ESET researchers uncovered a crimeware campaign that targeted clients of three Czech banks. The malware used, which we have named NGate, has the unique ability to relay data from victims’ payment cards, via a malicious app installed on their Android devices, to the attacker’s rooted Android phone.
Key points of this blogpost:
- Attackers combined standard malicious techniques – social engineering, phishing, and Android malware – into a novel attack scenario; we suspect that lure messages were sent to random phone numbers and caught customers of three banks.
- According to ESET Brand Intelligence Service data, the group has operated since November 2023 in Czechia, using malicious progressive web apps (PWAs) and WebAPKs. In March 2024 the group’s technique improved by deploying the NGate Android malware.
- Attackers were able to clone NFC data from victims’ physical payment cards using NGate and relay this data to an attacker device that was then able to emulate the original card and withdraw money from an ATM.
- This is the first time we have seen Android malware with this capability being used in the wild.
- Victims didn’t have to root their devices.
The primary goal of this campaign is to facilitate unauthorized ATM withdrawals from the victims’ bank accounts. This was achieved by relaying the near field communication (NFC) data from the victims’ physical payment cards, via their compromised Android smartphones by using the NGate Android malware, to the attacker’s device. The attacker then used this data to perform ATM transactions. If this method failed, the attacker had a fallback plan to transfer funds from the victims’ accounts to other bank accounts.
We haven’t seen this novel NFC relay technique in any previously discovered Android malware. The technique is based on a tool called NFCGate, designed by students at the Technical University of Darmstadt, Germany, to capture, analyze, or alter NFC traffic; therefore, we named this new malware family NGate.
Overview
Victims downloaded and installed the malware after being deceived into thinking they were communicating with their bank and that their device was compromised. In reality, the victims had unknowingly compromised their own Android devices by previously downloading and installing an app from a link in a deceptive SMS message about a potential tax return. A short description of this attack is available in the video below.
It’s important to note that NGate was never available on the official Google Play store.
NGate Android malware is related to the phishing activities of a threat actor that operated in Czechia since November 2023. However, we believe these activities were put on hold following the arrest of a suspect in March 2024.
We first noticed the threat actor targeting clients of prominent Czech banks starting at the end of November 2023. The malware was delivered via short-lived domains impersonating legitimate banking websites or official mobile banking apps available on the Google Play store, as illustrated in Figure 1. These fraudulent domains were identified through the ESET Brand Intelligence Service, which provides monitoring of threats targeting a client’s brand. During the same month, we reported our findings to our clients.
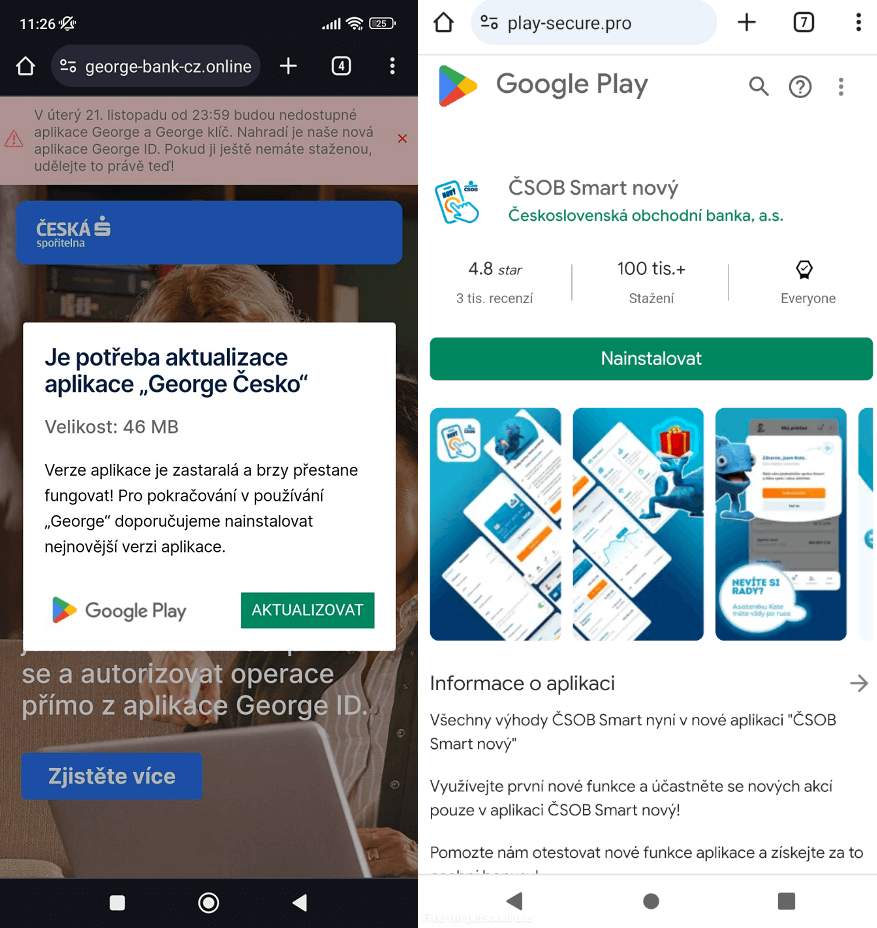
Victimology
During our investigation, we identified six different NGate apps specifically targeting clients of three banks in Czechia between November 2023 and March 2024.
