In 2024, ESET researchers discovered several malicious tools in the systems used by Kurdish and Iraqi government officials. The APT group behind the attacks is BladedFeline, an Iranian threat actor that has been active since at least 2017, when it compromised officials within the Kurdistan Regional Government (KRG). This group develops malware for maintaining and expanding access within organizations in Iraq and the KRG. While this is our first blog post covering BladedFeline, we discovered the group in 2023, after it targeted Kurdish diplomatic officials with the Shahmaran backdoor, and previously reported on its activities in ESET APT Activity reports Q4 2023-Q1 2024 and Q2 2024-Q3 2024.
The array of tools utilized in the recent campaign shows that since deploying Shahmaran, BladedFeline has continued to develop its arsenal. We found two reverse tunnels, a variety of supplementary tools, and most notably, a backdoor that we named Whisper and a malicious IIS module we dubbed PrimeCache. Whisper is a backdoor that logs into a compromised webmail account on a Microsoft Exchange server and uses it to communicate with the attackers via email attachments. PrimeCache also serves as a backdoor: it is a malicious IIS module related to what we referred to as Group 2 in our 2021 paper Anatomy of native IIS malware. Significantly, PrimeCache also bears similarities to the RDAT backdoor used by the Iran-aligned OilRig APT group.
Based on these code similarities, as well as on further evidence presented in this blog post, we assess with medium confidence that BladedFeline is a subgroup of OilRig, an Iran-aligned APT group going after governments and businesses in the Middle East. We have previously reported on other activity linked to OilRig. To avoid confusion, we have since refined our OilRig tracking, and we now track both of those operations under a separate subgroup – Lyceum – within OilRig.
BladedFeline has worked consistently to maintain illicit access to Kurdish diplomatic officials, while simultaneously exploiting a regional telecommunications provider in Uzbekistan, and developing and maintaining access to officials in the government of Iraq. This blog post details the technical aspects of the initial implants delivered to BladedFeline’s targets, the links between the victims, and lays the groundwork for associating this subgroup with OilRig.
Key points of the blog post:
- BladedFeline compromised officials within the Kurdistan Regional Government at least as early as 2017.
- The initial implants used there can be traced back to OilRig.
- We discovered BladedFeline after its operators compromised Kurdish diplomatic officials with the group’s Shahmaran signature backdoor in 2023.
- This APT group has also infiltrated high-ranking officials within the government of Iraq.
- We assess with medium confidence that BladedFeline is a subgroup within OilRig.
- We analyze two reverse tunnels (Laret and Pinar), a backdoor (Whisper), a malicious IIS module (PrimeCache), and various supplementary tools.
BladedFeline overview
BladedFeline is an Iran-aligned cyberespionage group, active since at least 2017 according to ESET telemetry. We discovered the group in 2023 when it deployed its Shahmaran backdoor against Kurdish diplomatic officials. Shahmaran, named after a mythical half-snake, half-woman creature from Iranian folklore, is a 64-bit portable executable that we found in the target’s Startup directory. This simple backdoor doesn’t use any compression or encryption for network communications. After checking in with the C&C server, the backdoor executes any operator commands provided, which include uploading and downloading additional files, requesting specific file attributes and providing file and directory manipulation API.
As evidenced by the campaign toolset we describe in this blog post; since deploying Shahmaran, BladedFeline has continued to develop its malware in order to retain and even further extend its access to the KRG and to high levels within the government of Iraq (GOI). We uncovered the campaign in 2024 after finding BladedFeline’s Whisper backdoor, PrimeCache IIS backdoor, and a set of post-compromise tools in the networks of Kurdish diplomatic officials, Iraqi government officials, and a regional telecommunications provider in Uzbekistan.
We detected and collected one version of Whisper and found another on VirusTotal, uploaded by a user in Iraq. They are virtually identical, and we were able to determine the likely identity of the VirusTotal uploader, based on data in the Whisper sample and other samples uploaded under the same submitter ID. PrimeCache, Flog (a webshell), and Hawking Listener (an early-stage implant that listens on a specified port) were all uploaded to VirusTotal by the same submitter ID who uploaded the Whisper samples. Based on the Whisper link and the close timeframe (both were uploaded within a matter of minutes) we believe it was deployed by BladedFeline to a victim in Iraq’s government. Some of the tools mentioned below in the Timeline are discussed later in the report (e.g., Slippery Snakelet).
