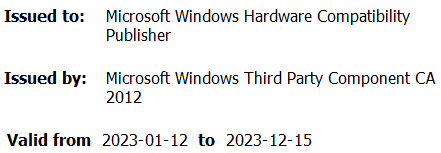
Story of a signed, vulnerable, ad-injecting driver
Malware research involves studying threat actor TTPs, mapping infrastructure, analyzing novel techniques… And while most of these investigations build on existing research, sometimes they start from a hunch, something that […]