Malware research involves studying threat actor TTPs, mapping infrastructure, analyzing novel techniques… And while most of these investigations build on existing research, sometimes they start from a hunch, something that looks too simple. At the end of 2023, we stumbled upon an installer named HotPage.exe that deploys a driver capable of injecting code into remote processes, and two libraries capable of intercepting and tampering with browsers’ network traffic. The malware can modify or replace the contents of a requested page, redirect the user to another page, or open a new page in a new tab based on certain conditions.
The installer was detected by most security products as an adware component but what really piqued our interest was the embedded driver signed by Microsoft. According to its signature, it was developed by a Chinese company named 湖北盾网网络科技有限公司 (machine translation: Hubei Dunwang Network Technology Co., Ltd), the lack of information about which was intriguing. The distribution method is still unclear but according to our research, this software was advertised as an “Internet café security solution” aimed at Chinese-speaking individuals. It purports to improve the web browsing experience by blocking ads and malicious websites, but the reality is quite different – it leverages its browser traffic interception and filtering capabilities to display game-related ads. It also sends some information about the computer to the company’s server, most likely to gather installation statistics.
On top of its obvious mischievous behavior, this kernel component unintentionally leaves the door open for other threats to run code at the highest privilege level available in the Windows operating system: the SYSTEM account. Due to improper access restrictions to this kernel component, any processes can communicate with it and leverage its code injection capability to target any non-protected processes.
We reported this driver to Microsoft on March 18th, 2024 and followed their coordinated vulnerability disclosure process. Microsoft Security Response Center (MSRC) determined that this is no longer a vulnerability as the offending driver was removed from the Windows Server Catalog on May 1st, 2024. ESET technologies detect this threat as Win64/HotPage.A and Win64/HotPage.B.
Who is 湖北盾网网络科技有限公司 ?
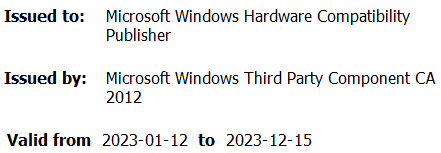
During its execution, the HotPage malware installs a driver, but before diving into the technical details of its inner workings, we wanted to learn more about the code-signing signature of this driver. What first caught our attention was the signing certificate’s owner, as illustrated in Figure 1.
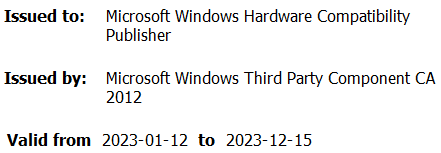
Since the 64-bit version of Windows 7, kernel-mode drivers have been required to be signed to be loaded by the operating system. As previously detailed by Mandiant Intelligence, SentinelLabs, and G DATA teams, the signing process is built on trust but there have been cases where this was abused. It seems that the Chinese company went through Microsoft’s driver code-signing requirements and managed to obtain an Extended Verification (EV) certificate as shown in Figure 2.
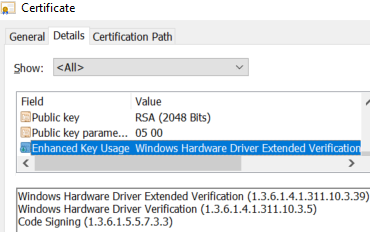
In order to retrieve the company name associated with this signature, the extraction of the signers’ attributes was necessary. Figure 3 shows the SpcSpOpusInfo attribute identified by the object ID 1.3.6.1.4.1.311.2.1.12.
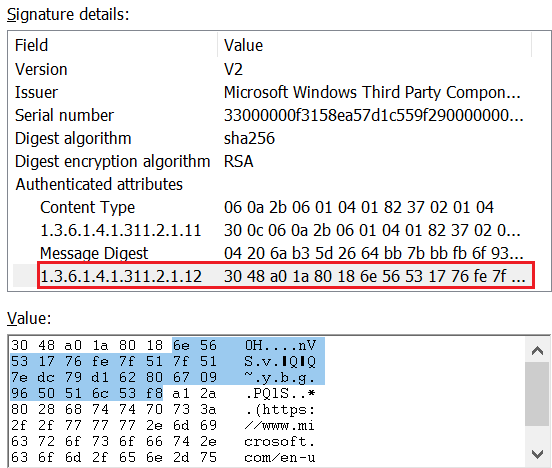
Using the LIEF binary parser, it is possible to extract the structure member programName that identifies the company behind this signature, as displayed in Figure 4.
