ESET researchers have recently tracked the activities of the CosmicBeetle threat actor, focusing on its new ScRansom ransomware and its connections to other established ransomware groups.
CosmicBeetle has been actively targeting SMBs worldwide with ScRansom, replacing its previous Scarab ransomware with this newer, continually improved version. The threat actor has also been observed using the leaked LockBit builder to impersonate the infamous LockBit ransomware gang in ransom notes and on leak sites.
There is medium confidence that CosmicBeetle may be affiliated with RansomHub, a new ransomware gang that has been increasingly active since March 2024. The blog post provides an in-depth analysis of CosmicBeetle’s activities over the past year, including insights into the ScRansom ransomware.
Key points from the blog post include:
- CosmicBeetle continues to distribute ScRansom in 2024, targeting SMBs globally.
- ScRansom may result in some encrypted files being permanently lost, despite the decryption key working as intended.
- CosmicBeetle has attempted to capitalize on the reputation of LockBit by impersonating the gang.
- There is a possibility that CosmicBeetle is affiliated with RansomHub, a rising ransomware-as-a-service gang.
- CosmicBeetle exploits older vulnerabilities to breach SMBs worldwide.
The blog post provides an overview of CosmicBeetle, its use of custom Delphi tools known as Spacecolon, and the evolution of its ScRansom ransomware. It also discusses the attribution of ScRansom to CosmicBeetle based on code similarities and telemetry data.
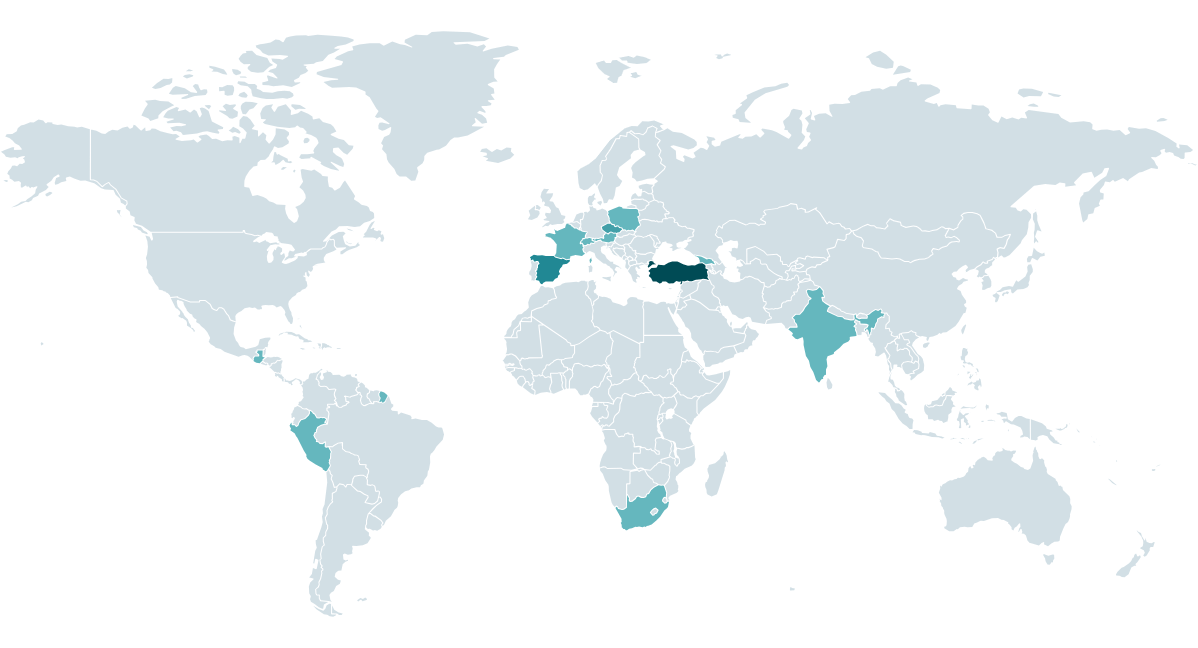
CosmicBeetle primarily targets SMBs through brute-force methods and exploits various vulnerabilities to gain initial access. The threat actor focuses on industries with weak patch management processes, making them more susceptible to attacks. The leak site of CosmicBeetle is shown to be unreliable and inconsistent, as demonstrated by ESET telemetry data. Figure 1 displays the victims of CosmicBeetle according to ESET telemetry, with attacks observed on various SMBs in different verticals such as manufacturing, pharmaceuticals, legal, education, healthcare, technology, hospitality leisure, financial services, and regional government.
The ransom notes dropped by ScRansom do not usually assign a name to the ransomware, except for the brief branding of NONAME. CosmicBeetle primarily relies on email and qTox, an instant messaging application utilizing the Tox protocol for communication. The ransomware’s custom name is NONAME, but for the purposes of this blogpost, it will continue to be referred to as ScRansom.
