In this blogpost, ESET researchers provide an analysis of Spellbinder, a lateral movement tool for performing adversary-in-the-middle attacks, used by the China-aligned threat actor that we have named TheWizards. Spellbinder enables adversary-in-the-middle (AitM) attacks, through IPv6 stateless address autoconfiguration (SLAAC) spoofing, to move laterally in the compromised network, intercepting packets and redirecting the traffic of legitimate Chinese software so that it downloads malicious updates from a server controlled by the attackers.
Key points in this blogpost:
- We discovered a malicious downloader being deployed, by legitimate Chinese software update mechanisms, onto victims’ machines.
- The downloader seeks to deploy a modular backdoor that we have named WizardNet.
- We analyzed Spellbinder: the tool the attackers use to conduct local adversary-in-the-middle attacks and to redirect traffic to an attacker-controlled server to deliver the group’s signature backdoor WizardNet.
- We provide details abouts links between TheWizards and the Chinese company Dianke Network Security Technology, also known as UPSEC.
Overview
In 2022, we noticed that a suspicious DLL had been downloaded by the popular Chinese input method software application known as Sogou Pinyin. The DLL, named after a legitimate component of that software, was a dropper for a downloader that retrieved an encrypted blob from a remote server. The blob contained shellcode that loads the backdoor we have named WizardNet.
Our research led to the discovery of a tool, used by the attackers, that is designed to perform adversary-in-the-middle attacks using IPv6 SLAAC spoofing to intercept and reply to packets in a network, allowing the attackers to redirect traffic and serve malicious updates targeting legitimate Chinese software.
Victimology
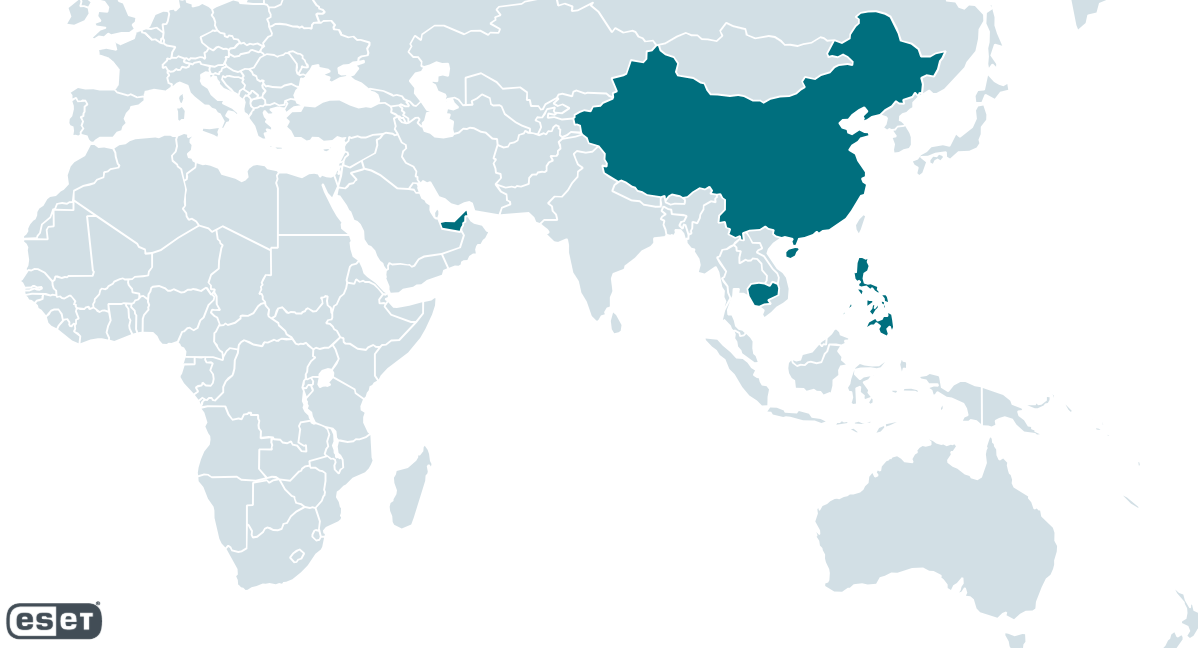
TheWizards has been constantly active since at least 2022 up to the time of writing. According to ESET telemetry, TheWizards targets individuals, gambling companies, and unknown entities in the Philippines, Cambodia, the United Arab Emirates, mainland China, and Hong Kong. Its geographical distribution is shown in Figure 1.
