Did you know that there were 236 million ransomware attacks worldwide in the first half of 2022? That’s a staggering number, and it’s only increasing. According to the APWG’s Phishing Activity Trends Report 2022, there were three lakh phishing attacks in 2022, triple the number compared to 2021.
Why Choose EDR Software?


Your remote employee endpoints are vulnerable to cyber threats. Securing them with EDR Software is crucial to prevent cybercriminals from infiltrating your system through an endpoint. Let’s delve into what endpoint detection and response software is and how it can benefit your organization.
Why Do We Choose EDR Software?
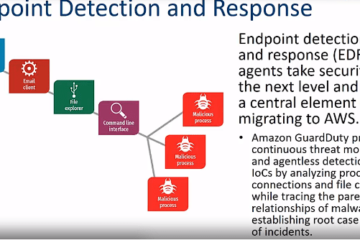
EDR software integrates tools that enable your cybersecurity team to monitor, detect, contain, analyze, respond, and report on malicious activities on endpoint devices connected to your corporate network.
EDR solutions have garnered significant attention in the digital realm. This software empowers your team to isolate an endpoint immediately upon detecting malicious activity. Additionally, it enables your team to take corrective measures to minimize the potential damage from a data breach or attack.
Benefits Of Endpoint Detection and Response
Here are some advantages of EDR that justify the investment of your time and resources in this software.
Transparency about the Company’s Security Posture The primary benefit of an EDR tool is that it enhances visibility across all endpoints. Your network gains a remarkable level of transparency, allowing your team to identify blind spots and vulnerabilities. Hackers may attempt to infiltrate the system, but with this software, your cybersecurity team will be vigilant. They can detect any attack on any endpoint, ensuring a comprehensive overview of your network’s health. Identifying vulnerabilities and addressing them becomes seamless with an EDR tool.
Detects Unnoticed Attacks Countless attacks go undetected without endpoint security tools. Your organization’s network remains vulnerable every second without EDR software. Hence, investing in a tool that leaves no attack unnoticed is imperative.
Modern-day hackers employ sophisticated tactics, techniques, and procedures to target organizations. They constantly evolve their tactics to evade detection by security software. Cybercriminals often execute advanced persistent threats by compromising an endpoint and then launching a detailed attack on your network. Without an endpoint detection tool, detecting and thwarting such attacks becomes challenging. Most EDR tools enable you to identify indicators of compromise and address threats proactively. Installing this software on your endpoints ensures a robust response strategy.
Efficient Response Another advantage of EDR software is the ability to detect a malicious attack before it spreads or causes significant damage. Without this software, it may take your team three to five hours to identify a breach and formulate a response. Delayed responses increase the risk of widespread network infiltration and escalate breach costs.
With an endpoint tool like Open EDR®, you can swiftly isolate the infected device in a controlled environment. This isolation grants your team sufficient time to investigate the attack and devise a response plan. It accelerates threat detection and response, minimizing potential damage.
Investigation of Past Attacks Understanding the malware techniques used by attackers gives you an edge in defending against them. EDR tools feature forensic and analysis tools that enable your team to trace the attack chain and comprehend how an attack unfolded. This analysis equips you with insights into the attacker’s tactics, enabling you to fortify your defenses. Leveraging this information helps you preempt future attacks using similar malware.
What is EDR Software and Know the Key Features of Advanced EDR Software
Vendors incorporate diverse techniques and tools in their endpoint detection and response software. While each software may offer unique features, certain standard features are prevalent across most tools.
Reporting Console Your dashboard typically includes a reporting console that provides visibility and transparency regarding your security status across all endpoints. It facilitates monitoring of system activities.
Advanced Response Feature Modern tools integrate advanced analytics and forensic capabilities, enabling deep analysis of past attacks. These tools offer valuable insights.
Universal OS Support Organizations utilize various operating systems, necessitating compatibility with multiple OS types for optimal tool performance.
Wrap up – What is EDR Software
Implementing reliable EDR software safeguards your corporate endpoints, enabling your organization to detect and thwart both known and unknown threats.
See Also