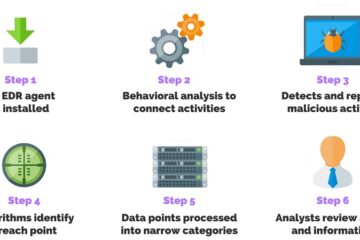
Endpoint detection and response (EDR) is a cutting-edge security system that keeps your endpoints safe from threats. But what exactly is EDR? EDR is an integrated endpoint security system that continuously monitors and gathers data from endpoints. This data is then analyzed and responded to automatically based on predefined rules. Also known as endpoint threat detection and response (ETDR), EDR was coined by Anton Chuvakin of Gartner to define new security technologies that focus on detecting and investigating suspicious activity on hosts and endpoints.
The main goals of an EDR security system are to observe and collect endpoint activity data that may indicate a threat, analyze this data for threat patterns, automatically remove or contain threats when detected, and alert security personnel. Additionally, EDR tools provide forensics and analysis capabilities to investigate any identified risks.
So, how does EDR work, and what should you look for in an EDR solution? Here are some key aspects to consider:
1. Endpoint Visibility: Real-time visibility across all endpoints allows you to spot adversary behaviors as they try to infiltrate your environment and take immediate action.
2. Threat Database: Gathering and enhancing data from endpoints is crucial for effective EDR. This data can be analyzed for attack indicators using various methods.
3. Behavioral Protection: Behavioral techniques are essential for detecting signs of attack before a breach occurs. Look for EDR solutions that focus on detecting indications of attack (IOAs) rather than relying solely on indications of compromise (IOCs).
4. Insight and Intelligence: A threat intelligence-integrated EDR solution can provide valuable insights into the adversaries targeting your organization and other relevant information about the attack.
5. Fast Response: EDR solutions that enable rapid incident response can help prevent attacks from escalating into breaches and minimize downtime for your organization.
6. Cloud-based Solution: Opting for a cloud-based EDR solution ensures that endpoint performance is not affected while allowing for precise real-time search and investigation capabilities.
Modern Advanced Persistent Threats (APTs) pose a significant risk to organizations, as threat actors can bypass traditional defenses undetected. EDR solutions help protect against common attack strategies used by initial access brokers, such as malicious scripts, file-less malware, and stolen credentials.
In conclusion, EDR works by monitoring and analyzing endpoint activities, identifying anomalies, automatically responding to threats, isolating affected systems, investigating threats, and alerting security teams. To find the best EDR solutions for your organization, visit the website mentioned below for more information.