Spellbinder, the IPv6 AitM tool
We initially discovered and analyzed this tool in 2022, and observed a new version with a few changes that was deployed to compromised machines in 2023 and 2024. Once the attackers gain access to a machine in a targeted network, they deploy an archive called AVGApplicationFrameHostS.zip, and extract its components into %PROGRAMFILES%\AVG Technologies. The files include:
- AVGApplicationFrameHost.exe
- wsc.dll
- log.dat
- winpcap.exe
Next, the attackers install winpcap.exe and run AVGApplicationFrameHost.exe. The latter, originally named wsc_proxy.exe, is a legitimate software component from AVG that is abused to side-load wsc.dll; this DLL simply reads the shellcode from the file log.dat and executes it in memory. The shellcode decompresses and loads Spellbinder in memory.
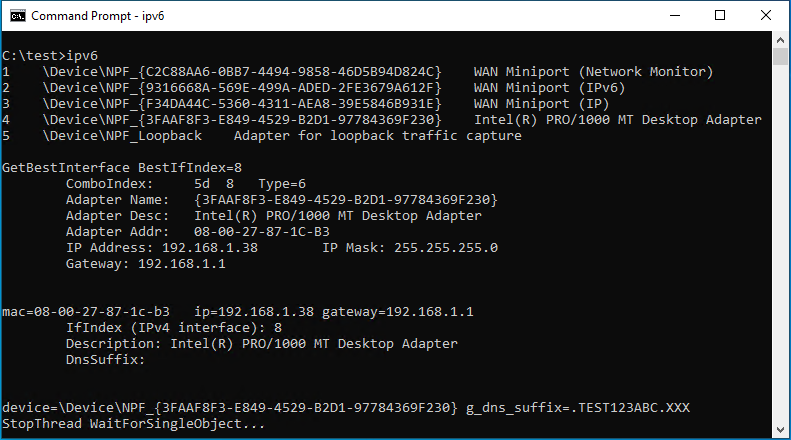
Spellbinder uses the WinPcap library to capture packets and to reply to packets when needed. The first task is to select or find an adapter with which to perform the packet capture. The code uses the WinPcap API pcap_findalldevs to get all available adapter devices. The devices are itemized in a numbered list for the attacker. Optionally, Spellbinder accepts, as an argument, an index that can be used to pick one adapter from this list. If a device is not supplied, Spellbinder uses the Windows APIs GetBestInterface and GetAdapterInfo to find a suitable adapter, and prints its information on screen.
Figure 2 shows the output of Spellbinder when no item number is supplied. In that case, the tool finds the most suitable adapter by itself.
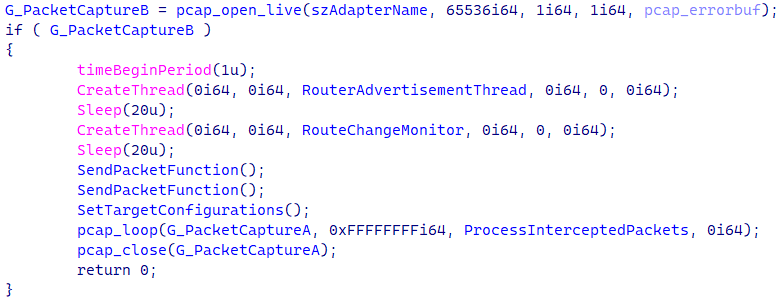
As shown in Figure 3, once an adapter is found, Spellbinder uses the WinPcap pcap_open_live API to start capturing packets, and creates two threads: one to send ICMPv6 Router Advertisement packets (explained in the next section), and a thread to monitor network changes. The WinPcap pcap_loop API does the job of invoking a callback function from Spellbinder every time a new packet is captured.
