ESET researchers provide details on a previously undisclosed China-aligned APT group that we track as PlushDaemon and one of its cyberespionage operations: the supply-chain compromise in 2023 of VPN software developed by a South Korean company, where the attackers replaced the legitimate installer with one that also deployed the group’s signature implant that we have named SlowStepper – a feature-rich backdoor with a toolkit of more than 30 components.
Key points of this blogpost:
- PlushDaemon is a China-aligned threat group, engaged in cyberespionage operations.
- PlushDaemon’s main initial access vector is hijacking legitimate updates of Chinese applications, but we have also uncovered a supply-chain attack against a South Korean VPN developer.
- We believe PlushDaemon is the exclusive user of several implants, including SlowStepper for Windows.
- SlowStepper has a large toolkit composed of around 30 modules, programmed in C++, Python, and Go.
Overview
In May 2024, we noticed detections of malicious code in an NSIS installer for Windows that users from South Korea had downloaded from the website of the legitimate VPN software IPany (https://ipany.kr/; see Figure 1), which is developed by a South Korean company. Upon further analysis, we discovered that the installer was deploying both the legitimate software and the backdoor that we’ve named SlowStepper. We contacted the VPN software developer to inform them of the compromise, and the malicious installer was removed from their website.
We attribute this operation to PlushDaemon – a China-aligned threat actor active since at least 2019, engaging in espionage operations against individuals and entities in China, Taiwan, Hong Kong, South Korea, the United States, and New Zealand. PlushDaemon uses a custom backdoor that we track as SlowStepper, and its main initial access technique is to hijack legitimate updates by redirecting traffic to attacker-controlled servers. Additionally, we have observed the group gaining access via vulnerabilities in legitimate web servers.
The victims appear to have manually downloaded a ZIP archive containing a malicious NSIS installer from the URL https://ipany[.]kr/download/IPanyVPNsetup.zip. We found no suspicious code on the download page (shown in Figure 1) to produce targeted downloads, for example by geofencing to specific targeted regions or IP ranges; therefore, we believe that anyone using the IPany VPN might have been a valid target.
Via ESET telemetry, we found that several users attempted to install the trojanized software in the network of a semiconductor company and an unidentified software development company in South Korea. The two oldest cases registered in our telemetry were a victim from Japan in November 2023, and a victim from China in December 2023.
Technical analysis
As illustrated in Figure 2, when the malicious IPanyVPNsetup.exe installer is executed, it creates several directories and deploys both legitimate and malicious files.
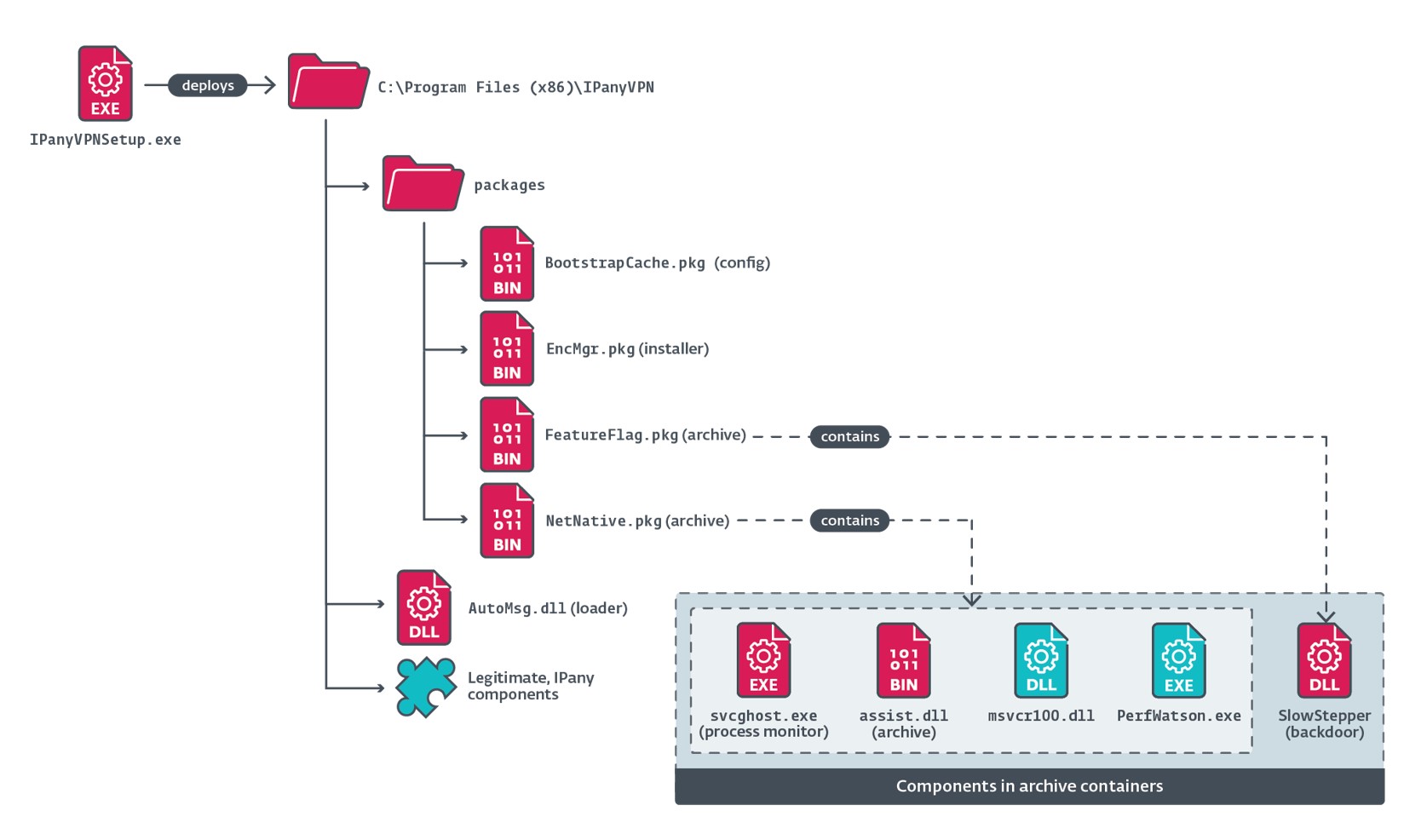
Additionally, the installer establishes persistence for SlowStepper by adding an entry named IPanyVPN to a Run key, with the value %PUBLIC%\Documents\WPSDocuments\WPSManager\svcghost.exe, so that the malicious component svcghost.exe (later extracted and deployed by the loader in EncMgr.pkg) is launched when the operating system starts.
The first malicious component that is loaded by the installer is the AutoMsg.dll loader. Figure 3 illustrates the major steps taken during the execution of this component.
