Cybercriminals have been known to approach their targets under the guise of company recruiters, enticing them with fake employment offers. After all, what better time to strike than when the potential victim is distracted by the possibility of getting a job? Since early 2024, ESET researchers have observed a series of malicious North Korea-aligned activities, where the operators, posing as headhunters, try to serve their targets with software projects that conceal infostealing malware. We call this activity cluster DeceptiveDevelopment.
As part of a fake job interview process, the DeceptiveDevelopment operators ask their targets to do a coding test, such as adding a feature to an existing project, with the files necessary for the task usually hosted on private repositories on GitHub or other similar platforms. Unfortunately for the eager work candidate, these files are trojanized: once they download and execute the project, the victim’s computer gets compromised with the operation’s first-stage malware, BeaverTail.
DeceptiveDevelopment was first publicly described by Phylum and Unit 42 in 2023, and has already been partially documented under the names Contagious Interview and DEV#POPPER. We have conducted further analysis of this activity cluster and its operator’s initial access methods, network infrastructure, and toolset, including new versions of the two malware families used by DeceptiveDevelopment – InvisibleFerret, and the aforementioned BeaverTail.
Key points of this blogpost:
- DeceptiveDevelopment targets freelance software developers through spearphishing on job-hunting and freelancing sites, aiming to steal cryptocurrency wallets and login information from browsers and password managers.
- Active since at least November 2023, this operation primarily uses two malware families – BeaverTail (infostealer, downloader) and InvisibleFerret (infostealer, RAT).
- DeceptiveDevelopment’s tactics, techniques, and procedures (TTPs) are similar to several other known North Korea-aligned operations.
We first observed this DeceptiveDevelopment campaign in early 2024, when we discovered trojanized projects hosted on GitHub with malicious code hidden at the end of long comments, effectively moving the code off-screen. These projects delivered the BeaverTail and InvisibleFerret malware. In addition to analyzing the two malware families, we also started investigating the C&C infrastructure behind the campaign. Since then, we have been tracking this cluster and its advances in strategy and tooling used in these ongoing attacks. This blogpost describes the TTPs of this campaign, as well as the malware it uses.
DeceptiveDevelopment profile
DeceptiveDevelopment is a North Korea-aligned activity cluster that we currently do not attribute to any known threat actor. Operators behind DeceptiveDevelopment target software developers on Windows, Linux, and macOS. They primarily steal cryptocurrency for financial gain, with a possible secondary objective of cyberespionage.
To approach their targets, these operators use fake recruiter profiles on social media, not unlike the Lazarus group in Operation DreamJob (as described in this WeLiveSecurity blogpost). However, while Operation DreamJob targeted defense and aerospace engineers, DeceptiveDevelopment reaches out to freelance software developers, often those involved in cryptocurrency projects. To compromise its victims’ computers, DeceptiveDevelopment provides its targets with trojanized codebases that deploy backdoors as part of a faux job interview process.
Victimology
The primary targets of this DeceptiveDevelopment campaign are software developers, mainly those involved in cryptocurrency and decentralized finance projects. The attackers don’t distinguish based on geographical location and aim to compromise as many victims as possible to increase the likelihood of successfully extracting funds and information.
We have observed hundreds of different victims around the world, using all three major operating systems – Windows, Linux, and macOS. They ranged from junior developers just starting their freelance careers to highly experienced professionals in the field. We only observed attacker–victim conversations in English, but cannot say with certainty that the attackers will not use translation tools to communicate with victims who don’t speak that language. A map showing the global distribution of victims can be seen in Figure 1.
