ESET researchers have identified multiple samples of Linux backdoor, which we have named WolfsBane, that we attribute with high confidence to the Gelsemium advanced persistent threat (APT) group. This China-aligned threat actor has a known history dating back to 2014 and until now, there have been no public reports of Gelsemium using Linux malware. Additionally, we discovered another Linux backdoor, which we named FireWood. However, we cannot definitively link FireWood to other Gelsemium tools, and its presence in the analyzed archives might be coincidental. Thus, we attribute FireWood to Gelsemium with low confidence, considering it could be a tool shared among multiple China-aligned APT groups.
The most notable samples we found in archives uploaded to VirusTotal are two backdoors resembling known Windows malware used by Gelsemium. WolfsBane is the Linux counterpart of Gelsevirine, while FireWood is connected to Project Wood. We also discovered other tools potentially related to Gelsemium’s activities. The goal of the backdoors and tools discovered is cyberespionage targeting sensitive data such as system information, user credentials, and specific files and directories. These tools are designed to maintain persistent access and execute commands stealthily, enabling prolonged intelligence gathering while evading detection.
The trend of APT groups focusing on Linux malware is becoming more noticeable. We believe this shift is due to improvements in Windows email and endpoint security, such as the widespread use of endpoint detection and response (EDR) tools and Microsoft’s decision to disable Visual Basic for Applications (VBA) macros by default. Consequently, threat actors are exploring new attack avenues, with a growing focus on exploiting vulnerabilities in internet-facing systems, most of which run on Linux.
In this blogpost, we provide technical analysis of the Linux malware, mainly focusing on the two different backdoors.
Key points of the blogpost:
- ESET researchers found archives with multiple Linux samples, containing two previously unknown backdoors.
- The first backdoor, WolfsBane, is a Linux version of Gelsevirine, a Windows backdoor used by Gelsemium.
- Its dropper is the equivalent of the Gelsemine dropper, and features a hider based on an open-source userland rootkit.
- The second backdoor, which we have named FireWood, is connected to Project Wood. The Windows version of the Project Wood backdoor was previously used by the Gelsemium group in Operation TooHash.
- Alongside the backdoors, we found additional tools, mainly web shells based on publicly available code.
Overview
In 2023, we found these samples in archives uploaded to VirusTotal from Taiwan, the Philippines, and Singapore, probably originating from an incident response on a compromised server. Gelsemium has previously targeted entities in Eastern Asia and the Middle East.
The first backdoor is a part of a simple loading chain consisting of the dropper, launcher, and backdoor. We named this malware WolfsBane. As explained in the Attribution and connection and Technical analysis sections, WolfsBane is a Linux equivalent of Gelsemium’s Gelsevirine backdoor and the WolfsBane dropper is analogous to the Gelsemine dropper. Our name for Gelsemium comes from one possible translation of the name we found in the report from VenusTech, who dubbed the group 狼毒草. It’s the name of a genus of flowering plants in the family Gelsemiaceae, and Gelsemium elegans is the species that contains toxic compounds like Gelsemine, Gelsenicine, and Gelsevirine, which we chose as names for the three components of this malware family. We previously analyzed Gelsevirine and Gelsemine in this white paper. Part of the analyzed WolfsBane attack chain is also a modified open-source userland rootkit, a type of software that exists in the user space of an operating system and hides its activities.
The second backdoor, which we named FireWood, is connected to a backdoor tracked by ESET researchers under the name Project Wood, previously analyzed in the Project Wood section of this blogpost. We have traced it back to 2005 and observed it evolving into more sophisticated versions.
The archives we analyzed also contain several additional tools, mostly webshells, that allow remote control to a user once they are installed on a compromised server, and simple utility tools.
Attribution and connection
In this section, we explain the similarities that led us to attribute the WolfsBane malware to the Gelsemium APT group and establish a connection between the FireWood backdoor and the Project Wood malware.