In a substantial breakthrough, the Czech police apprehended a 22-year-old, who had been stealing money from ATMs in Prague. Upon arrest, the suspect had 160,000 Czech korunas in his possession, an amount equivalent to over 6,000 euros (approximately US$6,500). The nationality of the arrested individual has not been disclosed. According to the Czech police, the money recovered from the suspect was stolen from just the last three victims, so it is likely that the total amount stolen by the threat actor behind this scheme is considerably higher.
Evolution of attack scenarios
The attackers leveraged the potential of progressive web apps (PWAs), only to later refine their strategies by employing a more sophisticated version of PWAs known as WebAPKs. Eventually, the operation culminated in the deployment of NGate malware.
It is important to note that in all of the attack scenarios described here, the victim’s device doesn’t need to be rooted, only the attacker’s device that emulates the received NFC traffic.
Progressive web apps
Initially, these fraudulent websites misused PWA technology. This technology allows a user to install an app from a website via a supported browser; the installation can be triggered either automatically through a pop-up notification or manually by selecting the Install app option from the browser’s menu. On Android, supported browsers include Chrome, Firefox, Edge, and Opera. Once installed, a new icon featuring a small browser logo in the bottom right corner is added to the smartphone’s home screen, basically serving as a website link. An example is shown in Figure 2, where we compare the icon of a PWA on the left side with an icon of a standard app on the right side.

PWAs are essentially a type of app, but unlike traditional apps that are downloaded and installed from an app store, PWAs are accessed and used directly within a web browser. They are built using common web programming languages such as HTML (for structure), CSS (for design), and JavaScript (for interactivity), which are the same technologies used to create websites. PWAs are known for their compatibility and flexibility, as they are designed to work on any device that has a standards-compliant web browser.
This implies that a user can access the same PWA on various devices, such as desktop computers, laptops, tablets, or smartphones, without the need to download separate apps for each device.
If a PWA is installed from a phishing website, it may display an icon that closely resembles that of a legitimate banking application, with a small browser icon added. Upon opening this malicious PWA, a full-screen phishing website appears, prompting the user to enter their banking credentials.
WebAPKs
Subsequently, the threat actor enhanced this attack method by targeting clients of the same banks as before but utilizing a more advanced type of PWA known as a WebAPK. WebAPKs are Android apps automatically generated by the Chrome browser when users add a PWA to their Android device’s home screen. Differentiating between PWAs and WebAPKs, PWAs are built using web technologies, while WebAPKs integrate PWAs as native Android apps. WebAPKs resemble native Android apps more than typical PWAs, as they lack the small browser logo found in PWA icons. This absence of a browser logo can deceive users into thinking that a malicious WebAPK is a legitimate app, as depicted in Figure 3.

