Ever wondered how EDR works?
Come along on this journey to uncover the inner workings of EDR,
When it comes to safeguarding endpoints, OpenEDR® stands as a formidable defense against ransomware, Trojans, and various forms of malware.
In the year 2021 alone, hackers attempted over 700 million ransomware attacks.
Your organization can mitigate the financial impact of a breach like ransomware by utilizing an Endpoint Detection and Response (EDR) tool. This tool diligently monitors endpoints for any signs of malicious activity. Upon detecting an anomaly, the software isolates the threat and notifies the system administrator. With this proactive approach, cyber criminals are prevented from infiltrating your entire system as their attack is meticulously analyzed in a controlled environment.
Curious about XDR?
XDR, short for Extended Detection and Response, offers comprehensive security across endpoints, networks, and cloud environments. By deploying this software within your business network, you can aggregate data from multiple security layers, enabling your security team to swiftly identify threats by gaining a holistic view of your organization’s IT infrastructure. Furthermore, XDR enhances response times through improved visibility and investigative tools.
But how does XDR actually function?
Let’s delve into the realm of XDR deployment;
Security analysts often grapple with alerts from various sources, leading to a deluge of false positives and disjointed threat perspectives.
XDR rises to meet this challenge head-on. By centralizing security operations, XDR eliminates the possibility of cyber criminals evading detection within segregated security silos. Equipped with powerful investigative capabilities, your Security Operations Center (SOC) team can conduct thorough analyses on behavioral patterns across email, servers, cloud workloads, networks, and endpoints, all in a fraction of the time it would take manually, thanks to XDR’s automated analysis. This comprehensive approach fortifies your organization’s security posture.
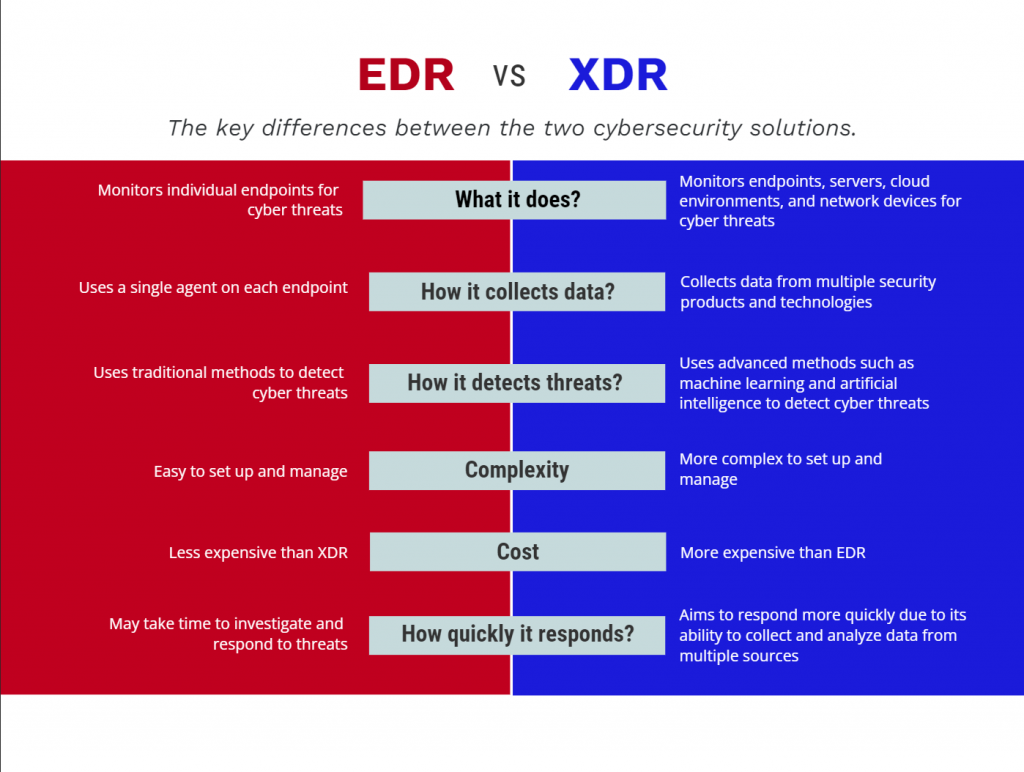

EDR vs XDR- What’s Similar?
Having explored the functionality of EDR and XDR, it’s time to uncover their similarities. Here are some common features of both tools.
- Proactive Defense: Both EDR and XDR offer proactive security measures to prevent and thwart attacks. By leveraging data analytics and threat intelligence, these solutions empower your team to proactively identify and neutralize potential threats before they escalate.
- Swift Response to Threats: Both EDR and XDR provide automated threat detection and response capabilities, enabling your organization to swiftly contain and analyze malicious activities. For instance, OpenEDR® isolates malicious files, preventing the spread of attacks across networks and endpoints.
- Support for Threat Hunting: In today’s landscape of sophisticated threat actors, organizations require advanced security measures beyond traditional antivirus solutions.
Thus, a brief comparison of EDR vs XDR emphasizes their shared proactive security approach, offering deep visibility and proactive threat detection across all devices.
EDR vs XDR: Unveiling the Differences
Having identified the common ground between XDR and EDR, let’s now distinguish their key disparities.
While EDR exclusively gathers data from endpoints, XDR extends its reach to encompass data from endpoints, workstations, cloud environments, and networks. While endpoint security remains pivotal due to the prevalence of cyber threats originating from this point, overlooking other security domains could leave vulnerabilities. Therefore, for comprehensive coverage, opting for an Xtended Detection and Response (XDR) solution proves beneficial.
In Conclusion – EDR vs XDR
With a comprehensive analysis of EDR vs XDR, the question arises: which solution best suits your organization’s needs? While EDR provides dedicated endpoint security, XDR offers an extended layer of protection by safeguarding all facets of your enterprise.
Explore More:
– What is XDR
– EDR Vendors
– EDR
– Endpoint Detection and Response