Timeline
2017-09-21 ● VideoSRV reverse shell on KRG system
|
2018-01-30 ● RDAT backdoor on KRG system
|
2019-07-09 ● Custom Plink on KRG system
|
2021-05-01 ● Sheep Tunneler on KRG system
|
2023-01-23 ● LSASS dumped on KRG system
|
2023-02-01 ● Shahmaran backdoor on KRG system
|
2023-03-25 ● First victim targeted at a telecommunications company in Uzbekistan
|
2023-06-12 ● Shahmaran version 2 on KRG system for access maintenance
|
2023-12-14 ● BladedFeline operators executing CLI commands on KRG system
|
2023-12-16 ● Slippery Snakelet backdoor on KRG system
|
2023-12-20 ● P.S.
2023-12-20 ● PsExec on KRG system
|
2024-01-07 ● Whisper backdoor on KRG system
|
2024-02-01 ● Laret reverse tunnel on KRG system
|
2024-02-20 ● Pinar reverse tunnel on KRG system
|
2024-02-29 ● PrimeCache malicious IIS module uploaded to VirusTotal
|
2024-03-11 ● Whisper version 2, Flog, and Hawking Listener uploaded to VirusTotal
Attribution
Our attribution of this campaign to BladedFeline is based on the following:
– The campaign targets members of the KRG, as have previous attacks conducted by BladedFeline.
– The original attack activity targeting the KRG organization allowed us to identify successive malware, as BladedFeline has attempted to maintain and expand access to the organization.
– Further analysis of the attacks led us to identify the telecommunications victim in Uzbekistan.
– At the same time, looking into the Whisper backdoor helped us identify the GOI victim.
We assess that BladedFeline is targeting the KRG and the GOI for cyberespionage purposes, with an eye toward maintaining strategic access to high-ranking officials in both governmental entities. The KRG’s diplomatic relationship with Western nations, coupled with the oil reserves in the Kurdistan region, makes it an enticing target for Iran-aligned threat actors to spy on and potentially manipulate. In Iraq, these threat actors are most probably trying to counter the influence of Western governments following the US invasion and occupation of the country.
We believe with medium confidence that BladedFeline is a subgroup of OilRig:
– As does OilRig, BladedFeline targets organizations in the Middle East with the purpose of cyberespionage.
– We have found OilRig tools (VideoSRV and RDAT) in a compromised KRG system.
– BladedFeline’s malicious IIS module PrimeCache shares code similarities with OilRig’s RDAT.
BladedFeline is not the only subgroup of OilRig that we are monitoring: we have already been tracking Lyceum, also known as HEXANE or Storm-0133, as another OilRig subgroup. Lyceum focuses on targeting various Israeli organizations, including governmental and local governmental entities and organizations in healthcare. Major tools we attribute to Lyceum include DanBot, the Shark, Milan, and Marlin backdoors, Solar and Mango, OilForceGTX, and a variety of downloaders using legitimate cloud services for C&C communication.
We will continue to use the name OilRig to refer to the parent group, also known as APT34 or Hazel Sandstorm (formerly EUROPIUM). OilRig is a cyberespionage group that has been active since at least 2014 and is commonly believed to be based in Iran. The group targets Middle Eastern governments and a variety of business verticals, including chemical, energy, finance, and telecommunications. Notable OilRig campaigns include the 2018 and 2019 DNSpionage campaign, targeting victims in Lebanon and the United Arab Emirates; the 2019–2020 HardPass campaign, using LinkedIn to target Middle Eastern victims in the energy and government sectors; the 2020 attack against a telecommunications organization in the Middle East using the RDAT backdoor; and the 2023 attacks targeting organizations in the Middle East with the PowerExchange and MrPerfectionManager backdoors.
OilRig tools used by BladedFeline
We have found two OilRig tools on the KRG machines compromised by BladedFeline.
RDAT
We discovered a previously unreported version of the OilRig backdoor RDAT on two KRG victim systems. Analyzing RDAT, we found that the operational flow, compilation timestamp, and file write time align with OilRig activity and targeting, particularly with regard to the group’s 2017 activity. We observed a file with an SHA-1 and a path of C:\Windows\System32\LogonUl.exe on both systems. The PDB path also corroborates that this binary is RDAT. To date, we have only ever observed RDAT in use by OilRig. Moreover, we have not seen any custom implant sharing between OilRig and other Middle Eastern groups, and it seldom occurs between Iran-aligned threat actors.
Further bolstering the case that BladedFeline is an OilRig subgroup, as with Lyceum, is the analysis linking RDAT with PrimeCache, a malicious IIS module that was uploaded to VirusTotal presumably by the GOI victim. This link is explored in more depth in the Links with OilRig section of the blogpost.