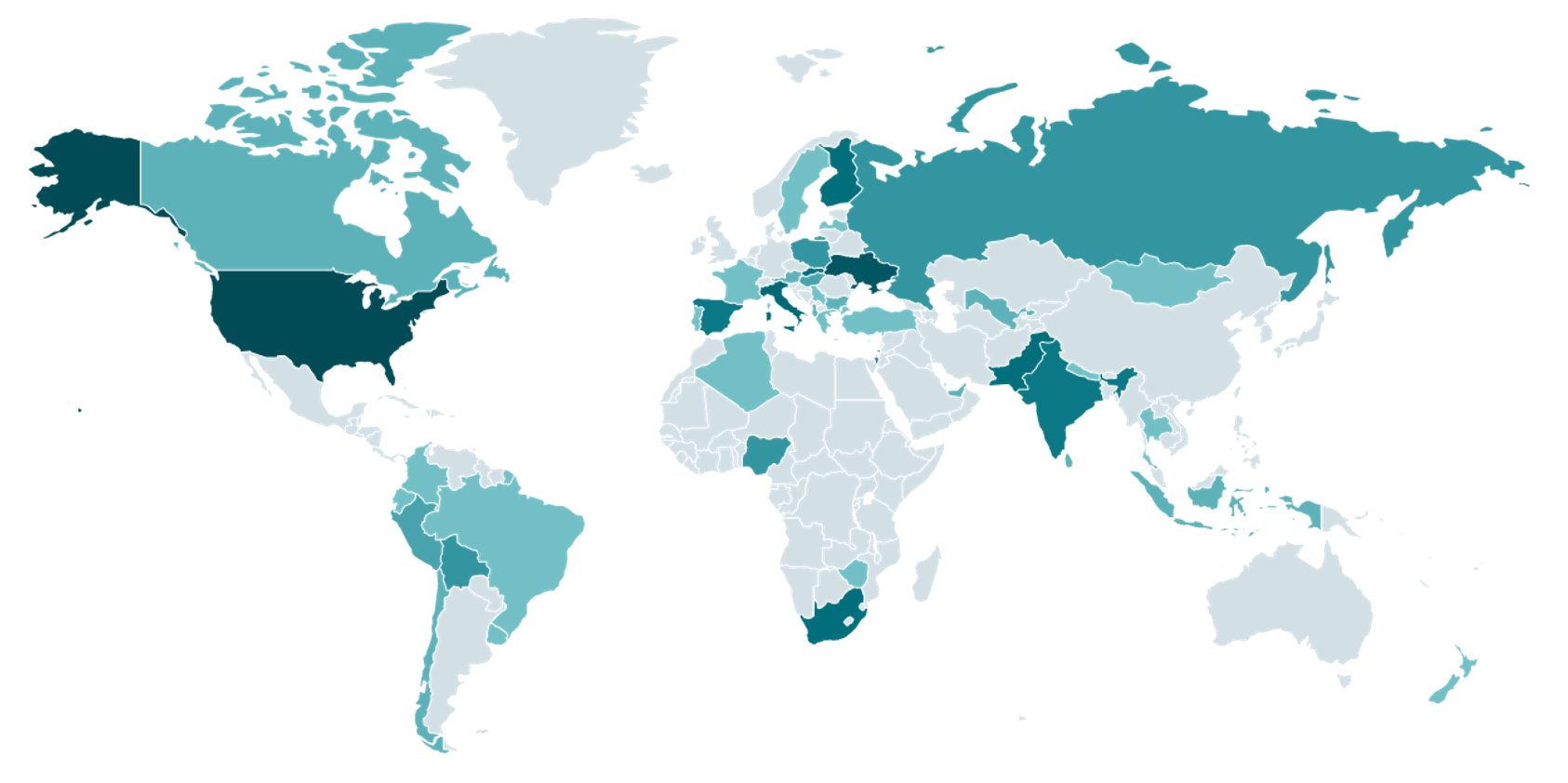
Attribution
We consider DeceptiveDevelopment to be a North Korea-aligned activity cluster with high confidence based on several elements:
- We observed connections between GitHub accounts controlled by the attackers and accounts containing fake CVs used by North Korean IT workers. These people apply for jobs in foreign companies under false identities in order to collect salaries to help fund the regime. The observed connections were mutual follows between GitHub profiles where one side was associated with DeceptiveDevelopment, and the other contained fake CVs and other material related to North Korean IT worker activity. Similar connections were also observed by Unit42. Unfortunately, the GitHub pages were taken down before we were able to record all the evidence.
- The TTPs (use of fake recruiters, trojanized job challenges, and software used during interviews) are similar to other North Korea-aligned activity (Moonstone Sleet, and Lazarus’s DreamJob and DangerousPassword campaigns).
