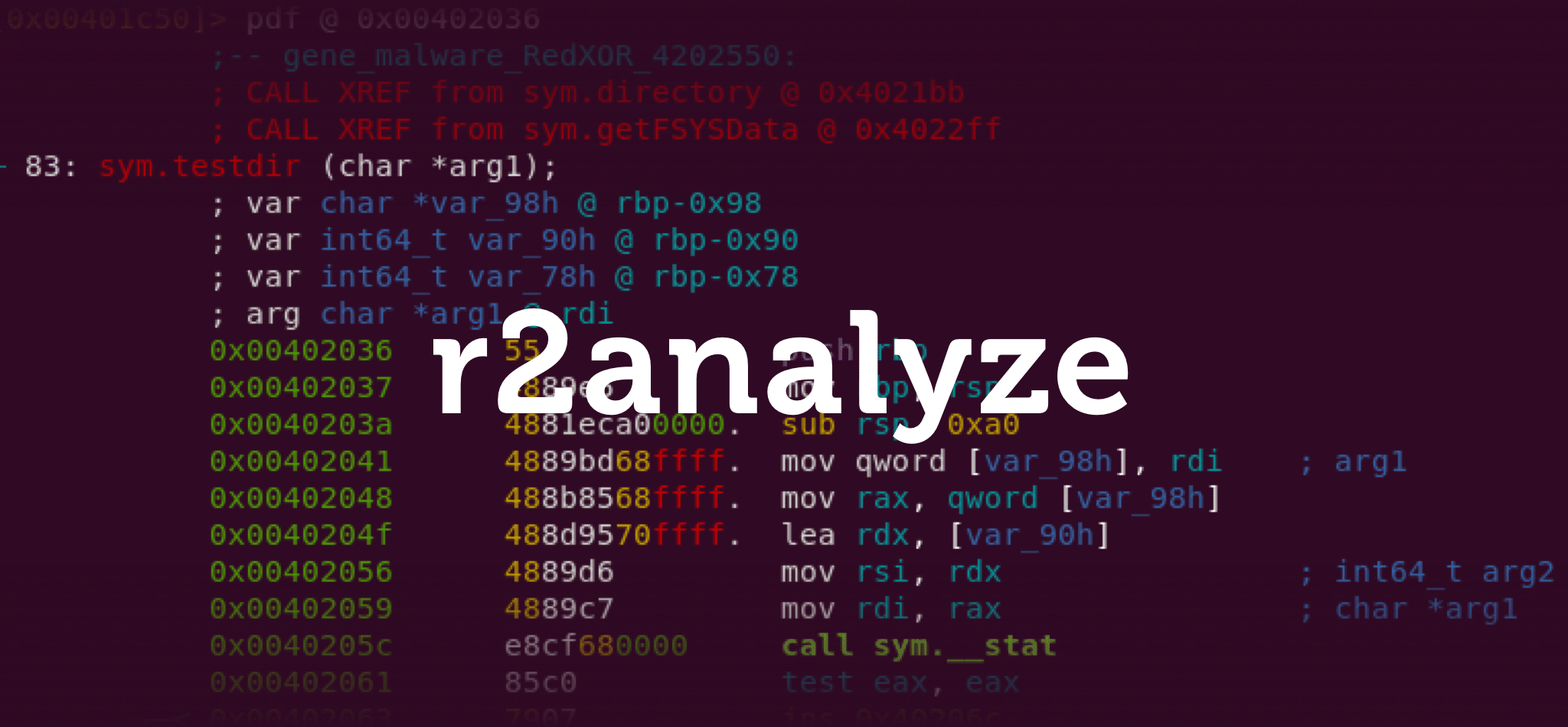
Radare Plugin is Here for Intezer Community
When you find yourself reverse engineering code as part of an incident response team, your main goal is to quickly gather information about the type of threat you are facing. […]

When you find yourself reverse engineering code as part of an incident response team, your main goal is to quickly gather information about the type of threat you are facing. […]
October 2023 Update: Intezer analyzes all URLs that we collect as evidence for automated alert triage, which now includes detecting and extracting QR codes for phishing email investigations. At Intezer, […]

Threat actors have a variety of tools and techniques at their disposal for cyber attacks, including malware-as-a-service, open-source tools, red team or admin tools. There are also legitimate tools that […]

Analyzing suspicious URLs on an individual basis can be tricky, but when you’re facing a large volume of potentially malicious URLs then other approaches that leverage automation (like machine learning) […]

Are you tired of being overwhelmed by never-ending alerts and struggling with skill gaps in your security operations team? Intezer’s AI-powered automation is here to save the day! By leveraging […]

Manufacturing companies are rapidly embracing digital transformation, which has led to increased production. However, this shift also exposes them to higher cyber risks due to the reliance on robust online […]

Welcome to the world of telecommunications, where staying connected 24/7 is crucial in our interconnected society. The telecom industry relies on a complex infrastructure involving satellites, internet providers, mobile phones, […]

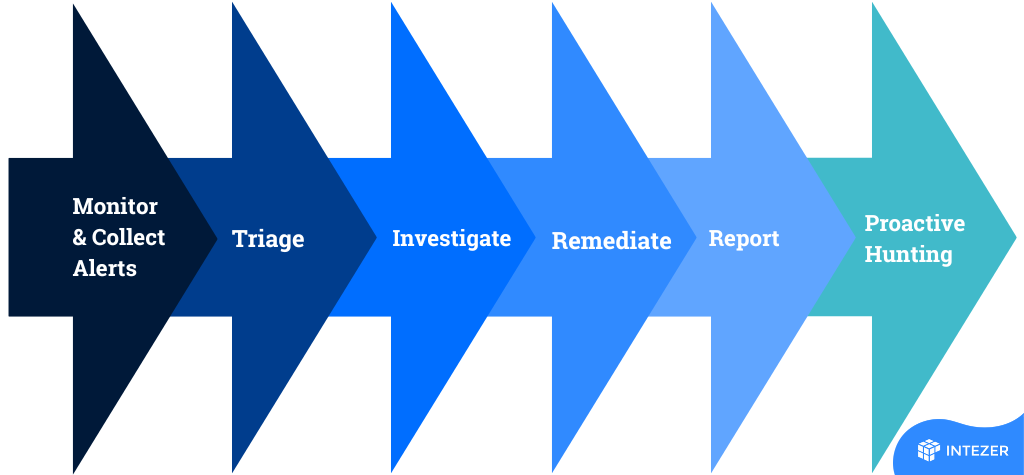
TL;DR – Intezer is revolutionizing incident response for security teams by automating the entire process with sandboxes and file analysis, offering an affordable alternative to in-house Tier 1 teams or […]
Are you considering replacing your Managed Detection and Response (MDR) service? MDR services are essential for keeping your business’ cybersecurity effective, but there are instances where a replacement may be […]

Welcome to the world of cybersecurity, where threats and vulnerabilities are on the rise, and businesses need all the help they can get to keep their networks and data safe. […]