WolfsBane links to Windows Gelsevirine
Based on the following similarities, we assess that the WolfsBane backdoor is the Linux version of Gelsevirine. Therefore, we attribute WolfsBane to the Gelsemium APT group with high confidence:
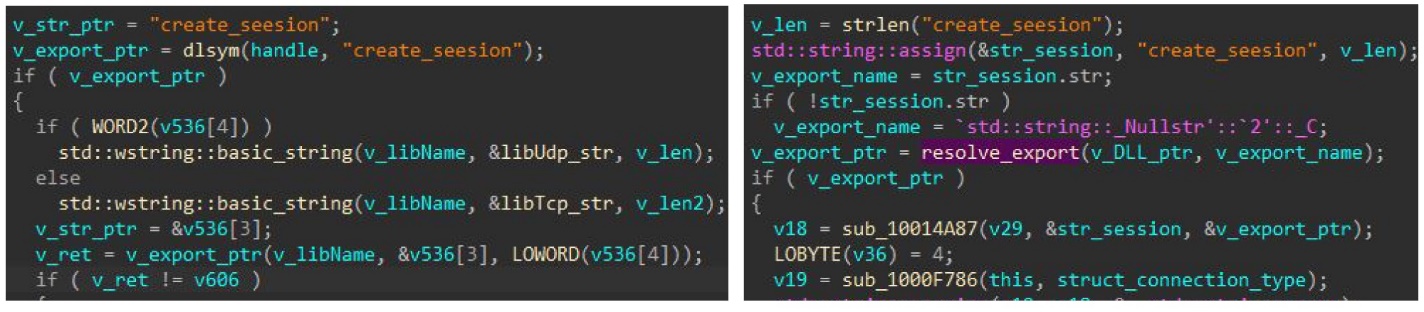
- Custom libraries for network communication: Both the Linux and Windows versions load an embedded custom library for network communication, with a different library for each communication protocol used. The backdoor accesses the library’s functions by calling its create_seesion export/symbol; notably, the typo seesion is the same in both versions (as shown in Figure 1).
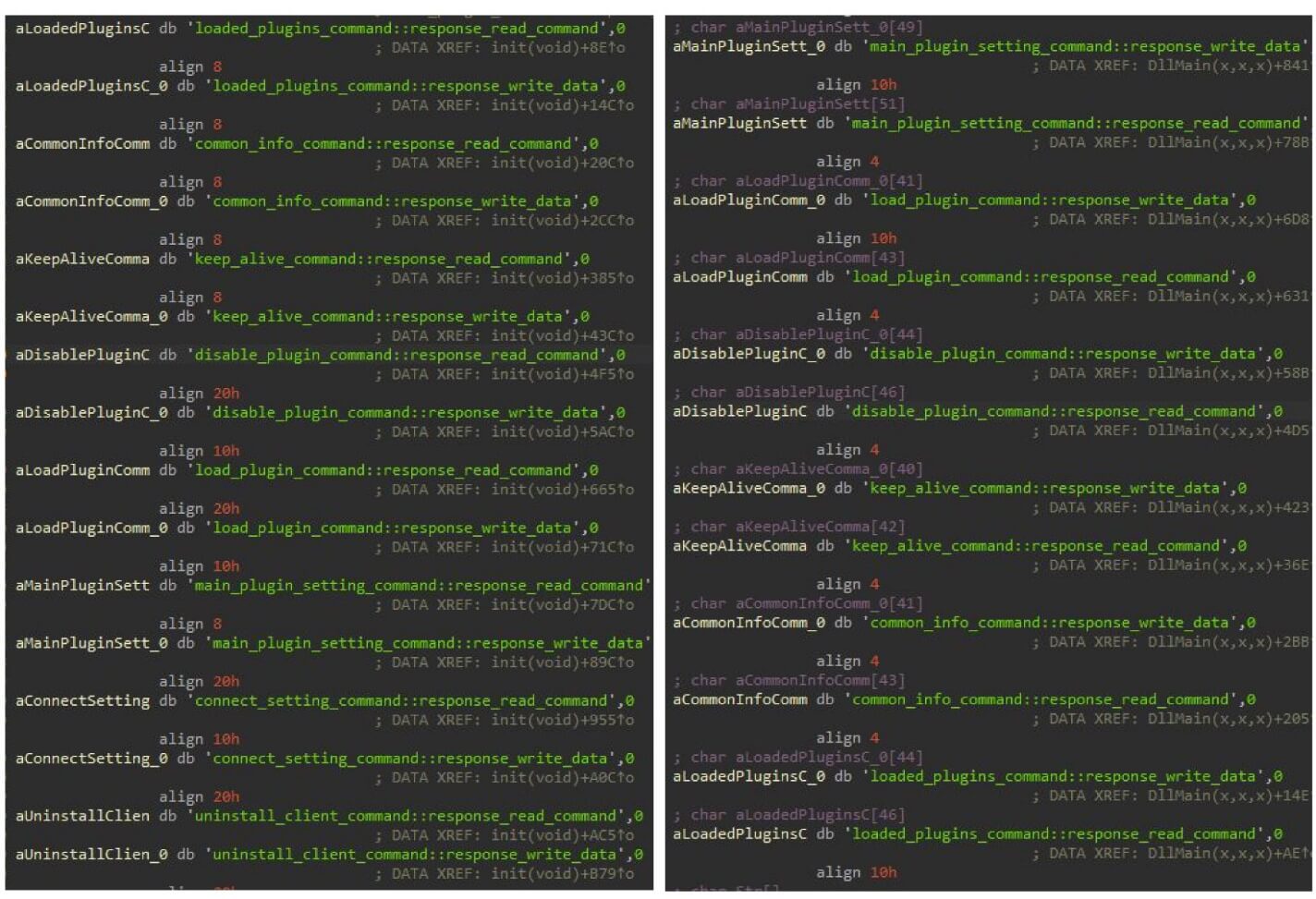
- Command execution mechanism: Both versions use the same mechanism for executing commands received from the C&C server. The backdoor creates a table with hashes (derived from the command name) and corresponding pointers to functions that handle those commands (Figure 2). We provide more details in the Technical analysis section.
- Configuration structure: Both backdoors use a very similar configuration structure. While the Linux version has some omitted fields and some extra ones, most of the field names are consistent. For example, the value of pluginkey found in the configuration is the same as in all Windows Gelsevirine samples from 2019.
Furthermore, the Linux version configuration’s controller_version values are aligned with those found in the Gelsevirine samples.