In addition to the connections between the GitHub profiles, the malware used in DeceptiveDevelopment is rather simple. This tracks with the reporting done by Mandiant claiming that the IT workers’ work is usually of poor quality.
While monitoring DeceptiveDevelopment activity, we saw numerous cases showing a lack of attention to detail on the part of the threat actors. In some of them, the authors failed to remove development notes or commented-out local IP addresses used for development and testing. We also saw samples where they seem to have forgotten to obfuscate the C&C address after changing it; this can be seen in Figure 2. Furthermore, the malware uses freely available obfuscation tools with links to them sometimes left in code comments.
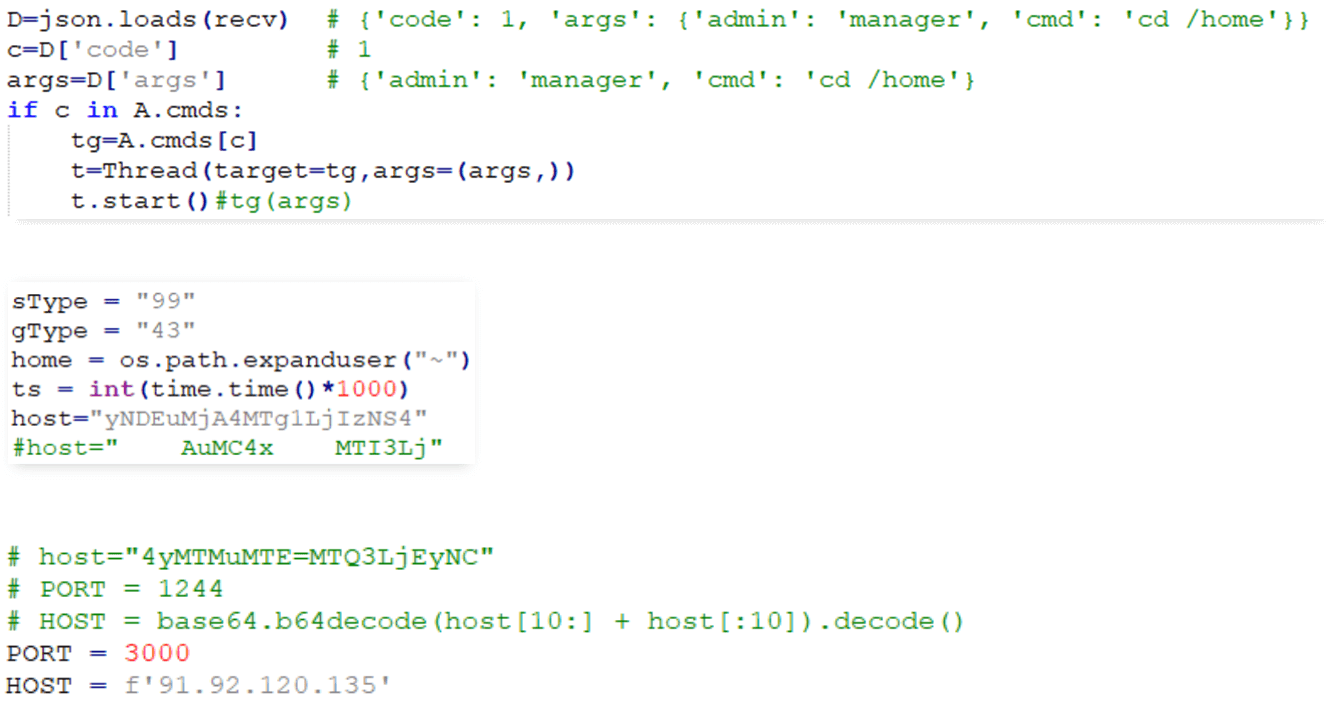
Technical analysis
Initial access
In order to pose as recruiters, the attackers copy profiles of existing people or even construct new personas. They then either directly approach their potential victims on job-hunting and freelancing platforms or post fake job listings there. At first, the threat actors used brand new profiles and would simply send links to malicious GitHub projects via LinkedIn to their intended targets.