VideoSRV
One additional data point on the OilRig and BladedFeline connection is a reverse shell deployed to one of the KRG victims (September 21st, 2017) prior to RDAT getting dropped on the same system (January 30th, 2018). VideoSRV, so named for its filename videosrv.exe, has the PDB string, which bears some similarities to the RDAT PDB string.
Technical analysis
Initial access
It is still unclear how BladedFeline is developing access to its victims. What we know is that in the case of the KRG victims, the threat actors obtained access at least as far back as 2017 and have maintained it ever since. As for the GOI victims, we suspect that the group exploited a vulnerability in an application on an internet-facing web server, which allowed them to deploy the Flog webshell.
Toolset
PrimeCache – malicious IIS module
PrimeCache, whose name we derived from the RTTI AVRSAPrimeSelector and its filename (cachehttp.dll), is a passive backdoor implemented as a native IIS module with an internal name of HttpModule.dll. It was uploaded to VirusTotal by the same user who uploaded one of the Whisper backdoor samples. It is a 64-bit C++ DLL with a compilation timestamp of 2023-05-14 06:55:52 and has a minimized PDB string of just HttpModule.pdb. It only has one export: RegisterModule.
PrimeCache serves as a replacement for a series of unattributed IIS backdoors previously identified as Group 2 (simple IIS backdoors) in our 2021 blogpost, Anatomy of native IIS malware. These original samples were sourced from VirusTotal uploads by users from Bahrain, Israel, and Pakistan between 2018 and 2020. Given the geographical locations of the suspected victims, there is a potential connection to BladedFeline – or more broadly, OilRig – activities.
Main functionality
The core functionality of PrimeCache resides in the CGlobalModule::OnGlobalPreBeginRequest handler, a departure from previous versions that utilized the CHttpModule::OnBeginRequest handler. PrimeCache filters incoming HTTP requests, specifically processing those from BladedFeline operators, identified by a cookie header with the format:
F=<command_ID>,<param>;
It’s important to note that this value can either stand alone or be embedded within a longer cookie, enclosed by semicolon characters.
The backdoor operates in a distinct manner, with each action divided into multiple requests, a new approach compared to our 2021 analysis. Initially, the BladedFeline operator sends individual requests for each parameter, which are stored in a global structure. Subsequently, another request triggers the backdoor command. PrimeCache then utilizes the previously received parameters to execute the specified action and clears the cached parameters.
Operator commands
There are three types of requests that the backdoor can receive, as outlined in Table 1.
Table 1. PrimeCache operator commands
| <command_ID> | Parameter | Description |
| 1 | Format: <key>=<value> | Clears the list of previously stored parameters and adds the new value. Most parameters are encrypted; see Encryption below. |
| 0 | Not used. | Triggers the backdoor action, using previously transmitted backdoor parameters. |
| Other | Format: <key>=<value> | Adds the specified value to the list of stored parameters (doesn’t clear the list). Most parameters are encrypted; see Encryption below. |
Upon triggering the action (via <command_ID>=0), PrimeCache executes an action based on the received parameters, as depicted in Table 2. It’s important to note:
The PrimeCache action is an operator command (OpCom) a, the session key is OpCom k, binary data is OpCom b, and the filename is OpCom f.
Table 2. PrimeCache post-operator command actions
| PrimeCache action | Session key | Binary data | Filename | Command description | Return value |
| r | RSA-encrypted session key | AES-encrypted command line | Null | Runs the specified command via popen. | Command output |
| r2 | Runs the specified command via CreateProcessW. | ||||
| r3 | (Presumably) runs the specified command by sending it to another (unknown) process via the named pipe \\.\pipe\iis, then reads (presumably) the command output from the same pipe. | ||||
| u | AES-encrypted file content | Local filename | Creates a local file with the specified name and content. | OK | |
| d | Null | Exfiltrates the given file from the compromised IIS server. | File content |
Encryption
Similar to its predecessors, PrimeCache employs both RSA and AES-CBC for C&C communication. The parameters and return values are consistently AES-CBC encrypted using the session key and then base64 encoded. The session key undergoes RSA encryption, with the backdoor containing a hardcoded private and public RSA key (non-pair) to facilitate bidirectional communication.
The encryption and decryption operations are managed using a statically linked Crypto++ library.
C&C communications
Operator commands are conveyed in the cookie header (a deviation from previous versions that utilized the URL or HTTP request body). PrimeCache responses are included in the HTTP response body. When exfiltrating a file, the Content-Type header is set to attachment, aligning with the functionality of prior versions.