The distribution method remained the same – users could download and install a standalone app from phishing websites rather than just a PWA web shortcut. The installation of WebAPKs requires manual intervention, but users are not prompted to grant explicit permission to install apps from unknown sources or to allow the browser to install unknown apps, as it is not a conventional app. This lack of explicit permission may lead users to unknowingly install an app from an untrusted source. Figure 4 illustrates what it looks like when users visit a phishing website requesting an update and installation of a malicious WebAPK.
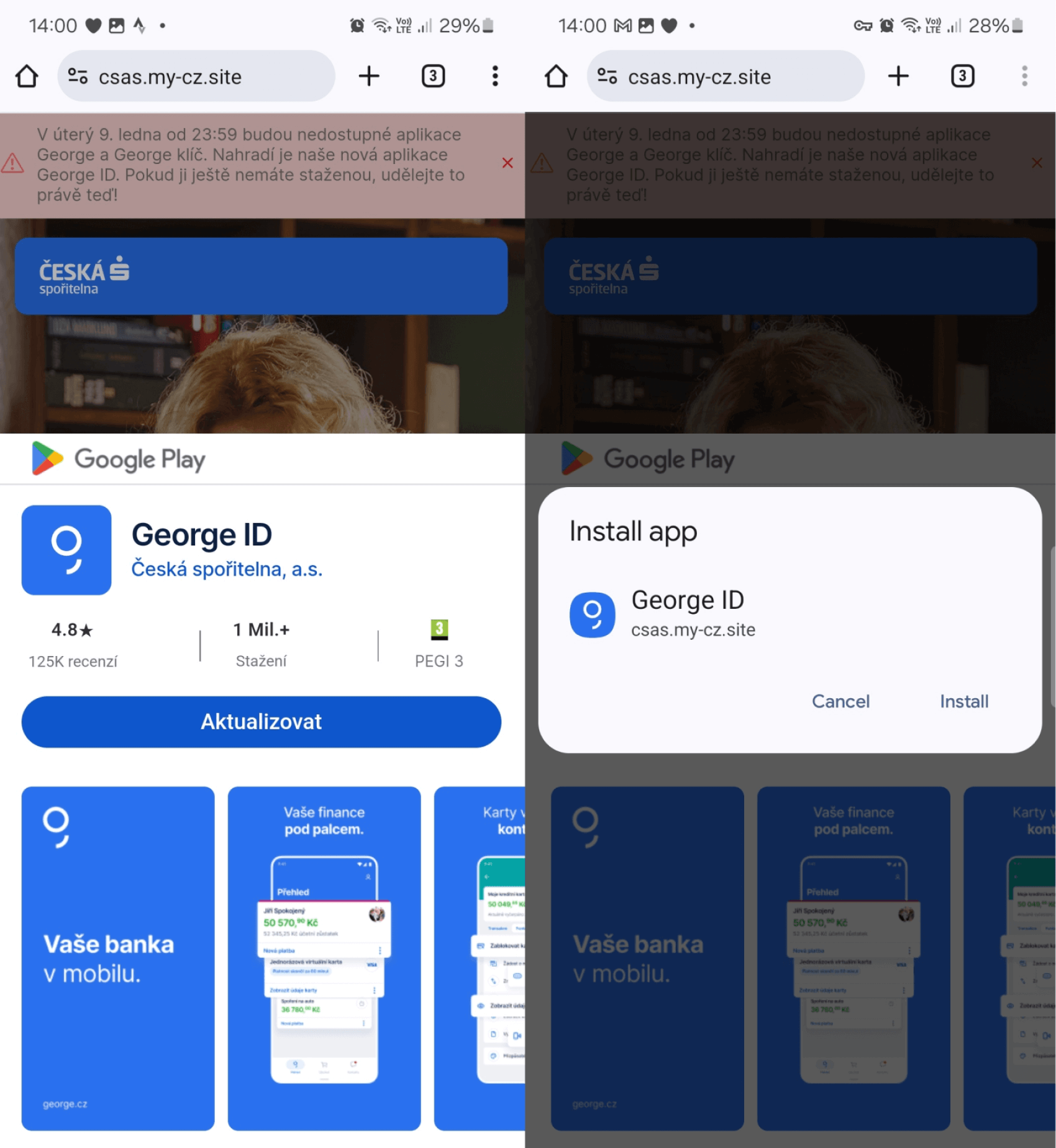
Once installed and launched, the malicious app requests banking credentials. Further details on phishing campaigns utilizing PWAs and WebAPKs were discussed in a previous blog post.
