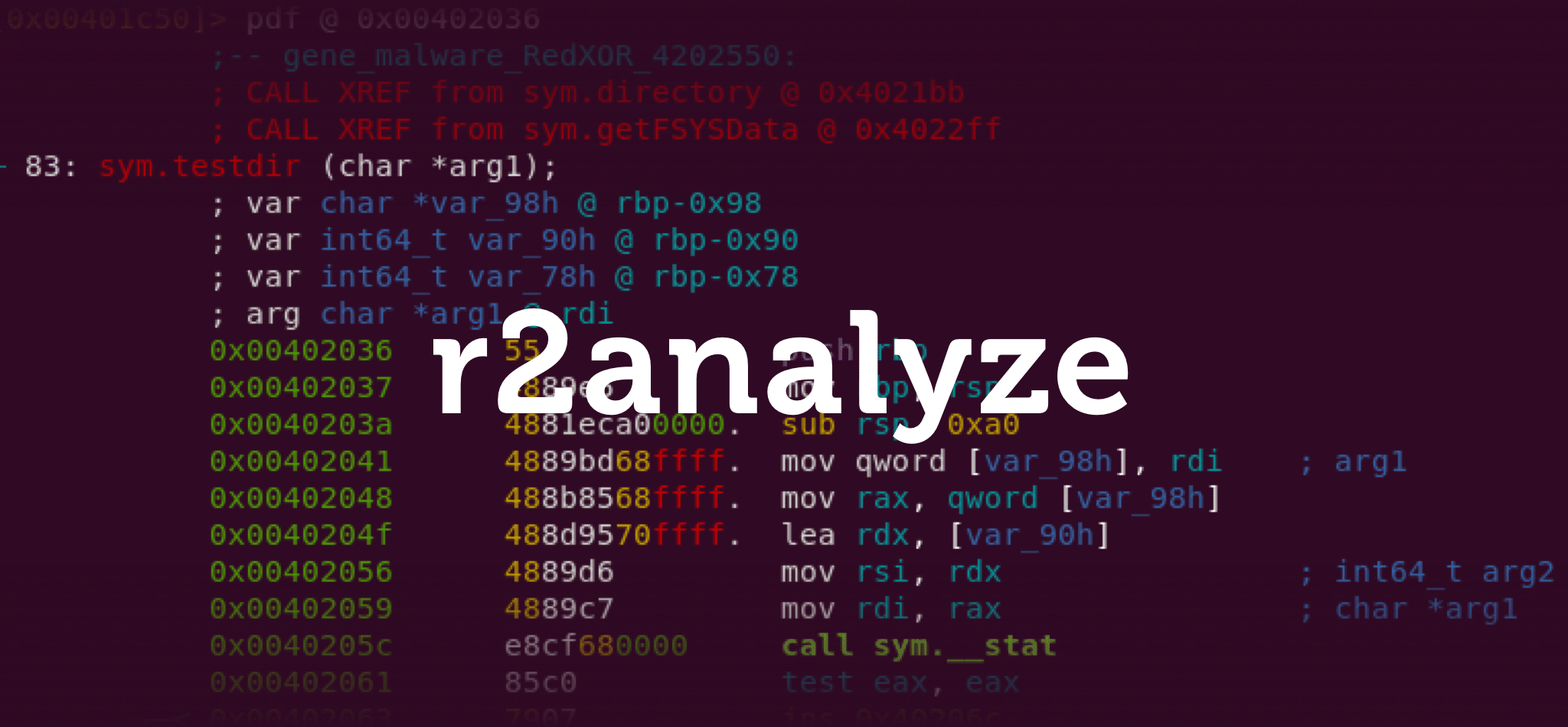
When you find yourself reverse engineering code as part of an incident response team, your main goal is to quickly gather information about the type of threat you are facing.
