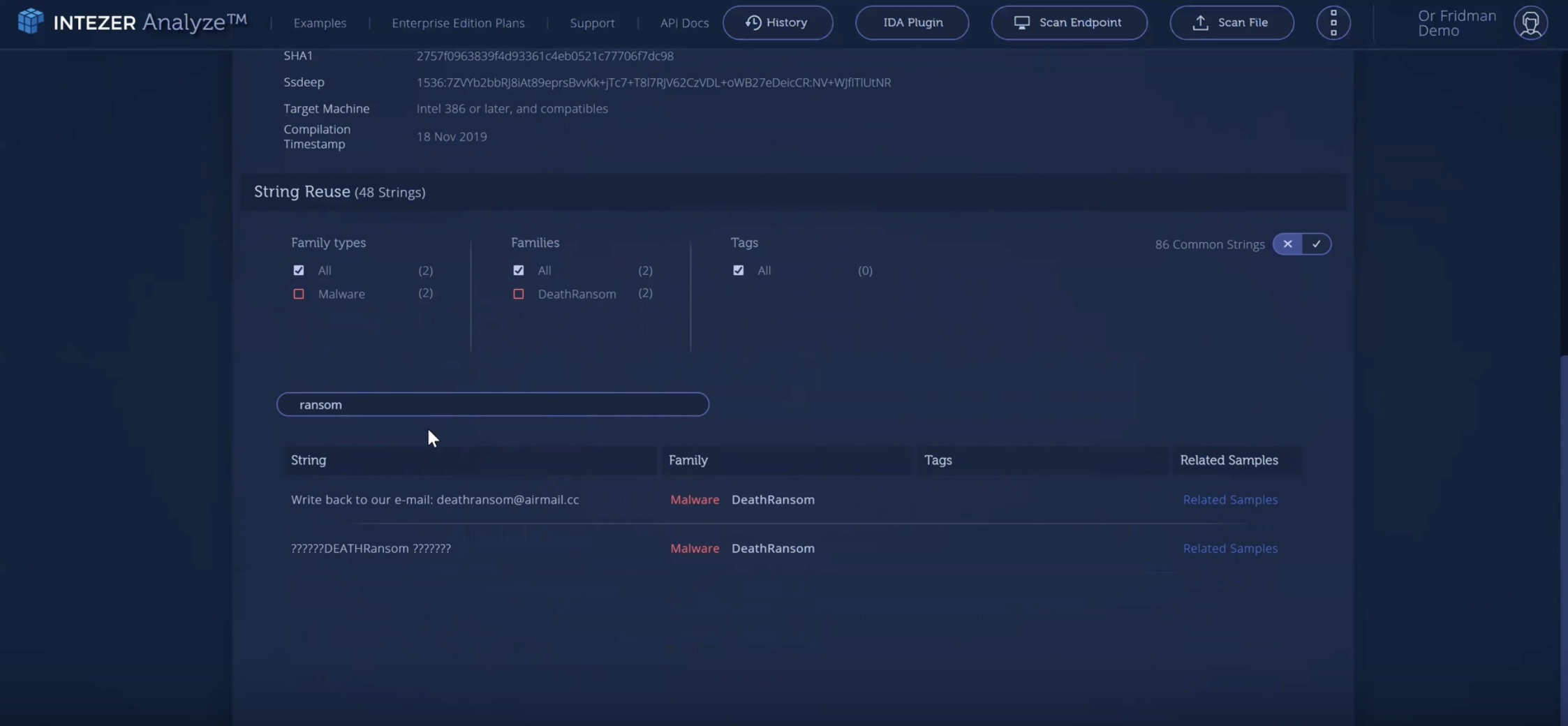
Revealing the Origins of Software with Genetic Analysis
When it comes to cyber attacks, running code is a crucial component. Whether it’s stealing data, installing a backdoor, or deleting sensitive materials, adversaries must execute code on a target’s […]