Later, they began utilizing profiles that appeared established, with numerous followers and connections, to enhance their credibility. They expanded their efforts to various job-hunting and code-hosting websites. Some of these profiles are created by the attackers themselves, while others may be compromised profiles of real individuals on the platform that have been altered by the attackers.
These interactions take place on platforms that range from generic job-hunting sites to those focused on cryptocurrency and blockchain projects, aligning with the attackers’ objectives. The platforms include LinkedIn, Upwork, Freelancer.com, We Work Remotely, Moonlight, and Crypto Jobs List.
The most common method of compromise involves the fake recruiter presenting the victim with a trojanized project under the guise of a hiring challenge or offering a financial reward for fixing a bug. Victims receive the project files through file transfer on the site or a link to a repository like GitHub, GitLab, or Bitbucket. They are then asked to download the files, make modifications, and report back to the recruiter. The repositories are typically private, requiring the victim to provide their account ID or email address for access.
In some cases, victims upload completed tasks to their own public repositories, inadvertently exposing the malicious activity. The trojanized projects typically fall into categories such as hiring challenges, cryptocurrency projects, blockchain-based games, and gambling applications with cryptocurrency features. These projects often mimic existing open-source projects, with minimal changes aside from the addition of malicious code.
Attackers may also impersonate legitimate projects and companies by using similar names or legal company type abbreviations. To conceal their malicious code, attackers often hide it within benign components of the project, appending it as a single line behind a long comment. This tactic makes the malicious code difficult to detect, especially when viewed in code editors with word wrap disabled.
Another method of compromise involves inviting victims to a fake job interview using an online conferencing platform and providing a link to a malicious website disguised as conferencing software. The downloaded software contains the first stage of the malware.
DeceptiveDevelopment primarily utilizes two malware families delivered in two stages as part of its operations. The initial phase, BeaverTail, comes in both JavaScript and native forms (coded in C++ with the Qt platform) and is distributed to the target under the guise of being a component of a project, a job application task, or as part of tampered remote conferencing tools like MiroTalk or FreeConference.
BeaverTail functions as a basic login theft tool, extracting browser databases that store saved logins, and as a conduit for the subsequent stage, InvisibleFerret. The latter, a Python-based malware, contains spyware and backdoor features, and can also download the legitimate AnyDesk software for post-compromise operations. The compromise chain, from the initial breach to data exfiltration and the deployment of AnyDesk, is illustrated in Figure 6.
Both BeaverTail and InvisibleFerret have been previously detailed by Unit 42, Group-IB, and Objective-See. Zscaler also conducted a parallel investigation corroborating these findings. Our analysis offers new insights and a comprehensive overview of the malicious activities.
BeaverTail, the infostealer and downloader utilized by DeceptiveDevelopment, exists in two versions – a JavaScript variant embedded in trojanized projects with simple obfuscation, and native versions disguised as conferencing software. Both versions share similar functionalities.
This malware targets Windows, Linux, and macOS systems with the goal of harvesting saved login details and cryptocurrency wallet information. It begins by obtaining the C&C IP address and port. The JavaScript version obfuscates the IP address and port using base64 encoding, while the native version stores this information in plaintext. BeaverTail searches for browser extensions from Chrome Web Store or Microsoft Edge Add-ons, targeting MetaMask, BNB Chain Wallet, Coinbase Wallet, and others. If found, it collects and exfiltrates .ldb and .log files from the extensions’ directories.
Additionally, BeaverTail seeks out the Solana keys stored in the user’s home directory and saved login information in specific locations on macOS and Linux systems. Each sample contains a unique victim ID for identification throughout the compromise chain. The stolen data, along with other system information, is uploaded to the C&C server, and a Python environment is downloaded to facilitate the execution of the next stage.
In August 2024, a new version of JavaScript BeaverTail was observed, which acted as a loader to download and execute the payload code from a remote server. This version targeted additional cryptocurrency wallet extensions and used a different obfuscation technique. The connection between this new JavaScript version and the native BeaverTail was evident from their similarities in targeting and techniques.
