Unlocking the Power of EDR Security
Are your company’s endpoints truly secure against the ever-evolving landscape of cyber threats? In today’s dynamic environment, traditional security measures may fall short in safeguarding critical data and thwarting malicious attacks. This is where Endpoint Detection and Response (EDR) steps in to redefine security paradigms. EDR security meaning encapsulates a state-of-the-art defense mechanism that offers real-time monitoring and response capabilities to combat threats targeting endpoints.
Let’s delve deeper into the realm of endpoint detection and response (EDR) to understand its significance in modern cybersecurity, the challenges encountered during implementation, and the strategies to overcome them. Brace yourself for an enlightening journey as we explore how EDR security meaning can revolutionize your organizational security posture.
Decoding EDR Security Meaning
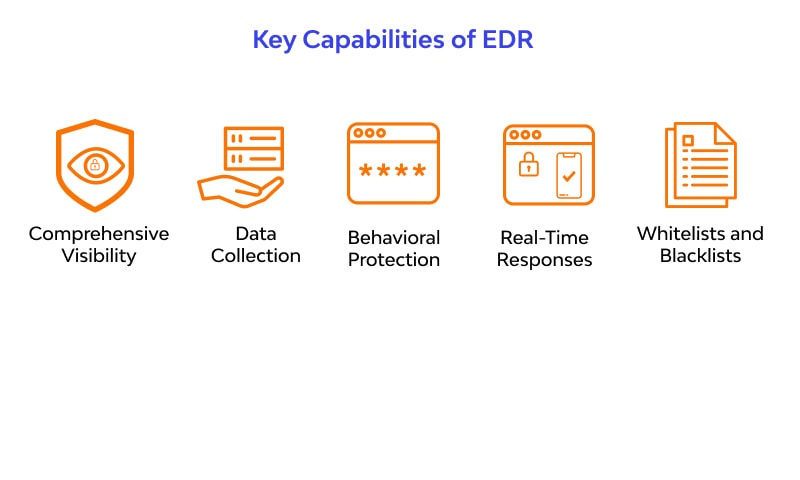
Endpoint Detection and Response (EDR) aims to proactively detect, investigate, mitigate, and respond to sophisticated threats targeting endpoints within an organization’s network. Endpoints encompass devices like computers, laptops, servers, and mobile devices that interact with the network.
Utilizing innovative methodologies such as behavioral analysis and machine learning algorithms,
EDR security meaning transcends conventional antivirus software by detecting new or zero-day malware. Upon integration with an endpoint, EDR solutions collect data on processes, file access patterns, user activities, and network connections, enabling swift identification and response to malicious activities.
By amalgamating comprehensive endpoint visibility with threat intelligence feeds and sandboxing technology, EDR security empowers organizations to swiftly identify and neutralize threats before they inflict significant harm.
Navigating Challenges in EDR Implementation
Aligning EDR security meaning with your organizational needs.
Embarking on the implementation of Endpoint Detection and Response (EDR) solutions entails overcoming common hurdles that organizations often encounter. By anticipating and addressing these impediments, businesses can streamline the deployment process.
Selecting an EDR system that suits your organization’s requirements is a pivotal decision. Amidst a plethora of competing products, finding an EDR solution that aligns with your security objectives can be challenging but diligent research and expert consultations can ease this process.
Ensuring compatibility of EDR security-meaning tools with existing network infrastructure is another stumbling block. Conducting preliminary compatibility assessments is essential to prevent disruptions and ensure seamless integration with current security systems.
An often overlooked aspect during deployment is the formulation of explicit incident response policies and workflows. In the absence of well-defined processes, team members may struggle to effectively address threats or incidents flagged by the EDR security meaning.
Organizations also encounter formidable barriers such as budget constraints and skill shortages when implementing EDR systems. Successful deployment of EDR security meaning necessitates investments in time and resources, supported by proficient personnel capable of leveraging the technology effectively.
By preemptively acknowledging and preparing for these prevalent challenges, organizations can navigate through the complexities of implementing endpoint detection and response systems, leveraging tailored best practices to suit their unique contexts.
Optimizing EDR Security Meaning: Best Practices
When integrating Endpoint Detection and Response (EDR) security meaning into your organizational framework, adhering to best practices can enhance the efficacy of deployment. Consider the following key recommendations:
- Evaluate Your Organization’s Needs: Prior to commencing implementation, assess your organization’s specific security requirements. Understand the nature of threats faced and the level of protection necessitated.
- Select the Right Solution: Opt for an EDR security meaning that caters to your organization’s demands. Look for features like real-time monitoring, threat intelligence integration, and incident response functionalities.
- Strategize in Advance: Develop a comprehensive implementation strategy outlining timelines, resource allocation, and communication protocols. This facilitates a seamless deployment process.
- Educate Your Team: Provide thorough training to IT personnel and end-users on leveraging the EDR security meaning effectively. Empowering them to promptly identify and respond to potential threats is crucial.
- Regular Updates and Patches: Keep your EDR solution updated with the latest patches and software upgrades from the vendor. This mitigates vulnerabilities and fortifies system resilience.
- Vigilant Monitoring: Establish clear guidelines for monitoring alerts generated by the EDR security meaning solution to swiftly identify and mitigate potential threats.
Remember, implementing EDR security meaning is an ongoing endeavor rather than a one-time task – continuously assess its efficacy through testing and adapt it in alignment with evolving threat landscapes.
Epilogue – Elevating EDR Security Meaning
A robust security framework hinges on the ability to combat threats at the endpoint with precision. By understanding the nuances of EDR security meaning implementations, businesses can better address their security imperatives. Best practices encompassing automated endpoint scanning, incident response protocols, employee training, and persistent monitoring systems enable organizations to safeguard their networks and data in real-time.
Related Resources:
EDR Definition



