In today’s digital landscape, the rise of malicious cyberattacks targeting businesses, government entities, and the general public is a pressing concern. To combat these threats effectively, a combination of prevention and detection strategies is crucial. This is where the leading EDR solutions excel.
Endpoint Detection and Response (EDR) tools offer real-time monitoring, threat data analysis, and automated response capabilities. This article delves into the top EDR solutions in the market that boast cutting-edge features.

Exploring Endpoint Detection and Response Solutions
Traditionally, cybersecurity efforts focused on preemptively blocking attacks. However, the evolution of threats has necessitated a shift towards a proactive approach that combines prevention with detection. The best EDR solutions monitor endpoints in real-time for suspicious activities.
By collecting and analyzing data, these tools can identify potential threats and initiate automated responses to thwart or remediate attacks. This proactive stance empowers security teams to stay ahead of evolving threats.
Complementing traditional antivirus software, the top EDR solutions excel in detecting and alerting about malicious activities that may go unnoticed by conventional security measures.
Top 5 EDR Solutions on the Market
The leading EDR solutions offer a comprehensive suite of capabilities, from monitoring various devices, data, and applications to safeguarding endpoints against cyber threats.
- OpenEDR®, a Premier EDR Solution Provider
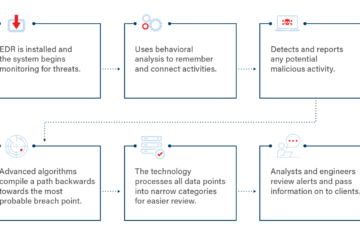
OpenEDR® from Xcitium stands out as an open-source EDR platform that delivers advanced threat detection with MITRE ATT&CK visibility. This allows for event correlation and deep analysis of cyber threat activities.
OpenEDR® gathers endpoint activity data and employs sophisticated analytics to detect malicious behavior. It offers comprehensive monitoring, visual representation of endpoint security data, and malware analysis capabilities.
Key features of OpenEDR® include:
- Extensive visibility across all activities in virtualized and physical environments.
- Robust threat detection capabilities.
- Swift response to contain and mitigate threats.
- Effortless management and detailed reporting to enhance security posture.
- Accessibility to security professionals of all organization sizes due to its open-source nature.
One such cloud-based solution is Cisco Secure Endpoint, which integrates prevention, threat hunting, detection, and response capabilities to safeguard diverse operating systems. Its robust protection mechanisms effectively block cyber threats at the entry point, making it a top choice among EDR solutions.
Key features of Cisco Secure Endpoint include:
- Centralized view for security teams to respond swiftly to threats.
- Advanced search functionalities for streamlined threat investigation.
- Accurate identification of attacks.
Another standout EDR solution is CrowdStrike, known for its autonomous cybersecurity capabilities that prevent, detect, and respond to attacks in real-time. Powered by artificial intelligence, CrowdStrike offers unparalleled threat visibility and response across endpoints, IoT devices, and cloud environments.
Key features of CrowdStrike include:
- Real-Time Response for enhanced security team visibility.
- Integration with cyber threat intelligence for rapid attack detection.
- Microsoft Defender for Endpoint
Microsoft’s Defender for Endpoint is a top-tier EDR solution that provides proactive protection and host-breach detection across various operating systems. Its advanced features include deep insights into Windows threats, anti-exploit technology, and efficient endpoint quarantine capabilities.
Built on a foundation of threat intelligence and cutting-edge technology, these top EDR solutions offer organizations comprehensive threat visibility and response capabilities. Among these, OpenEDR® emerges as a standout choice, providing continuous endpoint monitoring and holistic visibility into all activities. Explore OpenEDR® today to fortify your cybersecurity defenses.