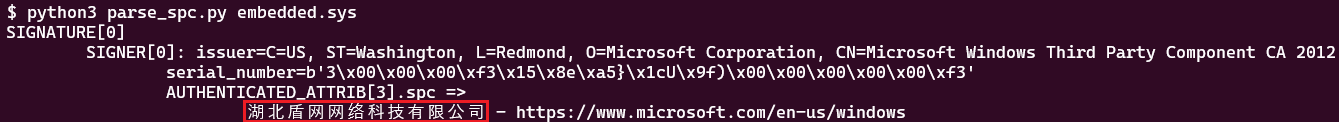
We found a reference to this company in the Windows Server Catalog, as shown in Figure 5. The company used various product categories when submitting its drivers for certification. Based on its name, it appears the company developed two network filtering programs: a netfilter component and the HotPage driver referred as adsafe or by its internal name KNewTalbeBase (Note the [Tt]albe typo, which also occurs elsewhere in the HotPage code).
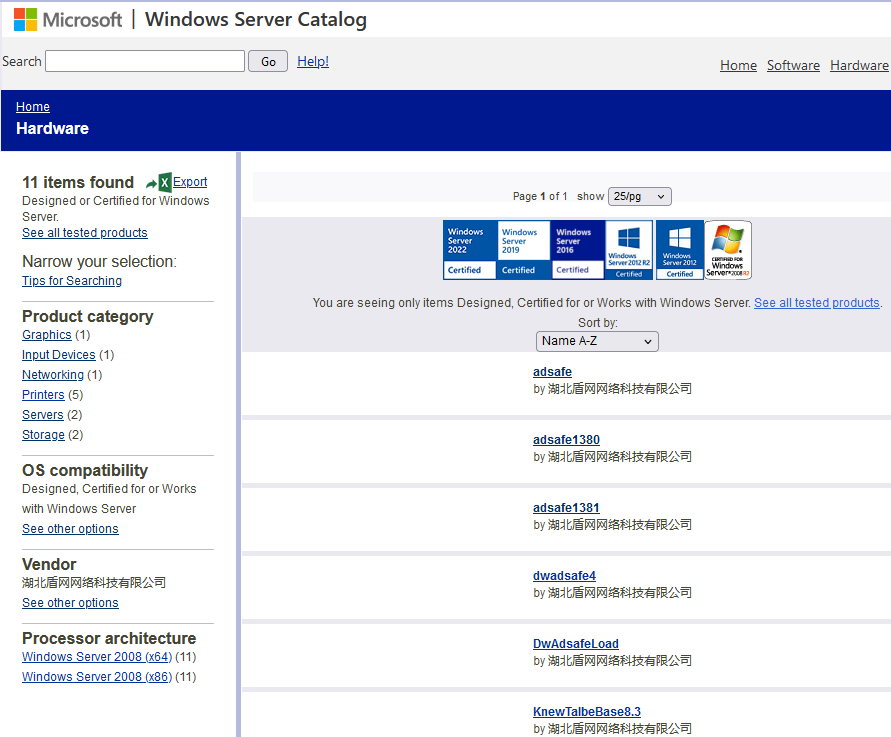
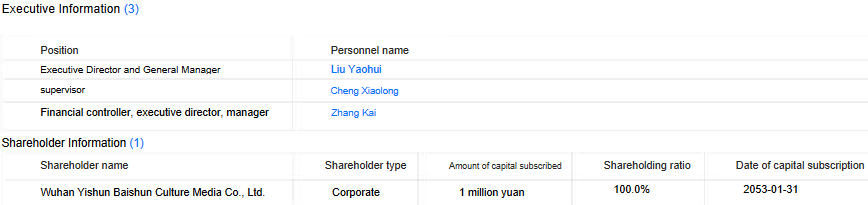
Investigating the company through search engines didn’t yield many results. According to the company register dingtalk, we discovered that the company was created on January 6th, 2022 and provided the email address dwadsafe@mail[.]io. The business scope includes: technology-related activities such as development, services, consulting, etc., but also advertising activities. As translated in Figure 6, the principal shareholder is now Wuhan Yishun Baishun Culture Media Co., Ltd, a very small company that looks to be specialized in advertising and marketing.