InvisibleFerret, on the other hand, is a modular Python malware with information theft and remote control capabilities. The malware comprises four modules: main (.npl file), payload (pay), browser (bow), and AnyDesk (adc). AnyDesk serves as the persistence mechanism for the malware, allowing attackers to execute InvisibleFerret at their discretion after gaining persistence.
Interestingly, most of the backdoor functionality of InvisibleFerret requires operator intervention or scripted behavior to send commands, decide on data exfiltration, and propagate the attack. The operator initiates the activation of backdoor components in all observed versions of InvisibleFerret, except for the automatic initial fingerprinting process.
Main Module:
The main module, initially named main, is the .npl file downloaded by BeaverTail from the C&C server and saved in the home directory. It is responsible for downloading and executing individual payload modules. Each module contains an XOR-encrypted and base64-encoded payload, along with code to decrypt and execute it via exec. The main module also contains the sType variable, representing the victim ID. Additionally, the main module downloads the payload module from /payload/
Payload Module:
The pay module has two parts – one collects system information and the other serves as a backdoor. The first part gathers the user’s UUID, OS type, PC name, username, system version, local IP address, public IP address, and geolocation information, which is then uploaded to the /keys API endpoint. The second part acts as a TCP backdoor and reverse shell, accepting remote commands from the C&C server. It may use various ports for communication. Under Windows, the second part enables a keylogger and clipboard stealer to collect keypresses and clipboard changes. It then executes backdoor functionality with eight commands.
Overall, InvisibleFerret’s modules work together to enable remote control and data exfiltration, with the main module handling module execution and the payload module collecting system information and acting as a backdoor.
· Stops operation and eliminates the compromise.
· Sends an empty response on non-Windows operating systems where keylogging is disabled.
· Reports the OS name and get browse to the server.
· Includes six subcommands: upload_all_dir, upload_dir, upload_file, upload_find_all_dir, upload_find_recursive, and upload_find.
Searches only the specified directory using the sfind command, which is similar to sfinda but starts the search in the current directory. If not, the script downloads anydesk.exe from the C&C server (http://
After completing these tasks, the AnyDesk process is terminated and restarted to load the updated configuration. Finally, the adc module attempts to delete itself by calling the os.remove function on itself.
InvisibleFerret update
A newer version of InvisibleFerret was found with significant changes, in use since at least August 2024. It is no longer split into separate modules but exists as a single large script file, still capable of selectively installing the browser and AnyDesk modules. There are also minor code adjustments for enhanced macOS support, such as gathering the username and hostname of the computer.
Another change observed is the inclusion of an identifier called gType, alongside sType. It serves as a secondary victim/campaign identifier when downloading modules from the C&C server (e.g.,
This updated version of InvisibleFerret has introduced a new backdoor command, ssh_zcp, which can extract data from browser extensions and password managers through Telegram and FTP.
With this new command, InvisibleFerret first identifies and collects data from 88 browser extensions for Chrome, Brave, and Edge browsers, storing it in a staging folder in the system’s temporary directory. The complete list of extensions can be found in the Appendix, and the code for data collection is displayed in Figure 18.
In addition to extension data, the command can extract information from various applications like Atomic and Exodus cryptocurrency wallets on all systems, as well as 1Password, Electrum, WinAuth, Proxifier4, and Dashlane on Windows, as depicted in Figure 19.
The extracted data is then archived and uploaded to a Telegram chat using the Telegram API with a bot token, and also to an FTP server. Once the upload is completed, InvisibleFerret removes both the staging folder and the archive.
Clipboard stealer module
In December 2024, a new version of InvisibleFerret was discovered, featuring an additional module named mlip, downloaded from the C&C endpoint /mclip/
Demonstrating an advancement in the operators’ technical capabilities, this module’s keylogging and clipboard stealing functionality is limited to two processes, chrome.exe and brave.exe, as opposed to earlier versions that logged all keystrokes. The collected data is uploaded to a new API endpoint, /api/clip.
Network infrastructure
DeceptiveDevelopment’s network infrastructure comprises dedicated servers hosted by commercial providers like RouterHosting (now Cloudzy), Stark Industries Solutions, and Pier7ASN. The server API, built in Node.js, includes nine endpoints, as listed in Table 4.