Router Advertisement thread
This attack vector was discussed by the IETF as early as 2008 and is caused by a commonly overlooked network misconfiguration of IPv4 and IPv6 coexistence. It was then thoroughly detailed in 2011 by Alec Waters, who dubbed it the SLAAC Attack. It takes advantage of IPv6’s Network Discovery Protocol in which ICMPv6 Router Advertisement (RA) messages advertise that an IPv6-capable router is present in the network so that hosts that support IPv6, or are soliciting an IPv6-capable router, can adopt the advertising device as their default gateway.
Spellbinder sends a multicast RA packet every 200 ms to ff02::1 (“all nodes”); Windows machines in the network with IPv6 enabled will autoconfigure via stateless address autoconfiguration (SLAAC) using information provided in the RA message, and begin sending IPv6 traffic to the machine running Spellbinder, where packets will be intercepted, analyzed, and replied to where applicable. Figure 4 illustrates the first stage of the attack.
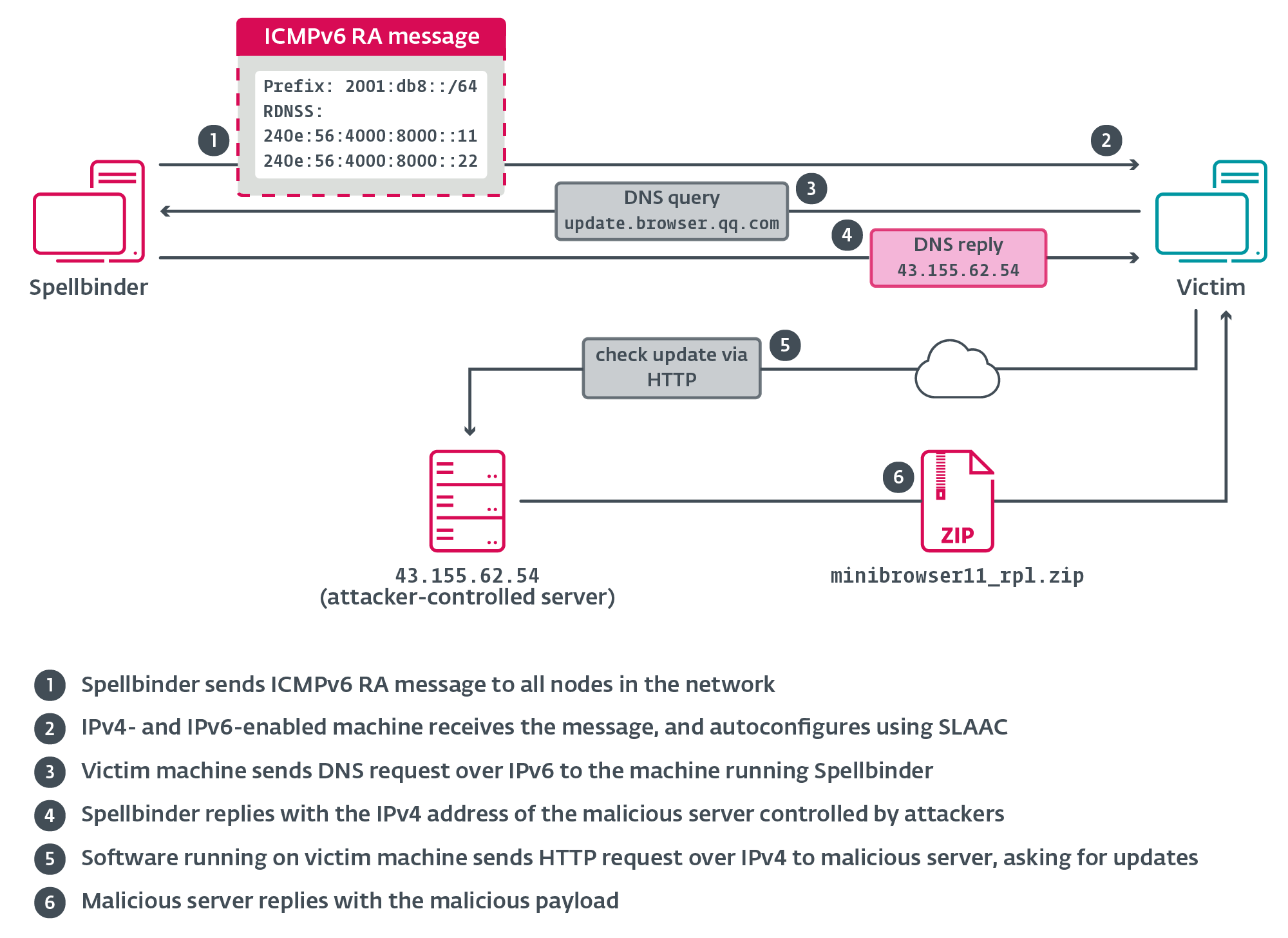
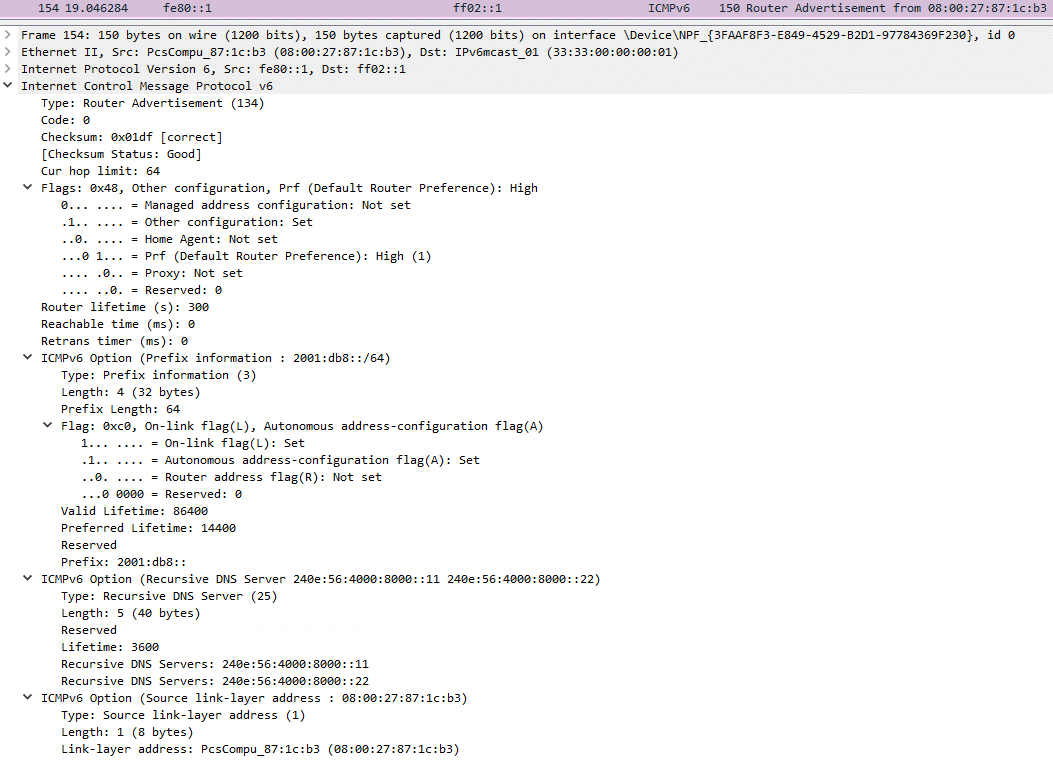
Spellbinder’s RA packet comprises four main parts:
- RA Flags: with the “managed address configuration” flag set to 0, indicating SLAAC usage to hosts.
- The prefix option instructing the host to utilize the 2001:db8::/64 prefix for generating its IPv6 address, a non-internet-routable subnet reserved for documentation.
- The RDNSS option providing the host with the DNS server addresses 240e:56:4000:8000::11 and 240e:56:4000:8000::22 from AS4134, China Telecom Backbone, though they are not responding to DNS requests from the Internet.