NGate malware
On March 6th, 2024, it was discovered that the NGate Android malware was available on the same distribution domains previously used for phishing campaigns delivering malicious PWAs and WebAPKs.
Upon installation and execution, NGate presents a fake website requesting the user’s banking information, which is then sent to the attacker’s server. In addition to its phishing functionalities, NGate malware features NFCGate, a tool designed to relay NFC data between two devices – the victim’s device and the perpetrator’s device. Developed by students from the Secure Mobile Networking Lab at the Technical University of Darmstadt in Germany, NFCGate is available on GitHub. NFCGate facilitates the transmission of an NFC signal from one Android device through a server to another Android device for emulation, as shown in Figure 5.
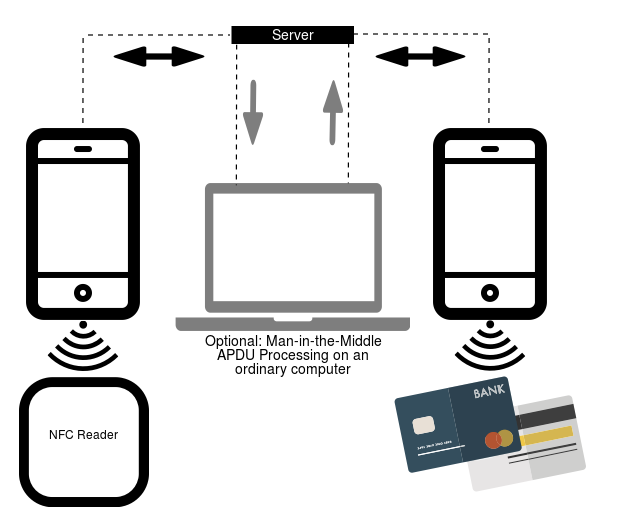
NFCGate interacts with NFC traffic on a device, capturing and relaying NFC data between devices, and mimicking or replaying intercepted data on another device. While some features require rooted devices, relaying NFC traffic is possible on non-rooted devices as well. NGate malware exploits only one of NFCGate’s features, solely focusing on relaying NFC data between devices without interfering with other device data.
Furthermore, NGate prompts victims to provide sensitive information such as their banking client ID, date of birth, and banking card PIN. Victims are instructed to activate the NFC feature on their smartphone and place their payment card behind the device until the malicious app detects the card.
Behind the scenes, the NFC data from the victim’s bank card is transmitted through a server to the attacker’s Android device, enabling the attacker to replicate the victim’s bank card on their own device. This allows the attacker to utilize the copied card data on their Android device for transactions and ATM withdrawals utilizing NFC technology.
Complete Attack Scenario with a Remedial Measure
The announcement by the Czech police outlined an attack scenario where attackers sent SMS messages to potential victims regarding tax returns, directing them to a phishing website impersonating banks. These links likely led to malicious PWAs. Once the victim installed the app and entered their credentials, the attacker gained access to the victim’s account. Subsequently, the attacker contacted the victim, posing as a bank employee, and informed them of a compromised account due to the earlier SMS. To “secure” their funds, the victim was instructed to change their PIN and verify their banking card using a mobile app – NGate malware, with a download link sent via SMS. It is suspected that victims using the NGate app would input their old PIN to create a new one and place their card behind their smartphone to verify the change. The attacker, having access to the compromised account, could alter withdrawal limits or transfer funds to another account. Utilizing NGate makes it easier for the attacker to access funds without leaving traces to their own account. A diagram of the attack sequence can be seen in Figure 6.