Most C&C communication occurs over ports 1224 or 1244 (occasionally 80 or 3000) for HTTP communication, and 1245 (occasionally 80, 2245, 3001, 5000, or 5001) for backdoor C&C communication over TCP sockets. All client-to-C&C communication, except Python environment downloads, includes the campaign ID. For InvisibleFerret downloads, the ID is appended to the URL in the GET request. For the purpose of data exfiltration, the ID is included in the POST request under the type field. This helps in identifying network traffic and determining the specific sample and campaign it is associated with.
The alphanumeric campaign IDs (sType and gType values) we have observed do not appear to directly correlate with the campaign. Prior to the introduction of gType, some sType values were base64 strings containing variations of the word team and numbers, such as 5Team9 and 7tEaM;. Following the introduction of gType, most observed values for both types were purely numeric, without the use of base64.
Conclusion
The DeceptiveDevelopment cluster is a new addition to the existing array of money-making schemes used by North Korea-aligned groups and aligns with the trend of shifting focus from traditional money to cryptocurrencies. Our research shows the evolution of this cluster from basic tools and techniques to advanced malware, as well as refined methods to attract victims and deploy the malware. Any online job-hunting or freelancing platform is at risk of being exploited for distributing malware by fraudulent recruiters. We continue to monitor significant activity related to this campaign and anticipate further innovation and targeting of cryptocurrency users by DeceptiveDevelopment.
For inquiries regarding our research published on WeLiveSecurity, please reach out to us at threatintel@eset.com.ESET Research provides private APT intelligence reports and data feeds. For inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
A detailed list of indicators of compromise (IoCs) and samples can be accessed in our GitHub repository.
Files
| SHA-1 | Filename | Detection | Description |
| 48E75D6E2BDB2B00ECBF |
FCCCall.exe | Win64/DeceptiveDevelopment.A | Trojanized conferencing app – native BeaverTail. |
| EC8B6A0A7A7407CA3CD1 |
pay.py | Python/DeceptiveDevelopment.B | InvisibleFerret payload module. |
| 3F8EF8649E6B9162CFB0 |
bow.py | Python/DeceptiveDevelopment.C | InvisibleFerret browser module. |
| F6517B68F8317504FDCD |
pay_u2GgOA8.py | Python/DeceptiveDevelopment.B | InvisibleFerret new payload module. |
| 01C0D61BFB4C8269CA56 |
setupTest.js | JS/Spy.DeceptiveDevelopment.A | BeaverTail. |
| 2E3E1B95E22E4A8F4C75 |
tailwind.config |
JS/Spy.DeceptiveDevelopment.A | BeaverTail. |
| 7C8724B75BF7A9B8F27F |
conf.ps1 | PowerShell/DeceptiveDevelopment.A | AnyDesk configuration PowerShell script. |
| 5F5D3A86437082FA512B |
adc.py | Python/DeceptiveDevelopment.A | InvisibleFerret AnyDesk module. |
| 7C5B2CAFAEABBCEB9765 |
bow.py | Python/DeceptiveDevelopment.A | InvisibleFerret browser module. |
| BA1A54F4FFA42765232B |
pay.py | Python/DeceptiveDevelopment.A | InvisibleFerret payload module. |
| 6F049D8A0723DF10144C |
.npl | Python/DeceptiveDevelopment.A | InvisibleFerret loader module. |
| 8FECA3F5143D15437025 |
admin.model.js | JS/Spy.DeceptiveDevelopment.A | BeaverTail. |
| 380BD7EDA453487CF115 |
run.js | JS/Spy.DeceptiveDevelopment.A | BeaverTail. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 95.164.17[.]24 | N/A | STARK INDUSTRIES SOLUTIONS LTD | 2024‑06‑06 | BeaverTail/InvisibleFerret C&C and staging server. |
| 185.235.241[.]208 | N/A | STARK INDUSTRIES SOLUTIONS LTD | 2021‑04‑12 | BeaverTail/InvisibleFerret C&C and staging server. |
| 147.124.214[.]129 | N/A | Majestic Hosting Solutions, LLC | 2024‑03‑22 | BeaverTail/InvisibleFerret C&C and staging server. |
| 23.106.253[.]194 | N/A | LEASEWEB SINGAPORE PTE. | 2024‑05‑28 | BeaverTail/InvisibleFerret C&C and staging server. |