From the Intellectual Property tab, we learned that in April and May 2022 the company applied for the trade name Shield Internet Café Security Defense and the website dwadsafe[.]com was created on February 22nd, 2022. The domain now resolves to localhost (127.0.0.1) and is therefore inaccessible.
However, a web crawler captured a screenshot of the website on November 10th, 2023, as shown in Figure 7.
The HTTP body of the URL https://www.dwadsafe[.]com/login/reg.html (SHA-1: 744FFC3D8ECE37898A0559B62CC9F814006A1218) was also analyzed by VirusTotal. The source code revealed the description “网吧主动防御云平台” (machine translation: Internet café active defense cloud platform). The license agreement on the page outlined the purpose of the software, although it contained contradictions. Table 1 presents some noteworthy excerpts from that agreement.
According to the license agreement, the software is marketed as a security solution for internet cafés to block ads. Despite the company’s assertion that DwAdsafe lacks interception capabilities, our investigation found otherwise, with the software possessing intrusive features and pre-written, unchangeable rules.
The identity of the company behind this malicious component remains undisclosed.
HotPage Analysis
This section delves into the installation and interactions of different components to achieve the objective of injecting ads into the browser. The method of malware distribution remains unknown, but there is a tentative belief that it might have been bundled with another software package or falsely advertised as a security product due to the elevated privileges required to install the driver. References promoting the product were found in forums in 2022, as depicted in Figure 8.
The installer drops the driver on disk and initializes a service to run it. Upon decrypting the configuration file, a list of targeted Chromium-based browsers and libraries is revealed. The driver attempts to inject one of these libraries into the browser process when it detects the specified executables. Subsequently, the injected library intercepts network-based Windows API functions to monitor and, under certain conditions, display alternate pages to the user through various methods.
The installer (SHA-1: 941F0D2D4589FB8ADF224C8969F74633267B2561) is a UPX-compressed file containing encrypted versions of the driver component, libraries for injection into web browser processes, and JSON-formatted configuration files. These files detail the targeted browser libraries, hooking patterns, and filtering rules for the malware. The malware initiates by running the CPUID instruction to check for virtualization and proceeds to install the driver in a specified directory, creating a service to load it when required. Surprisingly, this adware does not include any persistence mechanisms, at least not in this version.
The installer proceeds to communicate with and configure the driver through its device filename using I/O control codes in the following sequence:
1. 0x9C4013FC – sends the 32-bit hooking library that will be injected into target web browser processes.
2. 0x9C400FFC – sends the 64-bit hooking library that will be injected into target web browser processes.
3. 0x9C40173C – sends the chromedll configuration.
The installer fetches the registry key linked to the created service and verifies if the values IP and port are present. Since these values are not set by this code, it is assumed that they are created by another component. Without delving into the specifics of the network protocol, the remote server is expected to provide an update of the newtalbe configuration. The communication is encrypted with RC4, utilizing a key derived from the string ID:f~WdH+K?KD)r*sD4mk using the Windows BCryptGenerateSymmetricKey function. Figure 10 displays the contents of the configuration file.
Table 2 outlines the significant values extracted from this file, listed in the order they appear in the configuration file (Figure 10).
Using the hostapi URL value from this file, an HTTP GET request is made over TLS with a generic User-Agent string. The received data is decrypted using RC4 with the hostapikey value, containing a dictionary of gaming-related hostnames with their corresponding resolved addresses.
Upon completion of these updates, the installer transmits the updated newtalbe configuration to the driver by issuing an I/O request with the control code 0x9C400BFC.
Lastly, the malware cycles through the list of endpoints provided by the JSON element apiurl, crafting a JSON-formatted string for each one containing details about the compromised computer, encrypting it with RC4 using the key Abc123!@#&XM derived via the Windows API BcryptGenerateSymmetricKey, and dispatching the collected information to the remote server through an HTTP POST request. This information comprises the computer name, network interface MAC address, operating system version, and screen dimensions. List of Available IOCTLs and Descriptions:
1. IOCTL: 0x9C400BFC
Action: Parses the newtable configuration passed as an argument.
