In this article, we present a technical analysis of CloudScout, a toolset utilized by the Evasive Panda group to target a government entity and a religious organization in Taiwan between 2022 and 2023. The CloudScout toolset is capable of extracting data from various cloud services by using stolen web session cookies. It seamlessly integrates with MgBot, Evasive Panda’s malware framework, through a plugin.
Key Points:
– CloudScout was identified in Taiwan in 2022 and 2023, targeting a religious institution and a government entity.
– Stolen cookies from MgBot plugins are used by CloudScout to access and extract data from cloud services.
– Three CloudScout modules were analyzed for stealing data from Google Drive, Gmail, and Outlook, with additional modules likely existing.
– Hardcoded data in CloudScout’s requests for stealing Outlook emails indicate a focus on Taiwanese users.
– Each CloudScout module is written in C# and deployed by an MgBot plugin written in C++.
Evasive Panda Overview:
Evasive Panda, also known as BRONZE HIGHLAND, Daggerfly, or StormBamboo, is an APT group aligned with China since 2012. They engage in cyberespionage against entities opposing China’s interests, including Tibetan diaspora, Taiwanese religious and academic institutions, and pro-democracy groups in China, as well as countries like Vietnam, Myanmar, and South Korea. They employ sophisticated tactics like supply-chain attacks, watering-hole attacks, and malware development, including multiplatform backdoors for Windows, macOS, and Android.
Victimology:
ESET telemetry detected CloudScout in two incidents in Taiwan:
– In May 2022, a religious institution in Taiwan was compromised with MgBot and Nightdoor, with CloudScout modules deployed.
– In February 2023, CloudScout modules and Nightdoor were discovered at a suspected Taiwanese government entity.
Technical Analysis:
CloudScout is a .NET malware framework comprising modules targeting various cloud services, named after PDB paths like CGD for Google Drive, CGM for Gmail, and COL for Outlook. Other modules like CTW and CFB may target Twitter and Facebook. The toolset appears to have been developed around 2020, based on the Copyright field in the .NET manifest.
Old Dog, New Tricks:
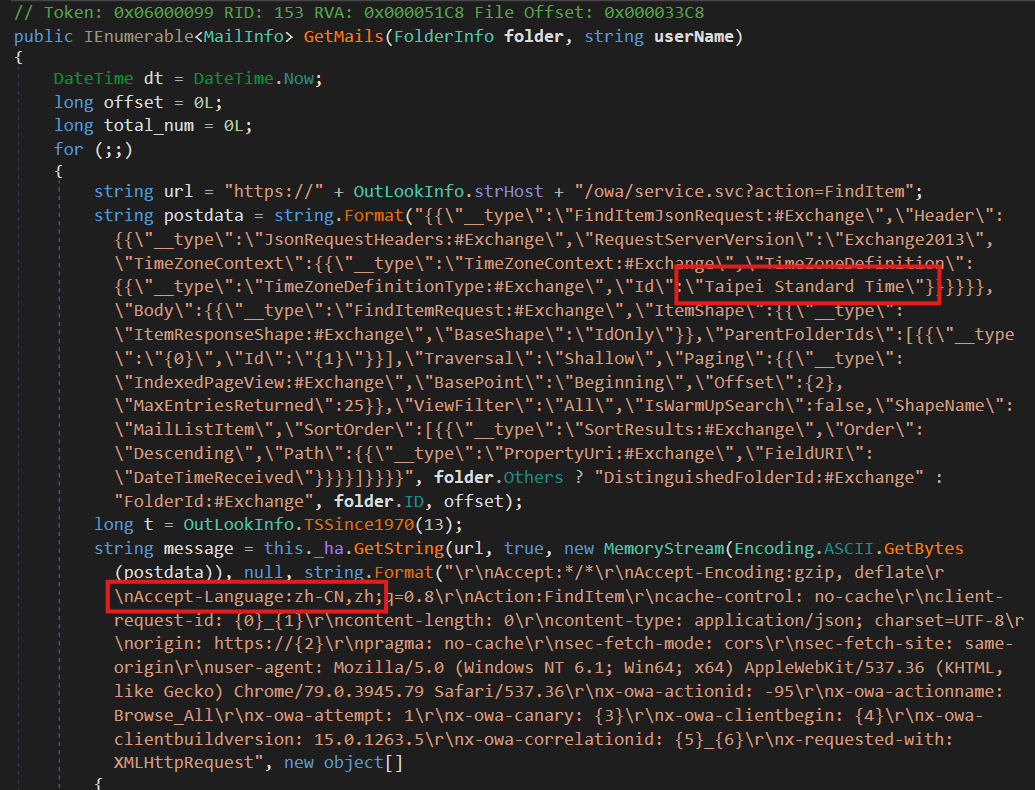
A common RC4 encryption key among the modules revealed that CGM was deployed by an MgBot plugin called Gmck.dll in an incident at a religious institution in Taiwan in 2022. MgBot installed CGM to access the victim’s Gmail account for data theft. The compromise chain observed in the network of a religious institution in Taiwan involves the Gmck.dll (Gmck) carrying the .NET module CGM within its binary. To execute CGM, Gmck drops the module to disk at a hardcoded path, starts the common language runtime (CLR) using ICLRMetaHost and ICLRRuntimeHost, and then calls ExecuteInDefaultAppDomain with a reference to CGM’s entry point function (ModuleStart). The CGD and COL modules are also written to the same staging folder as CGM. The staging folder NVIDlA is purposely misspelled for obfuscation