| 147.124.214[.]237 | N/A | Majestic Hosting Solutions, LLC | 2023‑01‑28 | BeaverTail/InvisibleFerret C&C and staging server. |
| 67.203.7[.]171 | N/A | Amaze Internet Services | 2024‑02‑14 | BeaverTail/InvisibleFerret C&C and staging server. |
| 45.61.131[.]218 | N/A | RouterHosting LLC | 2024‑01‑22 | BeaverTail/InvisibleFerret C&C and staging server. |
| 135.125.248[.]56 | N/A | OVH SAS | 2023‑06‑30 | BeaverTail/InvisibleFerret C&C and staging server. |
MITRE ATT&CK techniques
This table was built using version 16 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server | The attackers rent out infrastructure for C&C and staging servers. |
| T1587.001 | Develop Capabilities: Malware | The attackers develop the BeaverTail and InvisibleFerret malware. | |
| T1585.001 | Establish Accounts: Social Media Accounts | The attackers create fake social media accounts, pretending to be recruiters. | |
| T1608.001 | Stage Capabilities: Upload Malware | InvisibleFerret modules are uploaded to staging servers, from where they are downloaded to victimized systems. | |
| Initial Access | T1566.003 | Phishing: Spearphishing via Service | Spearphishing via job-hunting and freelancing platforms. |
| Execution | T1059.006 | Command-Line Interface: Python | InvisibleFerret is written in Python. |
| T1059.007 | Command-Line Interface: JavaScript/JScript | BeaverTail has a variant written in JavaScript. | |
| T1204.002 | User Execution: Malicious File | Initial compromise is triggered by the victim executing a trojanized project containing the BeaverTail malware. | |
| T1059.003 | Command-Line Interface: Windows Command Shell | InvisibleFerret’s remote shell functionality allows access to the Windows Command Shell. | |
| Persistence | T1133 | External Remote Services | Persistence is achieved by installing and configuring the AnyDesk remote access tool. |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | The JavaScript variant of BeaverTail uses code obfuscation. C&C server addresses and other configuration data are also encrypted/encoded. |
| T1564.001 | Hide Artifacts: Hidden Files and Directories | InvisibleFerret files are dropped to disk with the hidden attribute. | |
| T1564.003 | Hide Artifacts: Hidden Window | InvisibleFerret creates new processes with their windows hidden. | |
| T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File | InvisibleFerret payloads are encrypted and have to be decrypted before execution. | |
| Credential Access | T1555.001 | Credentials from Password Stores: Keychain | Keychain data is exfiltrated by both BeaverTail and InvisibleFerret. |
| Discovery | T1010 | Application Window Discovery | The InvisibleFerret keylogger collects the name of the currently active window. |
| T1217 | Browser Bookmark Discovery | Credentials and other data stored by browsers are exfiltrated by InvisibleFerret. | |
| T1083 | File and Directory Discovery | The InvisibleFerret backdoor can browse the filesystem and exfiltrate files. | |
| T1082 | System Information Discovery | System information is collected by both BeaverTail and InvisibleFerret. | |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol | AnyDesk is used by InvisibleFerret to achieve persistence and allow remote attacker access. |
| Collection | T1056.001 | Input Capture: Keylogging | InvisibleFerret contains keylogger functionality. |
| T1560.002 | Archive Collected Data: Archive via Library | Data exfiltrated using InvisibleFerret can be archived using the py7zr and pyzipper Python packages. | |
| T1119 | Automated Collection | Both BeaverTail and InvisibleFerret exfiltrate some data automatically. | |
| T1005 | Data from Local System | Both BeaverTail and InvisibleFerret exfiltrate data from the local system. | |
| T1025 | Data from Removable Media | InvisibleFerret scans removable media for files to exfiltrate. | |
| T1074.001 | Data Staged: Local Data Staging | InvisibleFerret copies browser databases to the temp folder prior to credential extraction. |