- The source link-layer option presenting the MAC address of Spellbinder’s machine as the router for the local network segment.
Displayed in Figure 5 is an ICMPv6 RA message transmitted by Spellbinder.

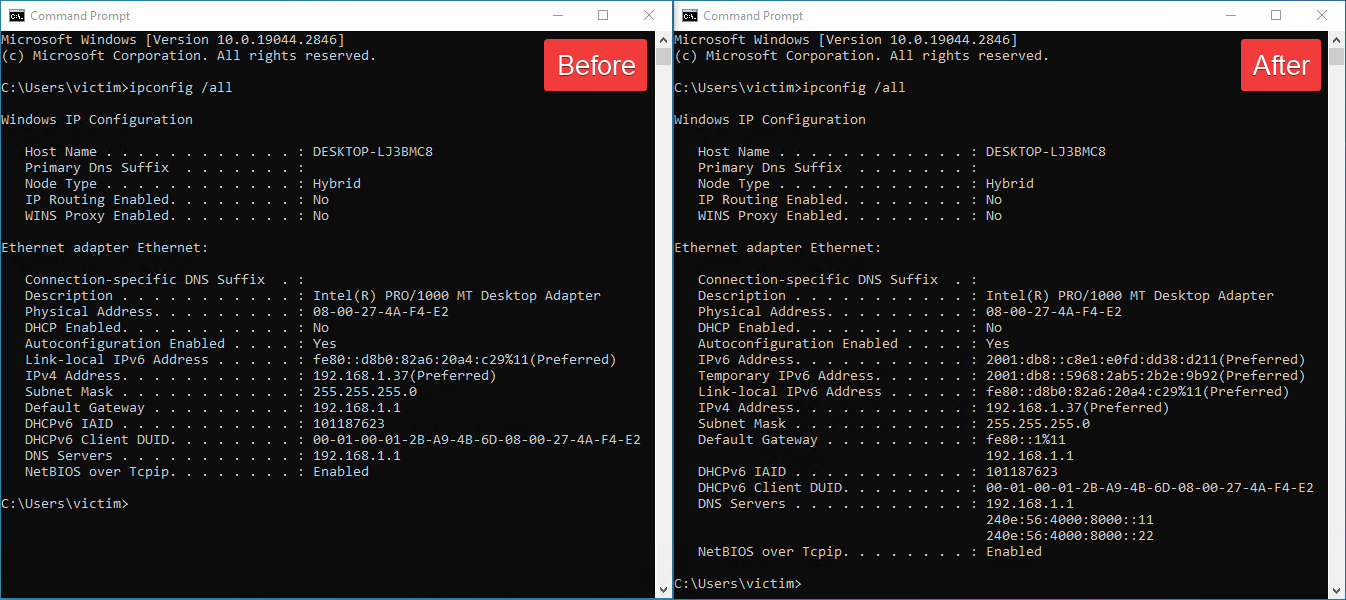
Figure 6 showcases the Windows ipconfig /all command output before and after running Spellbinder from a compromised machine within the network.
Packet handling
Spellbinder’s callback function processes captured raw packets. It includes a custom parser to identify packets for processing, replying to, or displaying attacker information. Table 1 outlines relevant protocols, packet types, and actions performed by Spellbinder.
Table 1. Protocols and packet types for Spellbinder responses
| Protocol | Message type | Action taken |
| DNS | Query | Responds to DNS query if domain matches preset list. |
| ICMPv6 | Router Solicitation | Sends RA packet. |
| Router Advertisement | Logs packet information. | |
| Neighbor Advertisement (NA) | Sends NA packet. | |
| DHCPv6 | Solicit | Sends Advertisement with DNS servers’ IPv6 addresses. |
| Information-request | Sends Reply with DNS servers’ IPv6 addresses. | |
| ARP | Any | Logs packet details. |
Spellbinder checks DNS queries against a hardcoded subdomain list. Figure 7 depicts the code segment performing this validation.
