Discovery of Zero-Day Vulnerability Exploited by RomCom
ESET researchers recently uncovered a previously unknown vulnerability in Mozilla products that was being exploited in the wild by the Russia-aligned group RomCom. This marks the second instance of RomCom exploiting a significant zero-day flaw, following their abuse of CVE-2023-36884 through Microsoft Word in June 2023.
The critical vulnerability, identified as CVE-2024-9680 with a CVSS score of 9.8, enables malicious code execution in the restricted context of Firefox, Thunderbird, and the Tor Browser. When combined with another undisclosed Windows vulnerability, designated as CVE-2024-49039 with a CVSS score of 8.8, arbitrary code can be executed within the user’s logged-in session. This exploit resulted in the installation of RomCom’s backdoor on the victim’s device without requiring any user interaction.
Key Points:
- ESET researchers identified a zero-day vulnerability in Mozilla products on October 8th, 2024, exploited by RomCom.
- The vulnerability, now labeled as CVE-2024-9680, was promptly patched by Mozilla on October 9th, 2024.
- Further analysis revealed an undisclosed Windows vulnerability, referred to as CVE‑2024‑49039, which Microsoft addressed on November 12th, 2024.
- Successful exploitation led to the deployment of the RomCom backdoor in what appears to be a widespread campaign.
Insight into RomCom
Operating under aliases like Storm-0978, Tropical Scorpius, or UNC2596, RomCom is a Russian-affiliated group engaged in opportunistic attacks against various industry sectors and targeted espionage activities. Their operations now include both conventional cybercrime and espionage endeavors, with their backdoor capable of executing commands and downloading additional modules on compromised systems.
Our research outlines the sectors targeted by RomCom in 2024, revealing their dual focus on espionage and cybercrime:
Table 1. RomCom victims in 2024
| Vertical and Region | Purpose | First Seen |
| Governmental entity in Ukraine | Espionage | 2024-01 |
| Pharmaceutical sector in the US | Cybercrime | 2024-03 |
| Legal sector in Germany | Cybercrime | 2024-03 |
| Insurance sector in the US | Cybercrime | 2024-04 |
| Defense sector in Ukraine | Espionage | 2024-08 |
| Energy sector in Ukraine | Espionage | 2024-08 |
| Governmental entities in Europe | Espionage | 2024-08 |