Some time ago, we introduced Intezer Analyze plugins for both IDA Pro and Ghidra to help you pinpoint a file’s malicious and distinctive code. Now, it’s Radare’s turn. Radare2 (r2) is an open-source tool chain designed for reverse engineering and forensics. With the launch of the community plugin r2analyze, Radare2 users can now enhance their reverse engineering process with code genomics from Intezer to attribute the malware family or threat actor.
The Radare Plugin for Reverse Engineering
Here’s how you can get started:
- Ensure you have an Intezer Analyze community account or a paid team account. (If not, register here.)
- Submit the file to Intezer Analyze.
- Install the plugin via pip:
pip install r2analyze. - Add your API key as an environment variable named INTEZER_API_KEY.
- Open the file in Radare2 and conduct an initial analysis (aaa).
- Execute the plugin as a Radare2 pipe command (
#!pipe r2analyze).
For example, let’s take a look at a ScarCruft sample (7c82689142a415b0a34553478e445988980f48705735939d6d33c17e4e8dac94). The Intezer Analyze result is displayed below.
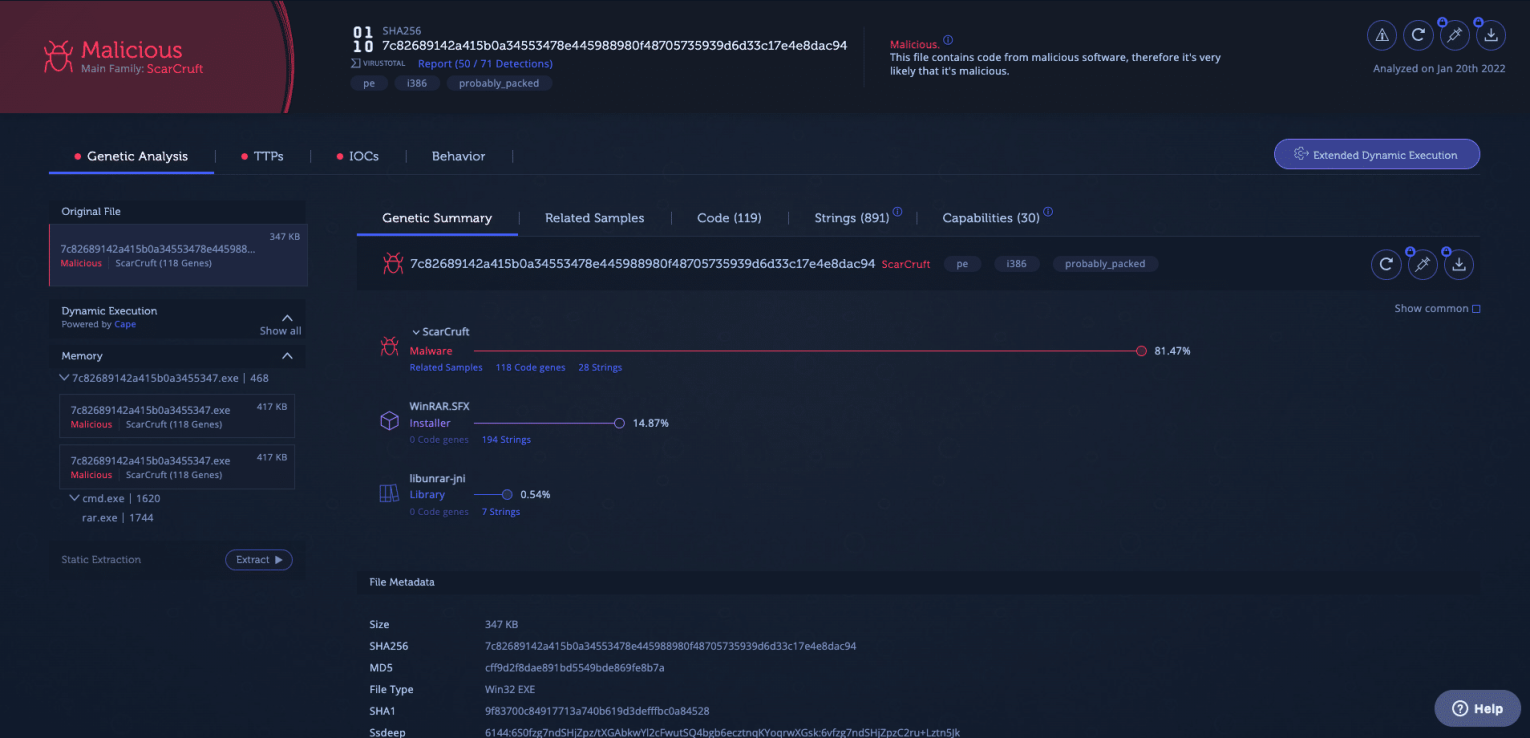
Upon opening the sample and running the plugin, you will see that four items in the flag space named gene have been generated.