Other potential attack scenarios involve using NGate malware or a customized NFCGate version, especially in situations where the threat actor has physical access to clone NFC tags or payment cards. To execute these attacks, a rooted and customized Android device is required.
One possible attack involves gaining access through NFC tags, which have unique IDs and data sections storing keys. By duplicating the UID of an NFC access token, an attacker can emulate the UID to gain entry into restricted areas. Another scenario involves making small contactless payments with copied payment cards. However, this is limited to small payments, not ATM withdrawals.
The NGate malware gains initial access by tricking victims into downloading a malicious app, often through SMS messages claiming to offer tax refunds. Victims are then instructed to change their PINs and verify their cards using a different app, which contains the NGate malware. None of the malicious apps we examined were found on Google Play.
We discovered two domains resembling the Czech Raiffeisenbank and ČSOB bank where NGate was available for download, but at the time of our analysis, neither of them were active:
– raiffeisen-cz[.]eu
– app.mobil-csob-cz[.]eu
The NGate malware exhibited consistent characteristics across all six samples we studied, including the same package name (rb.system.com) and phishing URL with a unique ID parameter. All samples were signed with the same developer certificate (SHA-1 fingerprint: 0C799950EC157BB775637FB3A033A502F211E62E), indicating a uniformity in their development.
Each sample featured a distinct phishing URL, with links to five different phishing websites mimicking various banking apps. The samples were designed to deceive victims by imitating specific banking apps in both icon and name.
NGate, when initiated, presented victims with a phishing website within a WebView, prompting them to input personal information and enable NFC on their device for an NFC relay attack.
Unlike traditional malware, NGate did not rely on a Command and Control server but rather controlled the compromised device through the phishing website, using JavaScript interfaces to trigger Android functions.
NGate utilized two servers – a phishing website and an NFCGate relay server – to carry out its operations, redirecting NFC traffic from the victim’s device to the attacker’s.
To prevent such attacks, users should verify website authenticity, download apps only from official sources, keep PIN codes confidential, use security apps, disable NFC when not in use, protect RFID cards, and consider using digital versions of physical cards on smartphones.
In conclusion, ESET researchers have uncovered a novel attack scenario involving phishing and NFC traffic relay, showcasing attackers’ evolving tactics and commitment to fraudulent activities. While we have focused on one specific attack, there may be other potential misuse cases to be aware of. Hey there! Have you heard about the recent crimeware campaign targeting Czechia? It’s quite alarming as it involves the cloning of physical cards and accessing NFC tokens, potentially increasing the threat and its impacts.
The good news is that the campaign is currently on hold, likely due to the arrest of a suspected perpetrator. However, we can’t rule out the possibility of it spreading to other regions or countries in the future. The arrest of one participant with a significant amount of cash on hand serves as a stark reminder of the real-world consequences of these “virtual” crimes.
To stay safe, it’s crucial to be aware of social engineering tactics, exercise caution online, and make use of robust mobile security apps. Your online security matters, so stay vigilant!
For more details and insights, feel free to reach out to us at threatintel@eset.com. Stay informed and stay safe online!
If you’re interested in private APT intelligence reports and data feeds, check out the ESET Threat Intelligence page for more information.
Remember, your online safety is a top priority! Let’s all work together to keep our digital world secure.
And for a detailed list of Indicators of Compromise (IoCs) and samples, you can visit our GitHub repository here.
Stay safe and secure online, folks! Your cyber wellness matters. sentence to make it more concise:
“Please ensure that you have completed all the necessary paperwork before the deadline.”
“Please complete all required paperwork by the deadline.” sentence: The cat slept peacefully on the windowsill in the warm sunlight.