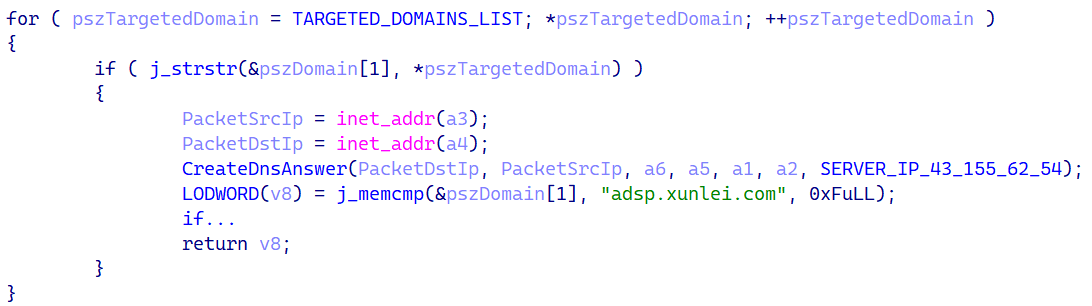
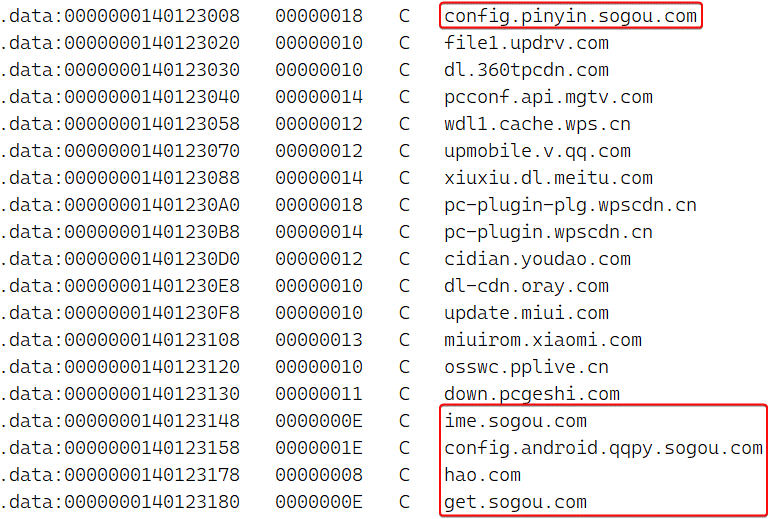
Figure 8 displays a subset of domains targeted by Spellbinder, including popular Chinese platforms like Tencent, Baidu, Xunlei, and more.
When a queried domain matches the list, Spellbinder crafts and sends a DNS answer message with a predetermined IP address. The tool notifies the attacker of this action, as shown in Figure 9.
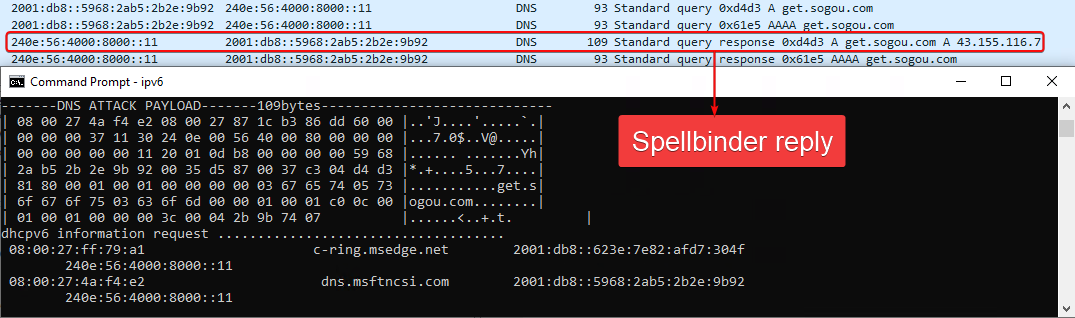
Figure 10 presents the packet details of a DNS answer message sent by Spellbinder, as captured in Wireshark.