| Worldwide targeting – Firefox exploit | Unknown | 2024-10 |
Compromise Chain Description
The compromise chain involves a deceptive website redirecting victims to an exploit server, triggering the execution of shellcode that downloads and runs the RomCom backdoor. The process is illustrated in Figure 1. Victims using vulnerable browsers are targeted through websites hosting the exploit, leading to the automatic execution of malicious code without user interaction.
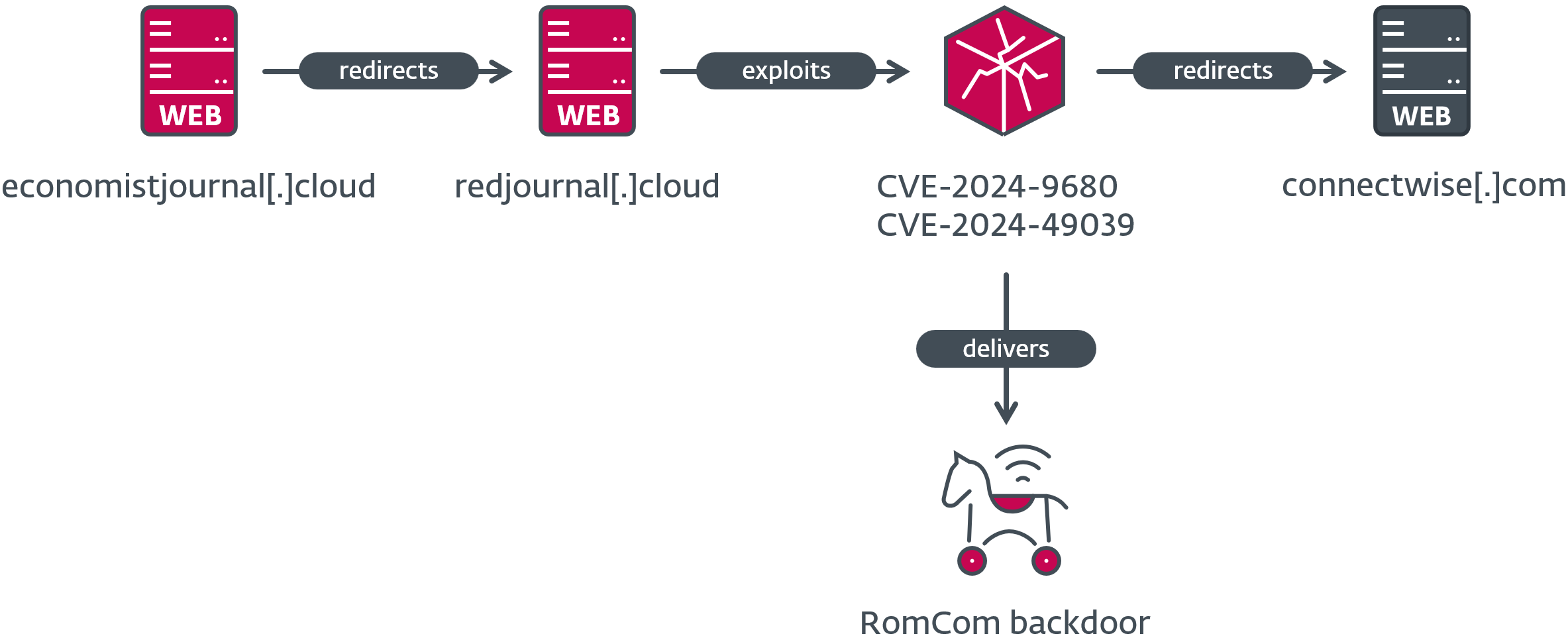
Between October 10th, 2024, and October 16th, 2024, after the initial vulnerability was patched, additional exploit servers were discovered hosting the attack. These servers utilized a consistent naming convention by adding prefixes or suffixes like redir or red to legitimate domains, sometimes altering the top-level domain (TLD). The purpose was to redirect victims to the original domain after successful exploitation, minimizing suspicion.
Table 2. Fake servers redirecting to the exploit
| First Seen | Fake Server | Final Redirect | Redirect Website Purpose |
| 2024-10-10 | redircorrectiv[.]com | correctiv.org | Nonprofit independent newsroom |
| 2024-10-14 | devolredir[.]com | devolutions.net | Remote access and password management solutions |
| 2024-10-15 | redirconnectwise[.]cloud | connectwise.com | MSP technology and IT management software |
| 2024-10-16 | redjournal[.]cloud | connectwise.com | MSP technology and IT management software |
Visiting a site serving the exploit triggers the vulnerability, executing shellcode in a content process. The shellcode consists of two parts: the initial component retrieves the subsequent part from memory and designates the containing pages as executable, while the latter implements a PE loader using Shellcode Reflective DLL Injection (RDI).
The injected library facilitates a sandbox escape in Firefox, leading to the download and execution of the RomCom backdoor from C&C servers like journalctd[.]live, correctiv[.]sbs, or cwise[.]store, depending on the specific sample.
Telemetry data indicates that between October 10th, 2024, and November 4th, 2024, potential victims of this exploit were predominantly located in Europe and North America, as depicted in Figure 2. The number of targeted individuals varied across countries, with ESET telemetry recording anywhere from a single victim to 250 potential targets per country.