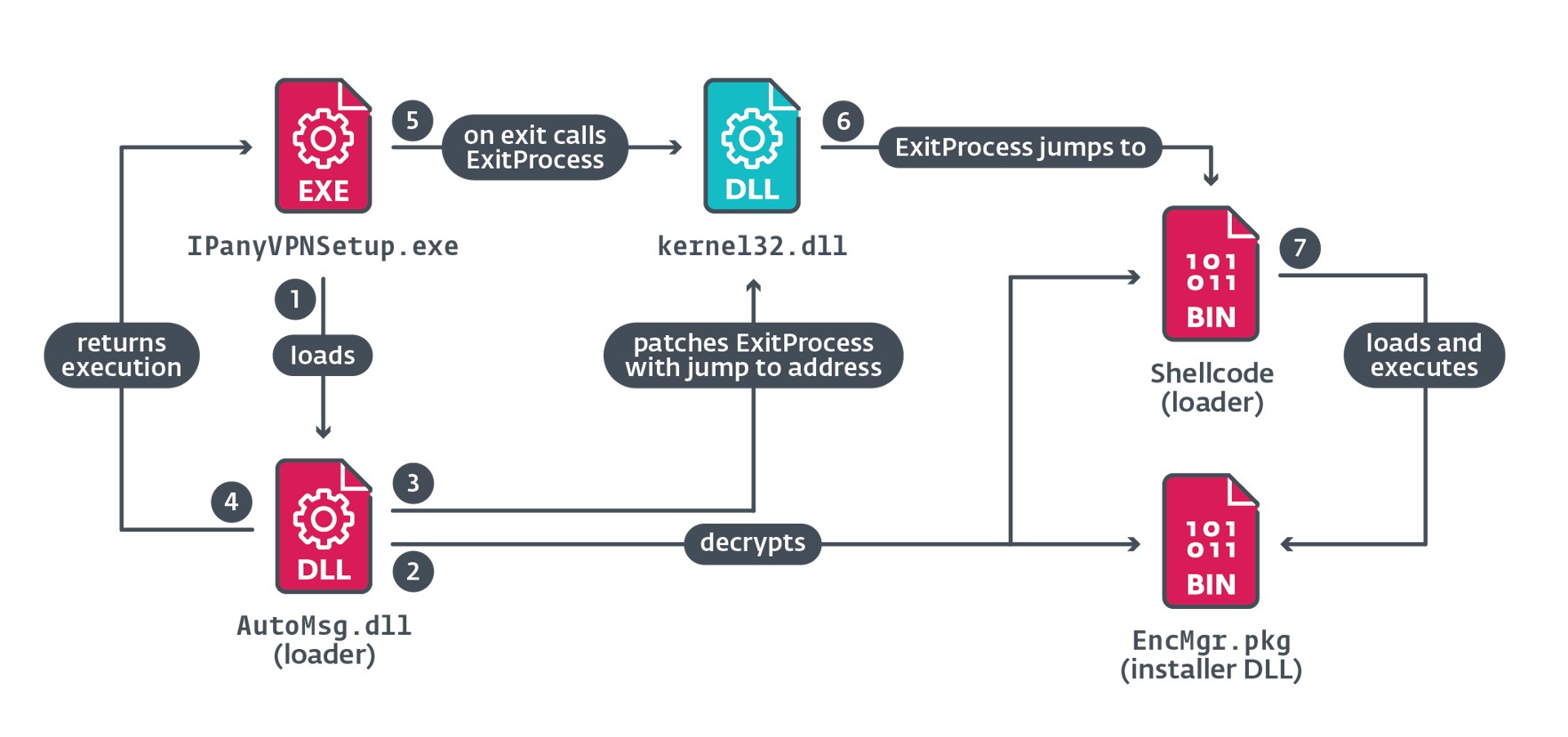
When IPanyVPNSetup.exe calls ExitProcess, the patched bytes redirect execution to the shellcode that loads EncMgr.pkg into memory and executes it.
EncMgr.pkg creates two directories – WPSDocuments and WPSManager – in %PUBLIC%\Documents and the deployment begins by extracting components from the custom archives NetNative.pkg and FeatureFlag.pkg. The components are dropped to disk and moved to other locations with new filenames. The sequence and actions taken are as follows:
1. Extracts the files from NetNative.pkg to:
a. %PUBLIC%\Documents\WPSDocuments\WPSManager\assist.dll,
b. %PUBLIC%\Documents\WPSDocuments\WPSManager\msvcr100.dll,
c. %PUBLIC%\Documents\WPSDocuments\WPSManager\PerfWatson.exe, and
d. %PUBLIC%\Documents\WPSDocuments\WPSManager\svcghost.exe.
2. Deletes NetNative.pkg.
3. Moves FeatureFlag.pkg to C:\ProgramData\Microsoft Shared\Filters\SystemInfo\winlogin.gif.
4. Moves assist.dll to C:\ProgramData\Microsoft Shared\Filters\SystemInfo\Winse.gif.
5. Extracts file from Winse.gif to %PUBLIC%\Documents\WPSDocuments\WPSManager\lregdll.dll.
6. Copies data from BootstrapCache.pkg to %PUBLIC%\Documents\WPSDocuments\WPSManager\Qmea.dat.
Its last actions are to execute svcghost.exe using the ShellExecute API and then exit.
The svcghost.exe component performs monitoring of the PerfWatson.exe process, where the backdoor is loaded, ensuring that it is always running. If the processes are not running, it executes PerfWatson.exe (originally a legitimate command line utility named regcap.exe, included in Visual Studio), which the attackers abuse to side-load lregdll.dll.
The DLL aims to load the SlowStepper backdoor from the winlogin.gif file.
