Hey there, fellow cybersecurity enthusiasts! When it comes to safeguarding mid to large size enterprises against targeted cyber threats, it’s truly a global effort. Many organizations have multiple security operations centers (SOCs) spread out across regions like the Americas, APAC, and EMEA. While each SOC may focus on protecting a specific area, they can all benefit from sharing vital information such as:
1) Identifying targeted threats
2) Implementing effective remediation strategies from past incidents
With Intezer’s cutting-edge Malware Analysis technology, security teams can automatically spot and classify cyber threats by recognizing code similarities from previous incidents. By utilizing Intezer Analyze’s private indexing feature, different SOCs within the same organization can seamlessly exchange threat classifications and remediation tactics for unknown files. This helps in reducing the time spent on investigating known threats and customizing their response promptly and efficiently.
Build Your Own Genetic Database!
Enterprise users of Intezer Analyze can privately index malware and proprietary software to:
1) Swiftly minimize false positives and redundant alerts
2) Uncover targeted threats
3) Speed up incident response, across various SOC teams within the organization
Benefits:
• Privately index your trusted software to decrease false positives and duplicate alerts
• Privately index targeted threats for sharing classifications and remediation tactics from previous incidents
• Categorize files for transparency across all SOC teams
• Enhance response time by focusing on known threats with effective remediation strategies
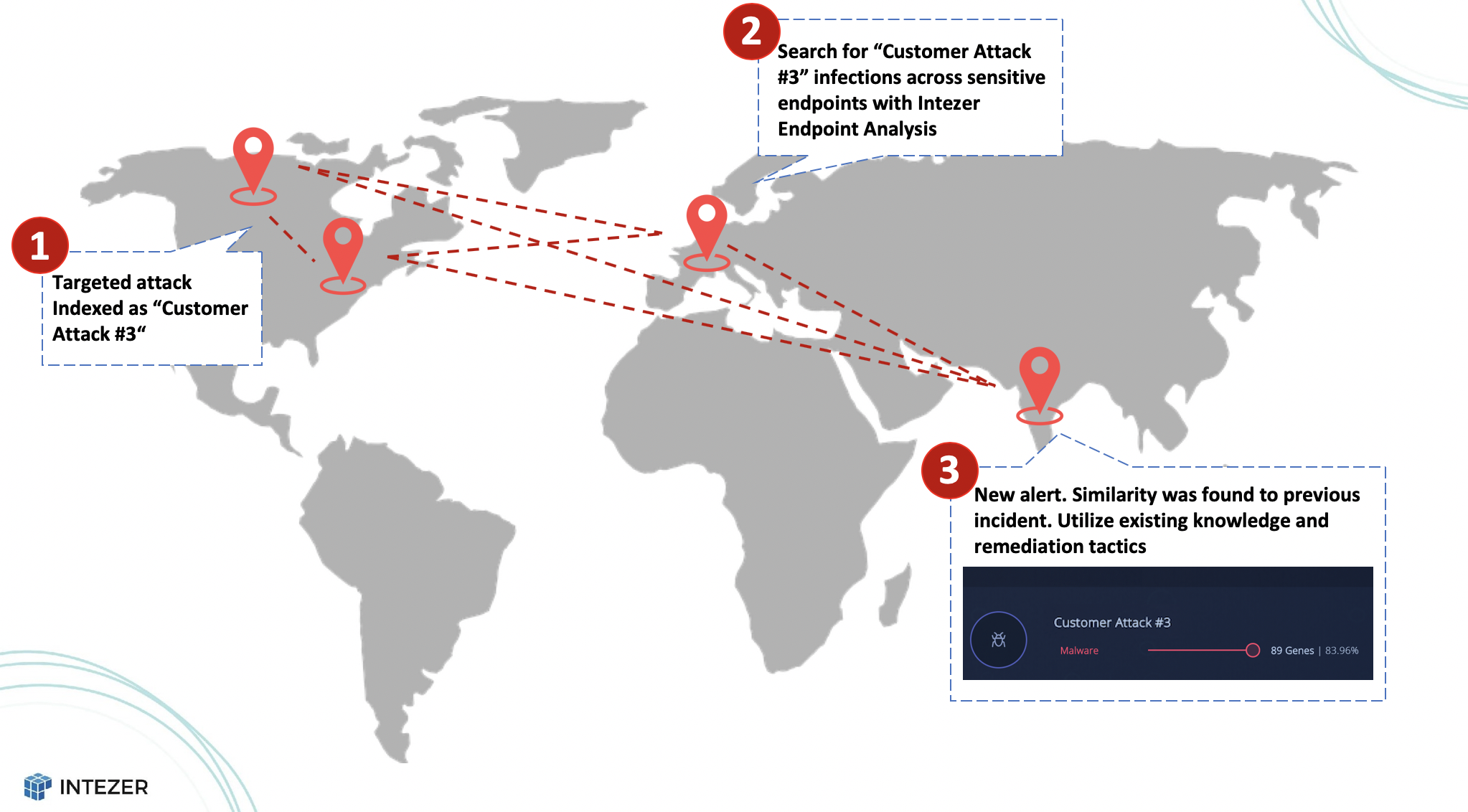
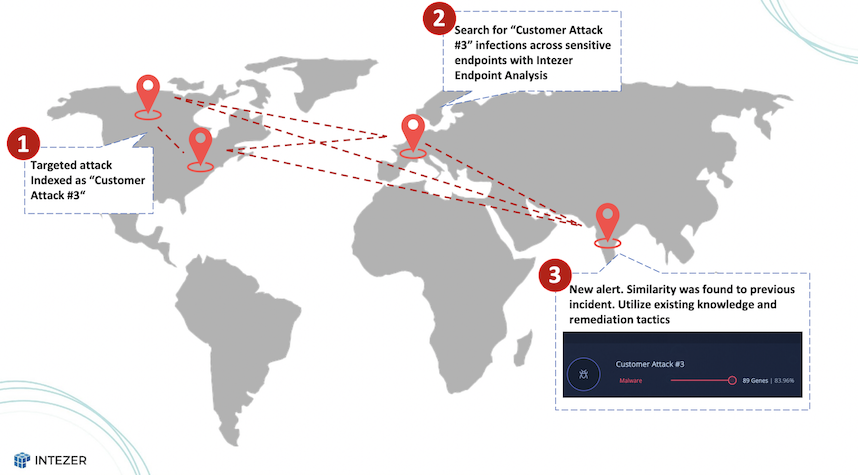
Let’s break it down with an example: if a SOC in the United States identifies a targeted attack using Intezer Analyze, they can label and index the threat as “Customer Attack #3.” Any future threat that bears even a tiny resemblance to this code will be automatically flagged as “Customer Attack #3.” This means that SOCs can swiftly determine if a threat is linked to a previous incident and seek guidance from other SOC teams worldwide for effective remediation tactics to promptly resolve the issue.
Once “Customer Attack #3” is indexed, SOCs can conduct endpoint analysis to scan for infections across sensitive endpoints. Moreover, security teams can effortlessly export a code-based YARA signature from Intezer Analyze to proactively hunt for variations of the threat targeting the organization in different regions. Since Intezer’s YARA signatures are solely based on a threat’s malicious and unique code—not on shared or embedded libraries—the accuracy of hits is significantly enhanced.
Intezer boasts a robust API that can fully automate the functionalities mentioned above. For more details on Intezer’s private indexing feature, feel free to request a demo today: https://intezer.com//contact-us/.