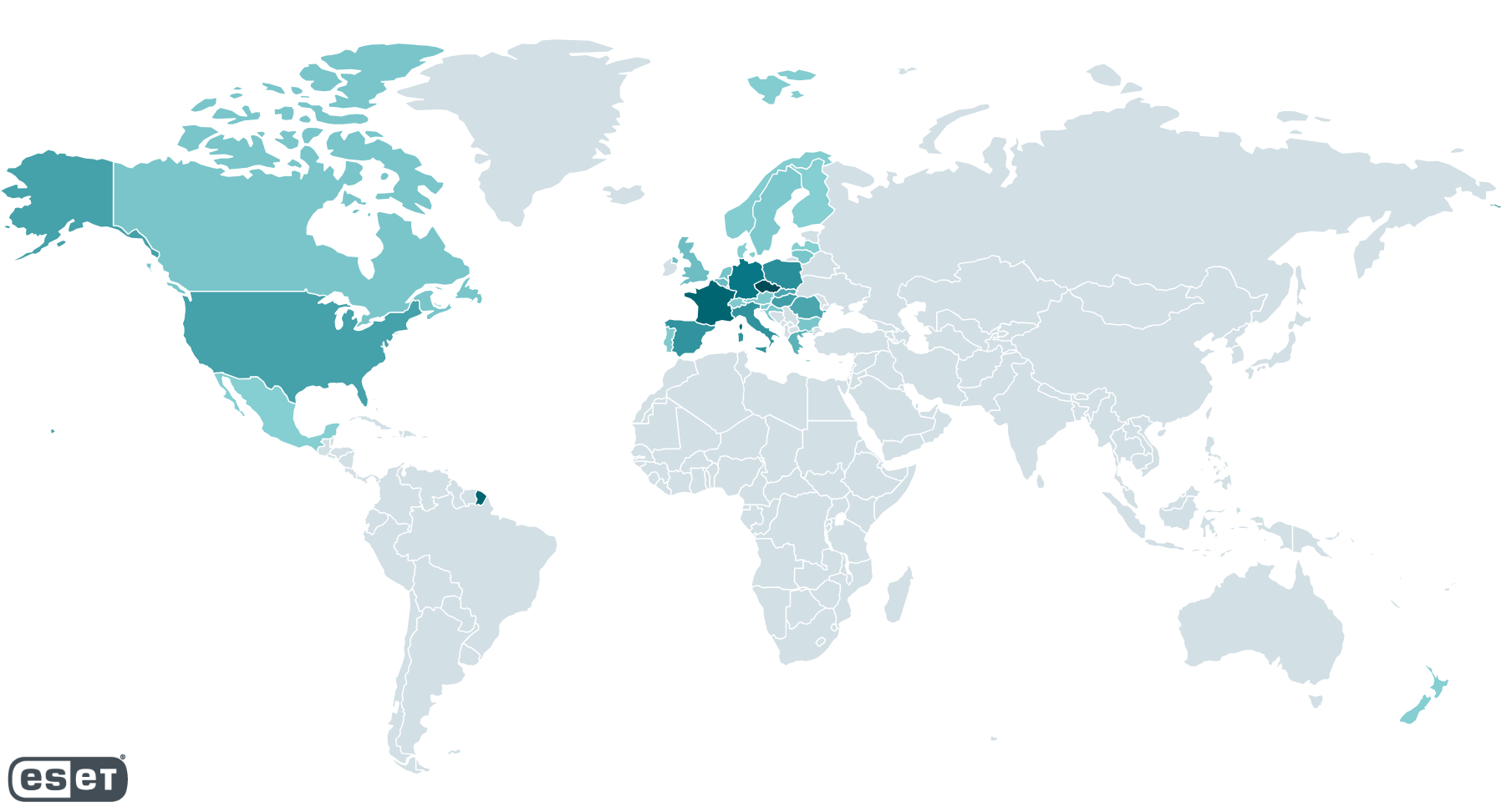
Heatmap of potential victims
On October 8th, 2024, we discovered files on the server 1drv.us[.]com that were used to distribute the RomCom backdoor. These files exploited a vulnerability in Firefox animation timelines, known as a use-after-free vulnerability, which allowed attackers to execute code within a content process. Our investigation focused on analyzing the files listed in Table 3.
Table 3. Files associated with the exploit
| Name | Description |
| main-128.js | Contains the exploit for Firefox versions 106 to 128. |
| main-129.js | Contains the exploit for Firefox versions 129 to 131. |
| main-tor.js | Contains the exploit for Tor Browser versions 12 and 13. |
| script.js | Generates a CAPTCHA using JavaScript. |
| utils.js | Contains helper functions for data type conversion, OS type retrieval, and browser version identification. |
| animation0.html | HTML iframe used to trigger the use-after-free vulnerability. |
| index.html | HTML page that loads the exploit and redirects to a legitimate website after a few seconds. |
Timestamps indicate that these files were created on October 3rd, 2024 and made available online. However, the threat actor may have possessed this exploit earlier.
After discovering the vulnerability, we promptly reported it to Mozilla, leading to the following sequence of events:
- 2024-10-08: Discovery and initial analysis.
- 2024-10-08: Vulnerability reported to Mozilla.
- 2024-10-08: Vulnerability acknowledged by Mozilla.
- 2024-10-09: Mozilla Corporation assigns CVE-2024-9680.
- 2024-10-09: Firefox patched the vulnerability in Security Advisory 2024-51.
- 2024-10-09: Tor Browser patched the vulnerability with release 13.5.7.
- 2024-10-10: Tails patched the vulnerability with release 6.8.1.