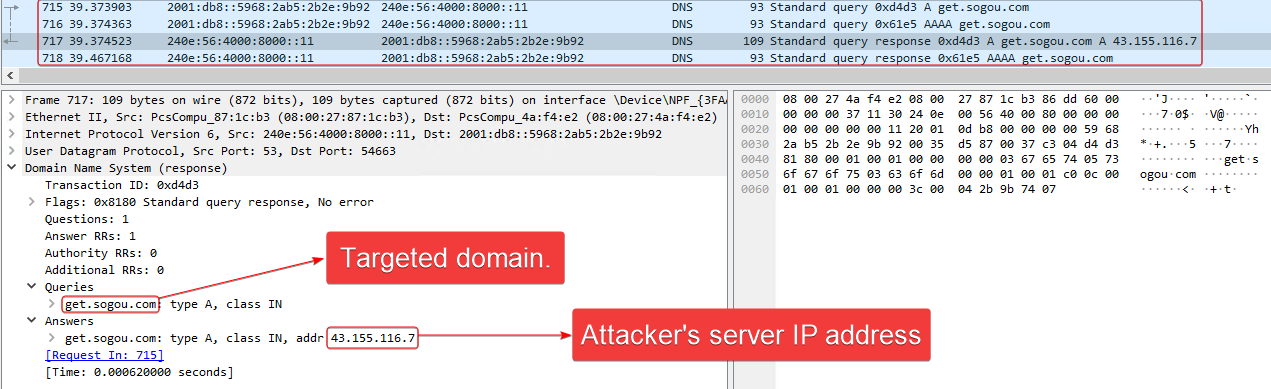
Update Hijacking
One notable incident in 2024 involved the hijacking of Tencent QQ software update. The malicious server issuing update instructions was active, as depicted in Figure 11.
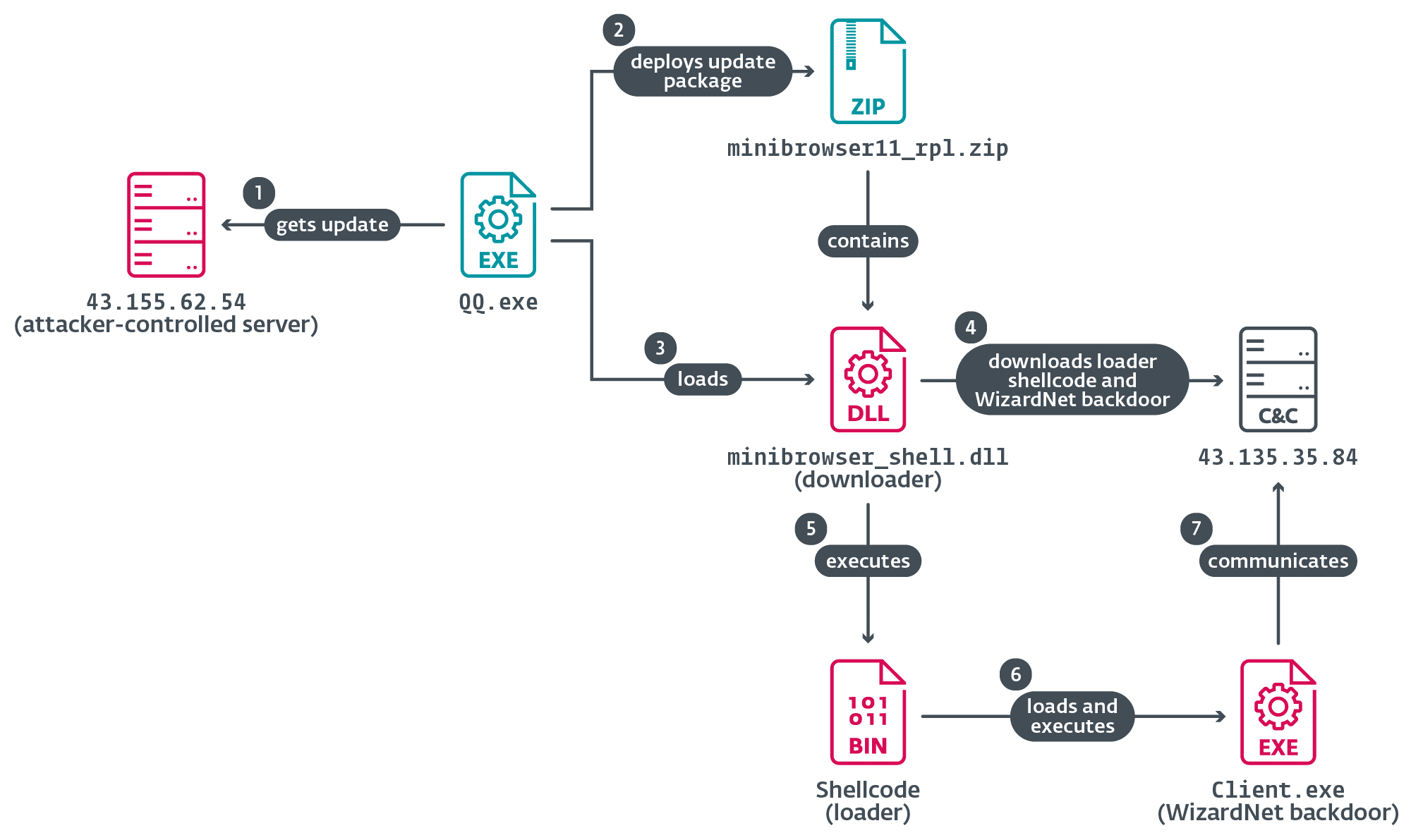
The legitimate QQ.exe software component sent an HTTP request to update.browser.qq.com.
The Spellbinder tool intercepts the DNS query for the specified domain name and responds with the IP address of a server controlled by the attacker, such as 43.155.62[.]54, which is currently serving malicious updates.
Upon receiving the request, the hijacking server sends JSON-formatted instructions to download an archive hosted on the same server. The archive contains a file named “minibrowser11.zip” and various other details for installation.
Subsequently, QQ.exe downloads the archive minibrowser11_rpl.zip and installs its contents on the victim’s machine, including the malicious minibrowser_shell.dll.
After a successful AitM attack, the compromised machine executes the malicious minibrowser_shell.dll downloader. This DLL connects to the attacker’s server via TCP, retrieves an encrypted blob with loader code and the WizardNet backdoor.
The loader code bypasses AMSI and disables Event Logging before executing the payload in memory using the .NET runtime. The payload is decrypted and loaded into memory for execution.
The WizardNet backdoor, a modular implant, connects to a remote controller to receive and execute .NET modules on the compromised machine. It creates a unique identifier for the computer and communicates with the C&C server using encryption and decryption techniques.