Regarding domain usage, the domain dsdsei[.]com, utilized in the Linux version, was previously identified by ESET researchers as an indicator of compromise (IoC) associated with the Gelsemium APT group.
The FireWood sample exhibits code similarities with the backdoor employed in Operation TooHash (SHA-1: ED5342D9788392C6E854AAEFA655C4D3B4831B6B), as detailed by G DATA. This backdoor, later named Project Wood by ESET researchers, shares naming conventions, file extensions, encryption algorithms, C&C communication strings, and networking code with the FireWood backdoor. Based on these similarities, it is highly likely that the FireWood backdoor is the Linux continuation of the Project Wood backdoor. However, a direct connection to other Gelsemium tools cannot be definitively proven, leading to attribution to Gelsemium with low confidence and acknowledging the potential for shared tools among Chinese APT groups. The objective remains consistent irrespective of the method of establishment: to run the binary that parses its embedded configuration and triggers the next phase, the WolfsBane backdoor, from the specified file in the configuration.
Phase 3: WolfsBane backdoor
Contained in a file named udevd, the WolfsBane backdoor initializes by loading an embedded library and invoking its main_session export, which encompasses the primary backdoor functionalities. This library, identified as libMainPlugin.so by its creators, mirrors the Windows Gelsevirine backdoor’s MainPlugin.dll.