2. IOCTL: 0x9C400FFC
Action: Sets the 64-bit library to be injected.
3. IOCTL: 0x9C4013FC
Action: Sets the 32-bit library to be injected.
4. IOCTL: 0x9C40173C
Action: Parses the chromedll configuration passed as an argument.
5. IOCTL: 0x9C401EC4
Action: Receives a list of browser tabs (processes) to kill.
6. IOCTL: 0x9C4027A8
Action: Returns the hotPage configuration.
7. IOCTL: 0x9C4027AC
Action: Returns the size of the hotPage configuration.
8. IOCTL: 0x9C4027E8
Action: Returns the newtable configuration.
9. IOCTL: 0x9C4027EC
Action: Returns the size of the newtable configuration.
10. IOCTL: 0x9C4027FC
Action: Parses the hotPage configuration passed as an argument.
Note: The hotPage configuration is not set in this software version; it is used to redirect users to specific pages filled with ads when a targeted browser is launched. The software primarily relies on the chromedll and newtable configurations for ad injection. Hook routine for NtDeviceIoControlFile API function
By inspecting incoming and outgoing data, the malware can manipulate traffic and perform various malicious activities. This includes redirecting users to fake websites, injecting ads, stealing sensitive information, and more. The ability to hook into and control the browser’s network traffic gives the attacker a powerful tool for carrying out their malicious intentions.
It is crucial for users to be aware of the risks associated with browsing the web and to take necessary precautions to protect themselves from such threats. This includes using reputable security software, keeping their browsers and operating systems up to date, and being cautious of the websites they visit and the links they click on.
To intercept the NtDeviceIoControlFile API function, the malware implements a hook routine that targets specific control codes for different actions.
For the control code 0x12023 (AFD_SEND_DATAGRAM used for sending UDP packets), the malware intercepts DNS requests by checking if the remote port number is 53. If the port number is 53, the malware returns STATUS_INVALID_PARAMETER to cancel the DNS request, ensuring that the web browser only uses hosts provided by the newtable configuration.
Another routine handles the control code 0x1201F (AFD_SEND) by extracting the URL and Referrer header from the request. Based on the URL matching values in the newtable and hotPage configurations, the malware performs various actions as described in Table 4. In some cases, the request is modified, and the response is further altered in the routine handling the AFD_RECV control code using different redirection methods explained later.
For control code 0x12017 (AFD_RECV), the malware retrieves data received by the client and checks if the response is eligible for redirection. There are four redirection methods described in Table 5, where certain strings in the modified response are replaced with URLs from the newtable configuration.
The malware also has security issues related to privilege escalation, as the driver’s device object lacks access control lists, allowing anyone to send I/O requests to it. The driver’s validation of the requesting process can be easily bypassed, potentially leading to unauthorized access. Two scenarios are outlined for privilege escalation, including arbitrary DLL injection in processes, exploiting the driver’s vulnerabilities to run code as the NT AUTHORITY\System account.
Overall, the malware’s hook routine for NtDeviceIoControlFile API function targets specific control codes to manipulate HTTP requests, perform actions based on configurations, and potentially exploit security vulnerabilities for privilege escalation. We developed a small library that logs the PID of the injected process, its administrator privileges status, and the file path of the injected process.
In Figure 20, the log file shows that many processes were injected using our library, including those with administrator privileges.
It’s important to note that protected processes cannot be injected using this method.
In another scenario, we found a way to escalate privileges by changing the command line of newly created processes. By leveraging the driver’s process creation and image loading notification routines, we were able to execute the same executable with a different command line.
The analysis of this malware has revealed the lengths adware developers will go to achieve their goals, including developing a kernel component with various techniques to manipulate processes. The HotPage driver highlights the risks associated with abusing Extended Verification certificates and the potential security vulnerabilities it introduces.
ESET technologies detect this threat as Win64/HotPage.A and Win64/HotPage.B. If you have any inquiries about our research, please contact us at threatintel@eset.com. ESET Research also offers private APT intelligence reports and data feeds. If you’re curious about this service, be sure to check out the ESET Threat Intelligence page for more information.
IoCs
If you’re looking for a detailed list of IoCs and samples, head over to our GitHub repository.