purposes. After deploying the CGM module, Gmck provides browser cookies to CGM in a configuration file extracted from web browser database files. The configuration file must be RC4 encrypted using a specific key for CGM to recognize it. The CloudScout modules continuously monitor their working directory for configuration files in .dat format, handling them in separate threads for multiple configurations. The CommonUtilities package provides low-level libraries for the modules to run, and the HTTPAccess library allows for modifying HTTP headers with cookie integration. The core functionality of CloudScout modules is in the Cloud namespace, with authentication and data retrieval functions tailored to specific cloud services. Authentication cookies from services like Google Drive, Gmail, and Outlook are used to access and download data, with mechanisms in place to handle authentication and retrieve necessary cookies. In order to achieve this goal, each CloudScout module comes equipped with a set of hardcoded web requests to execute, along with intricate HTML parsers that are able to identify and extract the desired data from the web responses.
For instance, the CGM and COL modules focus on obtaining mail folder listings and email messages from Gmail and Outlook, respectively. The process that CGM undergoes to extract email headers, email bodies, and attachments from the HTML content provided by the Gmail web server is illustrated in Figure 14.
Conversely, CGD is interested in gathering user information from Google Drive, a complete directory hierarchy, and files with specific extensions like .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, and .txt. The code snippet from CGD, shown in Figure 15, demonstrates how a download URL for a document is generated.
Furthermore, a custom header is added to each downloaded item, whether it be a file or an email. This custom header includes metadata such as the client ID (assigned by the malware), email subject or filename, and the username of the cloud service. This additional header likely facilitates the processing of stolen data on a large scale by automated systems for quick indexing or analysis.
Subsequently, each item is encrypted using the same RC4 key as the configuration file and saved with the filename
Following this, all items are compressed into a ZIP archive named
In conclusion, CloudScout serves as a .NET toolset utilized by Evasive Panda for the purpose of extracting data stored in cloud services. It functions as an extension to MgBot and employs the pass-the-cookie technique to hijack authenticated sessions from web browsers.
For any questions regarding our research featured on WeLiveSecurity, please reach out to us at threatintel@eset.com. ESET Research also offers private APT intelligence reports and data feeds. For inquiries about this service, please visit the ESET Threat Intelligence page.
If you’re interested in a more detailed list of indicators of compromise (IoCs) and samples, you can find them in our GitHub repository. Can you please rewrite the sentence?