To achieve this goal, it creates a nameless window on a new thread that selectively responds to messages like WM_CLOSE, WM_QUERYENDSESSION, and WM_ENDSESSION. Upon receiving any of these messages, the thread attempts to establish persistence in the Windows registry based on the current process permissions. The targeted registry keys for persistence are listed in Table 1.
The SlowStepper backdoor is a C++ developed backdoor that utilizes object-oriented programming in its C&C communications code. The backdoor is available in both Lite and full versions, with the Lite version, used in the IPany VPN software compromise, having fewer features compared to other versions. The backdoor’s code contains various functions, with the oldest version being 0.1.7 and the newest being 0.2.12.
The backdoor communicates with its C&C server by crafting a DNS query to obtain a TXT record for the domain 7051.gsm.360safe[.]company. The backdoor then connects to the C&C server using TCP based on the extracted IP addresses from the DNS query. If connection attempts fail, it falls back to using the domain st.360safe[.]company to obtain the IP address. SlowStepper supports various commands for collecting information and executing actions on the compromised machine, as listed in Table 3. Execution of tools via SlowStepper’s pycall shell command
Figure 6 illustrates the flow of execution when the operator issues a pycall command to execute a Python module on the compromised machine, such as the CollectInfo module.
From the remote repository, the pycall command downloads a ZIP archive containing the Python interpreter and supporting libraries. Depending on the conditions outlined in Table 5, one of three customized Python distributions is downloaded.
Table 5: List of customized Python distributions and download conditions
| Condition | Archive name | Description |
|————————————————————–|————————-|——————–|
| Windows operating system is XP | winxppy.org | Python 3.4 |
| All required Windows API set DLLs and Microsoft C runtime present | winpy_no_rundll.org | Python 3.7 |
| Neither of the above conditions are met | win7py.org | Python 3.7 with necessary DLLs and runtime library |
Figure 7 displays the directory structure of the decompressed archive containing the customized Python distribution, showcasing only the malicious files included. Directory structure of the customized Python distribution and malicious files:
Root Directory:
- Python:
- Pythonw.exe
- runas.py
- help.py
- Modules:
- abc.py
- Browser.py
- Camera.py
- CollectInfo.py
- Decode.py
- DingTalk.py
- Download.py
- FileScanner.py
- FileScannerAllDisk.py
- getOperaCookie.py
- list.py
- Location.py
- Location1.py
- LocationByIP.py
- PackDir.py
- qpass.py
- qqpass.py
- ScreenRecord.py
- Telegram.py
- Webpass.py
- WeChat.py
- WeChat_all_file.py
- WeChat_src.py
- Wechat1.py
- WechatFile.py
- WirelessKey.py
Other Tools:
- C/C++ Tools:
- Tool1.exe
- Tool2.exe
- Go Tools:
- Tool3.go
- Tool4.go
Tools and their Functions
| Tool Filename | Description |
| agent.mod | A reverse proxy programmed in Go. |
|
getcode.mod getcode64.mod
|
Mimikatz. This tool is a DLL downloaded by the getpwd command. |
| InitPython.mod | An old downloader used to install a customized Python distribution on the compromised machine. This tool is a DLL. |
| Remote.mod | A RealVNC server that allows attackers to remotely control the compromised machine. This tool is a DLL. |
| soc.mod |
A reverse proxy programmed in Go. Signed with a certificate from a Chinese company called Hangzhou Fuyang Qisheng Information Technology Service Department. Limited information is available about the company.
|
| stoll.mod |
A tool used for downloads, written in Go. Signed with a certificate from the Chinese company Zhoushan Xiaowen Software Development Studio. Limited information is available about the company.
|
Please rewrite the sentence so that I can help you. following sentence: “The cat sat lazily in the sun, enjoying the warmth on its fur.”
“The cat lounged in the sun, relishing the cozy feeling on its fur.” sentence in your own words to show your understanding:
Sure! Just provide me with the sentence you would like me to rewrite. sentence: Can you please close the window before you leave? phrase: “The quick brown fox jumps over the lazy dog.”
Rewritten phrase: “The speedy brown fox leaps over the lethargic dog.” sentence.
The cat chased the mouse around the house.
The mouse was chased by the cat all over the house.