If you select only that flag space and list all the flags, you will see that four functions have been identified as unique to ScarCruft.
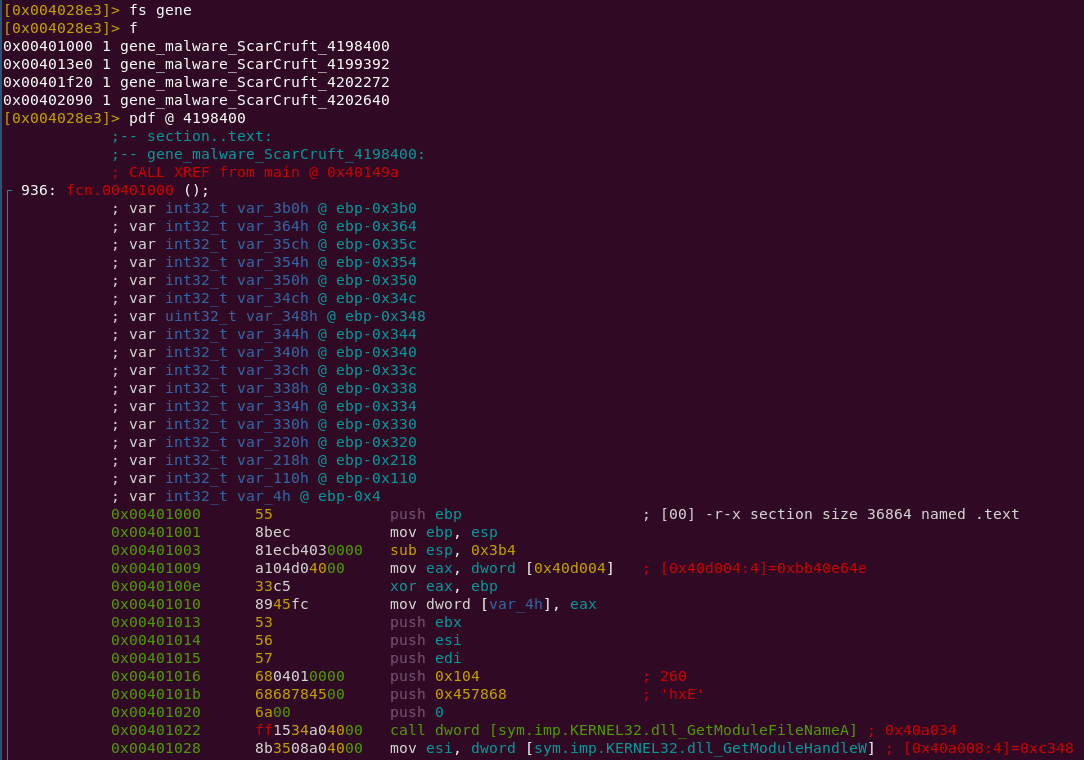
If Radare2 is your preferred framework for reverse engineering and binary analysis, you can now utilize this Intezer Analyze plugin to save time and gain additional insights for your incident response team.
Intezer automates the malware analysis process to swiftly identify and classify malware families. Analyze malware and unknown files for free at analyze.intezer.com
Additional Resources