In September 2023, CosmicBeetle established a dedicated leak site on Tor named NONAME, which closely resembles LockBit’s leak site. This imitation continued further with the domain lockbitblog[.]info, mimicking the official LockBit leak site. A sample of the leaked LockBit 3.0 builder uploaded to VirusTotal in August 2024 from Türkiye contained a ransom message in Turkish, linked to CosmicBeetle.
The connection to RansomHub was also observed, with CosmicBeetle attempting to compromise a manufacturing company in India with ScRansom and using RansomHub’s EDR killer tools. The technical analysis reveals that ScRansom is written in Delphi, with ongoing development and a structured GUI typical for Delphi applications.
Overall, the behavior of CosmicBeetle in impersonating other ransomware gangs and utilizing leaked builders suggests a lack of originality and reliance on established ransomware tactics. The older samples, often referred to as "Static" by developers, require user interaction for encryption to occur. While this may seem like a complication, it may have contributed to ScRansom evading detection for some time, as running these samples in analysis sandboxes does not show any malicious activity. Launching such an encryptor requires the threat actor to have access to the victim’s screen and manipulate their mouse. This is not the first time CosmicBeetle has used this approach, as ScHackTool also requires manual interaction on the victim’s machine. The method used by CosmicBeetle to achieve this goal is not entirely clear, but it is speculated that VPN access with stolen credentials and RDP is the most likely scenario.
CosmicBeetle has also experimented with a variant called "SSH" which encrypts files over FTP instead of locally. Newer builds of ScRansom use automation to simulate clicking the correct buttons from code. These automated builds, known as "Auto," are typically bundled inside an MSI installer along with tools to delete shadow copies. The GUI is hidden by default, with the most recent version shown in Figure 6.
The ScRansom GUI, with multiple buttons, some of which are non-functional, is characteristic of CosmicBeetle. Despite the complexity of the GUI, the functionality is straightforward. ScRansom encrypts files on all types of drives based on a predefined list of extensions. The encryption process can be modified through different modes, including FAST, FASTEST, SLOW, FULL, and ERASE. The ERASE mode replaces the contents of files with a constant value, making them unrecoverable. ScRansom also terminates various processes and services and has a separate tool called ScKill for killing processes.
The initial samples of ScRansom used symmetric encryption with AES-CTR-128, but the encryption scheme was updated in December 2023. The new scheme involves generating an AES key (ProtectionKey) and an RSA-1024 key pair (RunKeyPair). Each file is encrypted using an AES key (FileKey), and additional data is appended to the file. Decryption IDs are stored in a text file and ransom note, and the filename is encoded and given the .Encrypted extension.
A decryptor has been obtained for the recent encryption scheme, which requires the ProtectionKey and Decryption ID. Victims who pay the ransom must collect all Decryption IDs from all machines, obtain ProtectionKeys from CosmicBeetle, and run the decryptor on each machine to recover their files. Some victims have reported difficulty recovering all files, possibly due to missing Decryption IDs, incomplete ProtectionKeys, or files permanently destroyed by the ERASE encryption mode. The decryption method used by an inexperienced ransomware threat actor is common. Established criminal groups opt for a simpler decryption process to ensure successful decryption, enhance their reputation, and increase the likelihood of victims paying the ransom. Typically, a decryptor is integrated with the encryptor, simplifying the decryption process for the victim as the key is embedded in the binary. Furthermore, a single key can decrypt all files, regardless of their location in the victim’s network.
In our analysis of CosmicBeetle’s activities over the past year, we observed a shift from Scarab ransomware to a new custom ransomware family called ScRansom. It appears that CosmicBeetle attempted to leverage LockBit’s reputation to mask potential issues with their ransomware and improve payment rates. While there were instances of deploying LockBit samples using the leaked builder, CosmicBeetle primarily focused on developing and refining ScRansom.
Recent observations show the deployment of both ScRansom and RansomHub payloads on the same machine within a short timeframe, indicating a potential affiliation with RansomHub. The continuous development of ScRansom introduces complexities that may lead to decryption errors, making file restoration uncertain. Even with a working decryptor and all necessary keys from the threat actor, some files may be permanently damaged. Decryption in the best-case scenario is expected to be lengthy and intricate.
For further inquiries regarding our research on WeLiveSecurity, please reach out to threatintel@eset.com. ESET Research also provides private APT intelligence reports and data feeds, and inquiries about this service can be directed to the ESET Threat Intelligence page.
Most Recent Configuration for Filename Masks to Encrypt
Below are the file extensions that are currently being encrypted:
- *._ms
- *.0001
- *.001
- *.002
- *.003
- *.004
- *.005
- *.006
- *.007
- *.008
- *.1*
- *.2*
- *.3*
- *.3dm
- *.3dmbak
- *.3ds
- …
- *ibdata
These are the specific file types that are currently included in the encryption process. If there are any additional file types that need to be encrypted, please let us know.