying solely on signatures. By comprehending what endpoint detection and response entails and implementing an effective EDR solution, businesses can better monitor their network endpoints and quickly identify any intrusions or malicious activities, thereby reducing the impact of potential breaches. Whether you’re managing a small company’s network or a large enterprise’s, integrating endpoint detection and response should be a top priority.
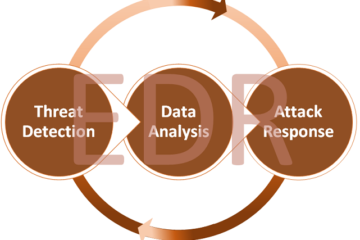
How EDR Works
Now that you’re familiar with What is endpoint detection and response, let’s delve into how this powerful cybersecurity solution operates. Protecting your digital assets is incomplete without endpoint detection and response (EDR). But have you ever wondered about the inner workings of EDR? Let’s explore how this cutting-edge tool functions.
EDR primarily focuses on monitoring and analyzing endpoint devices like laptops, workstations, and servers. By collecting massive amounts of real-time data from these endpoints, EDR can identify abnormal or malicious behavior. Using advanced algorithms and machine learning, EDR can detect potential cyber threats by analyzing normal behavior for anomalies.
When EDR identifies a problem, it promptly takes corrective actions. This could involve disconnecting the device from the network, halting malicious programs, or restoring infected data. Being proactive, EDR can respond swiftly to new threats and prevent significant damage.
Furthermore, EDR provides valuable insights into endpoint activities through comprehensive logs and reports. This information enables security teams to analyze incidents by understanding their context. By gaining insights into attackers’ methods at the endpoint level, organizations can enhance their overall security.
In addition to its detection capabilities, EDR offers robust response features. Automated responses based on rule sets can be triggered in case of an incident, while security analysts can intervene in more complex scenarios. This ensures that threats are swiftly contained, minimizing disruptions to business operations.
In essence, EDR provides a comprehensive approach to safeguarding your digital assets by combining real-time monitoring with rapid response capabilities. Setting it apart from traditional signature-based solutions, EDR can detect both known and unknown threats through behavioral analysis. Therefore, it plays a vital role in modern cybersecurity defenses.
Conclusion
While antivirus software remains essential for combating known malware, it struggles to keep pace with newer threats that evade signature-based defenses. Understanding What is endpoint detection and response reveals that EDR excels in this scenario by actively searching for malicious activities on endpoints, rather than just blocking attacks. In a constantly evolving threat landscape, organizations relying solely on traditional antivirus solutions may be vulnerable to advanced persistent threats (APTs) or zero-day attacks. Implementing an EDR solution offers the ability to monitor and respond swiftly to security threats, making it a critical component of effective cybersecurity defenses. Endpoint detection and response (EDR) isn’t just a buzzword; it’s a powerful tool for protecting your digital assets against sophisticated cyber threats. Take proactive steps with this security solution!
Related Resources:
EDR Definition
following sentence:
“The cat was sleeping peacefully on the window sill.”
The cat peacefully slept on the window sill.