- 2024-10-10: Thunderbird patched the vulnerability in Security Advisory 2024-52.
We express our gratitude to Mozilla for their swift response and commendable efforts in issuing a patch within a day.
Mozilla and the Tor Project released patches for the vulnerability in the following versions:
- Firefox 131.0.2
- Firefox ESR 115.16.1
- Firefox ESR 128.3.1
- Tor Browser 13.5.7
- Tails 6.8.1
- Thunderbird 115.16
- Thunderbird 128.3.1
- Thunderbird 131.0.1
Additionally, independent researcher Dimitri Fourny published a detailed analysis of the vulnerability on November 14th, 2024, during the preparation of this blogpost.
Root cause analysis
The main-<Firefox version>.js file checks the browser version and specific object properties to determine exploitability. Upon meeting certain criteria, it adds an HTML iframe to the exploit page in animation0.html. This script creates HTML div elements and defines a getter function for the Object.prototype‘s then property, which triggers the use-after-free vulnerability.
Following heap spraying, the prepare function generates Animation objects for each previously created div element. These animation objects are managed by an AnimationTimeline object.
During the document animation timeline, the test function accesses the ready property of animation objects, triggering the use-after-free vulnerability through the getter function defined earlier. This ultimately leads to the exploitation of the vulnerability.
This function also performs heap feng shui and, in the initial exploit, calls the getInfo function responsible for achieving code execution.
Meanwhile, while the animation0.html document is being refreshed, the Tick method of its AnimationTimeline object is called periodically. This method iterates over the different animation objects present in the animation timeline and appends animations to be removed to a local array variable called animationsToRemove.
The bug occurs when the Tick method of the Animation object is called while iterating over the different animation objects of the animation timeline, which can lead to handling a dangling pointer. This sequence of calls eventually ends up in the getter function, as shown in Figure 6 and Figure 7.
The getter function calls Animation::Cancel, which then calls AnimationTimeline::RemoveAnimation. This manipulation of a dangling pointer of an Animation object that was already removed leads to a crash in AnimationTimeline::RemoveAnimation, as depicted in Figure 8.
After freeing the animations in the rm0 function, the exploit proceeds with more heap management to control the objects that will replace the freed animations, and finally, the getInfo function is called, as seen in Figure 9.
The exploit code abuses div objects and their attributes as well as ImageData objects to leak properties of the latter, as observed in Figure 10.
Next, the exploit code manipulates ArrayBuffer objects to leak the address of an arbitrary JavaScript object and abuse the Firefox JIT compiler to execute shellcode in the context of a content process, as illustrated in Figure 11.
Mozilla patched the vulnerability in Firefox 131.0.2, Firefox ESR 128.3.1, and Firefox ESR 115.16.1 on October 9th, 2024, by implementing reference-counting pointers to prevent animations from being freed.
Shellcode analysis
Both shellcodes are stored in the JavaScript exploit file main-
Egghunting shellcode
This first shellcode retrieves the second shellcode by searching in memory for a hardcoded magic value, changes its memory protection to read-write-execute (RWX), and executes the code located at this address.
Reflective loader shellcode
The second shellcode is the compiled version of the Shellcode RDI project, which allows a DLL to be loaded. The constants used in the shellcode were not changed by the threat actor, as shown in Figure 12. The constants utilized in the public Shellcode RDI project remained unaltered. The level of sophistication displayed by the threat actor demonstrates their determination and resources to acquire or develop stealthy capabilities. ESET promptly shared detailed findings with Mozilla through our coordinated vulnerability disclosure process. Mozilla then published a blogpost detailing their response to the disclosure and successfully implemented a fix within just 25 hours, a remarkable achievement compared to industry norms. For further information on our research featured on WeLiveSecurity, please reach out to us at threatintel@eset.com. ESET Research also provides private APT intelligence reports and data feeds. If you’re curious about this service, why not head over to the ESET Threat Intelligence page for more details?
IoCs
If you’re looking for indicators of compromise and samples, you can find a detailed list in our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| A4AAD0E2AC1EE0C8DD25 |
utils.js | JS/Exploit.Agent.NSF | RomCom Firefox exploit. |
For a visual representation and more information, feel free to check out the 
sentence in a passive voice.
The teacher assigned the homework to the students.
The homework was assigned to the students by the teacher. sentence using different words:
Original sentence: The cat sat lazily in the sun.
Rewritten sentence: The feline lounged idly in the sunlight. text in a clear, concise manner.