Similar to its Windows version, the WolfsBane backdoor utilizes other embedded libraries for network communication, named libUdp.so and libHttps.so in the samples collected. Both libraries export the symbol create_seesion, maintaining the same spelling error present in the Gelsevirine TCP module for Windows. These shared libraries facilitate C&C communications via UDP and HTTPS protocols, respectively.
The backdoor encrypts the libMainPlugin.so library using the RC4 algorithm, with the key sourced from the pluginkey value in the configuration, and saves it to <work_directory>/X1l/data/gphoto2. Upon subsequent executions, the backdoor checks for this file: if present, it decrypts and loads the file instead of the embedded libMainPlugin.so. This mechanism facilitates updating the backdoor by overwriting the file.
Similar to the Windows version, the WolfsBane backdoor adopts a comparable method for executing commands received from its C&C server.
WolfsBane Hider rootkit
The WolfsBane backdoor employs a modified open-source BEURK userland rootkit to conceal its operations. Located in /usr/lib/libselinux.so, this rootkit leverages the operating system’s preload mechanism to load into new processes before other libraries, by appending its path to the /etc/ld.so.preload file, enabling its functions to intercept the original ones.
The WolfsBane Hider rootkit intercepts various standard C library functions such as open, stat, readdir, and access. While these intercepted functions call the original ones, they filter out any data related to the WolfsBane malware. Unlike the initial BEURK rootkit that uses an embedded configuration file for filtering, the WolfsBane developers retained the default configuration but adjusted the source code to exclude information linked to the hardcoded filenames of the malware executables udevd and kde. Moreover, the network traffic-concealing features of the original BEURK rootkit are absent.
FireWood backdoor
Residing in a file named dbus, the FireWood backdoor is the Linux OS continuation of the Project Wood malware, as mentioned in the Attribution and connection section. The analyzed code indicates that the file usbdev.ko functions as a kernel driver module serving as a rootkit to conceal processes. The FireWood backdoor communicates with the kernel drivers using the Netlink protocol.
FireWood employs a configuration file named kdeinit, encrypted with XOR using the single-byte key 0x26. The configuration file’s layout is outlined in Table 2.
Table 2. Selected offsets and their corresponding values from the FireWood backdoor configuration file
FireWood Backdoor Commands
| Command ID | Description |
| 0x105 | Download and execute an executable file from the C&C server with the ‑UPDATE parameter. |
| 0x110 | Execute a shell command using the popen function. |
| 0x111 | Modify connection time value in the configuration. |
| 0x112 | Conceal a process using the usbdev.ko kernel module. |
| 0x113 | Adjust delay time in configuration. |
| 0x114 | Modify connection day value in configuration. |
| 0x132 | Cleanup and exit. |
| 0x181 | List contents of a specified directory. |
| 0x182 | Exfiltrate a specified file to the C&C server. |
| 0x183 | Delete a specified file. |
| 0x184 | Rename a specified file. |
| 0x185 | Execute a specified file using the system function. |
| 0x186 | Download a file from the C&C server. |
| 0x189 | Exfiltrate a specified folder to the C&C server. |
| 0x193 | Load a specified kernel module or shared library. |
| 0x194 | Unload a specified kernel module or shared library. |
| 0x19F | Modify the timestamp of a specified file. |
| 0x200 | Delete a specified directory. |
| 0x201 | Read the content of a specified file and send it to the C&C server. |
| 0x1018F | Search for a specified file in the folder defined in the command. |
text to make it more engaging:
“Transform your life by taking charge of your happiness and success. Start today by seizing every opportunity that comes your way. Don’t wait for success to find you, go out and create it!” sentence in your own words.
Please provide an original sentence that I can help you rewrite. Rewrite the given sentence for me to understand better. sentence “The dog ran quickly across the field.”
Rewritten sentence: The dog sprinted across the field with speed. Rewrite the sentence: He is going to the store to buy some milk.
Rewritten sentence: He is heading to the store to purchase milk.