Files
|
SHA-1
|
Filename
|
Detection
|
Description
|
|
0D1D298A3EBCA4ECE0BA
|
N/A
|
Win64/HotPage.B
|
HotPage driver.
|
|
DDD82422D418FC8E8748
|
N/A
|
Win32/HotPage.B
|
32-bit HotPage hooking library.
|
|
D5D646B052E8B2572399
|
N/A
|
Win64/HotPage.A
|
64-bit HotPage hooking library.
|
|
941F0D2D4589FB8ADF22
|
Hotpage.exe
|
Win32/HotPage.A
|
HotPage installer.
|
Network
|
IP
|
Domain
|
Hosting provider
|
First seen
|
Details
|
|
61.147.93[.]49
|
nnijs-f-9-9-1.nycpqx[.]top
|
CHINATELECOM JiangSu YangZhou IDC.
|
2023-10-06
|
Server used to obtain a list of game-related domains with their corresponding IP addresses.
|
|
140.210.24[.]33
|
tmrr-s-f-9-9-1.vosdzxhbv[.]top
|
CHINATELECOM JiangSu YangZhou IDC.
|
2023-10-06
|
Compromised users are redirected to this web server that hosts ad-riddled pages.
|
|
202.189.5[.]222
|
N/A
|
Shandong eshinton Network Technology Co., Ltd.
|
2023-10-06
|
Former DwAdsafe domain used to collect information about installations.
|
MITRE ATT&CK techniques
If you’re interested in the MITRE ATT&CK techniques associated with this threat, take a look at the table below. This information is based on version 15 of the MITRE ATT&CK framework.
|
Tactic
|
ID
|
Name
|
Description
|
|
Resource Development
|
|
Obtain Capabilities: Code Signing Certificates
|
DwAdsafe’s driver is signed with a valid code-signing certificate.
|
|
Execution
|
|
User Execution: Malicious File
|
The installer component is an executable application.
|
|
|
System Services: Service Execution
|
DwAdsafe’s driver is loaded by creating a service.
|
|
|
Persistence
|
|
Hijack Execution Flow: KernelCallbackTable
|
DwAdsafe’s driver installs kernel callbacks to monitor loaded images and process creation.
|
|
Defense Evasion
|
|
Process Injection: Asynchronous Procedure Call
|
DwAdsafe’s driver can use APC as an injection method.
|
|
|
Subvert Trust Controls: Code Signing
|
DwAdsafe’s driver is signed with a valid code-signing certificate.
|
|
|
|
Deobfuscate/Decode Files or Information
|
The embedded configuration files are encrypted.
|
|
|
|
Process Injection: Dynamic-link Library Injection
|
DwAdsafe can hijack web browser processes’ control flow by injecting DLLs.
|
|
|
|
Obfuscated Files or Information: Embedded Payloads
|
DwAdsafe’s driver and hooking libraries are embedded inside the installer.
|
|
|
|
Indicator Removal: File Deletion
|
DwAdsafe’s driver deletes itself from disk.
|
|
|
|
Obfuscated Files or Information: Software Packing
|
DwAdsafe’s installer is packed with UPX.
|
|
|
Discovery
|
|
System Owner/User Discovery
|
DwAdsafe’s installer and the hooking libraries collect the victim’s username.
|
|
Collection
|
|
Browser Session Hijacking
|
DwAdsafe’s hooking libraries can intercept and tamper with network traffic inside web browser processes.
|
|
Command and Control
|
|
Application Layer Protocol: Web Protocols
|
The HTTP protocol is used to send collected information about the user and computer to the C&C.
|
|
|
Encrypted Channel: Symmetric Cryptography
|
The RC4 encryption algorithm is used for encrypting communication with the C&C.
|
|
|
Impact
|
|
Data Manipulation: Transmitted Data Manipulation
|
DwAdsafe’s hooking libraries can intercept and tamper with network traffic inside web browser processes.
|
original sentence: Please make sure to turn off the lights before leaving the room.
Rewritten sentence: Before you leave the room, be sure to turn off the lights. sentence: The cat was lying in the sun, purring contentedly. sentence:
The cat quickly ran across the yard.
The cat sprinted through the yard at high speed.