Danabot: Analyzing a fallen empire
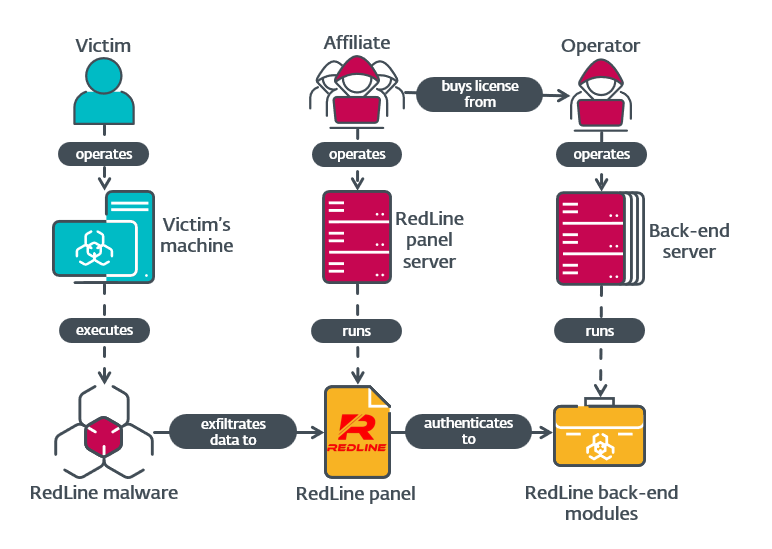
The US Department of Justice, along with the FBI and US DoD’s Defense Criminal Investigative Service (DCIS), successfully disrupted the infrastructure of the infamous infostealer, Danabot. ESET, among other cybersecurity […]