WizardNet supports various commands to execute .NET modules in memory, expanding its capabilities on the compromised system. These commands allow loading, invoking, and unloading modules as needed. The u method in the plugin assembly is called to perform cleanup tasks before being unloaded. This includes sending system and orchestrator information to the server in two messages, listing security solutions, and obtaining information related to the current process and network settings. Additionally, the method checks for running processes matching specific names associated with security products. If you have any questions about this service, make sure to check out the ESET Threat Intelligence page for more information.
IoCs
If you are looking for a detailed list of indicators of compromise and samples, head over to our GitHub repository.
Files
| SHA-1 | Filename | ESET detection name | Description |
| 9784A1483B4586EB12D8 |
minibrowser_shell |
Win32/Agent.AGNF | Downloader component. |
Network
| IP | Domain | Provider | First seen | Details |
| 43.155.116[.]7 | hao[.]com | ACEVILLEPTELTD-SG | 2022‑11‑06 | Server issuing malicious updates to legitimate applications in 2022. Used by Spellbinder. (Note: Spellbinder hijacks requests to resolve the hao[.]com domain.) |
For more insights and details, feel free to visit the 
phrase “I need to finish my homework before I can go out with my friends.”
My friends and I can only go out once I have completed my homework. sentence in a passive voice:
“The teacher assigned the homework to the students.”
The homework was assigned to the students by the teacher.

