Hey there, fellow security enthusiasts! Ever wondered how blue teams defend while red teams attack? It’s all about working together towards a common goal – identifying and addressing gaps in organizations’ defenses before cybercriminals can exploit them.
In our previous post, we explored some open-source tools for blue teams defending against simulated attacks and highlighted four gadgets that could potentially cause security issues in the wrong hands. Today, we’re back with five cutting-edge tools that hobbyist hardware hackers, red teamers, or ethical hackers can use to sharpen their skills or carry out their work.
1. Raspberry Pi 5
Let’s start with the versatile Raspberry Pi 5. This affordable single-board computer is a favorite among security professionals, students, and enthusiasts alike. Loaded with various penetration testing tools, it can morph into a network sniffer, run automated security tests, and analyze IoT devices for vulnerabilities.

With operating systems like Kali Linux tailored for penetration testing, Raspberry Pi is a powerhouse for security assessments.
- FruityWifi: Audit wireless networks and perform advanced attacks.
- Ha-Pi: Tools for penetration testing, including Aircrack Ng Suite and Metasploit.
- Raspberry Pwn: Tools like scapy, Wireshark, and tcpdump.
- Wireless Attack Toolkit (WAT): Wi-Fi network penetration testing on ARM platforms.
- PwnPi: Debian Wheezy simplified for pentesting.
- NetPi: Create a network analyzer with commercial-grade features.
2. HackRF One
The HackRF One is a must-have for radio frequency enthusiasts. This open-source device can transmit and receive signals from 1 MHz to 6 GHz, allowing you to experiment with various wireless communications.

Whether testing wireless vulnerabilities or troubleshooting signal issues, the HackRF One is your go-to tool.
3. WiFi Pineapple
The WiFi Pineapple is a sleek gadget that uncovers the secrets of wireless networks by simulating access points to lure unsuspecting users. Its custom operating system, Pineapple OS, is designed for wireless penetration testing.

From evil twin attacks to deauth tests, the WiFi Pineapple is a powerhouse for wireless network security assessments.
4. Deauther Watch
The Deauther Watch disrupts Wi-Fi connections by executing deauthentication attacks, making it a handy tool for testing vulnerabilities in Wi-Fi networks.

With features like Wi-Fi scanning and packet capturing, the Deauther Watch is a handy tool for Wi-Fi security assessments.
5. Ubertooth One
The Ubertooth One is designed for monitoring Bluetooth communications and analyzing Bluetooth packets, making it ideal for testing Bluetooth-enabled IoT devices.
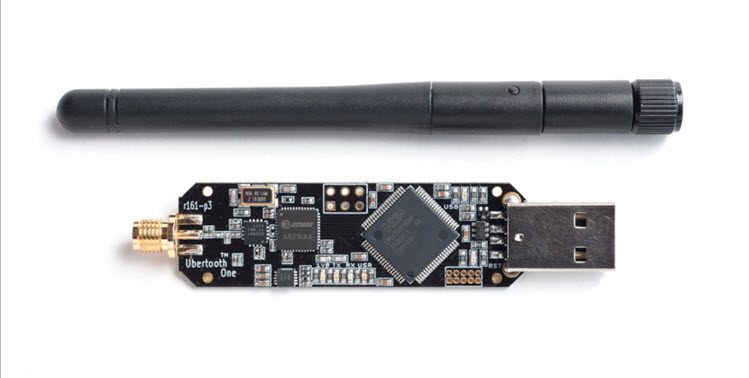
From sniffing Bluetooth communications to analyzing IoT devices, the Ubertooth One is a versatile tool for security testing.
Conclusion
Remember, these tools should be used ethically and with permission. Unauthorized use can have severe consequences. Stay safe, stay secure!