The predecessors of PrimeCache also utilized a similar encryption scheme and parameter names (a, c, f, k), all sent to the backdoor in a single request. The supported commands included r, u, and d.
Links with OilRig
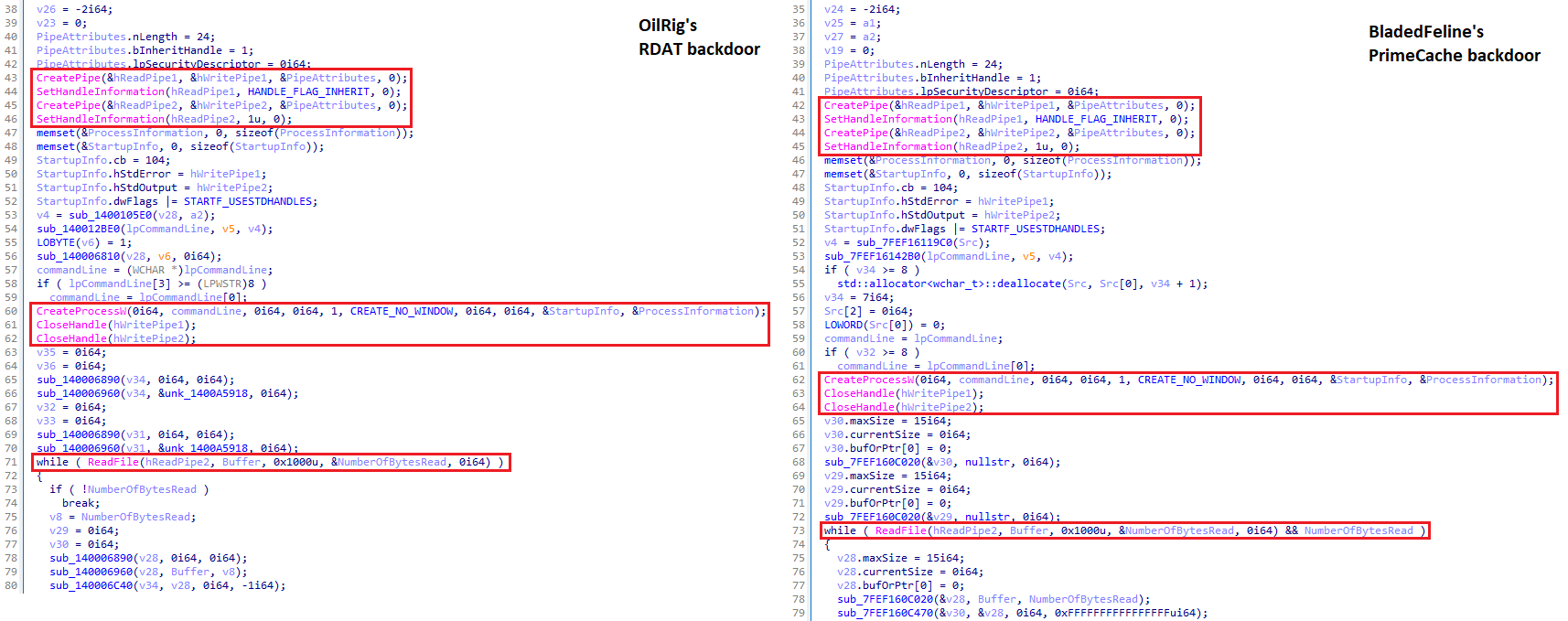
Upon comparing PrimeCache with RDAT, as detailed in the RDAT attribution subsection, several similarities emerge, reinforcing the notion that BladedFeline is a subset of OilRig.
- Both RDAT and PrimeCache utilize the Crypto++ library and parse backdoor commands using the regular expression [^,]+.
- The payload attempts to parse the decrypted cleartext using the regular expression [^,]+ to extract the command value and arguments separated by commas.
- They share a function, depicted in Figure 1, that executes a shell command and retrieves the output, a feature exclusive to these two malware pieces within our dataset.
Whisper backdoor
Whisper, a 32-bit Windows binary coded in C#/.NET, is dubbed after its PDB strings G:\csharp\Whisper_Trojan_winform\Whisper_Trojan_winform\Whisper_Trojan_winform\obj\Release\Veaty.pdb and Z:\csharp\Whisper_Trojan_winform_for_release\Whisper_Trojan_winform\Whisper_Trojan_winform\obj\Release\Veaty.pdb. The attackers utilize a Microsoft Exchange server to communicate, sending email attachments through a compromised webmail account. We have identified two versions of the backdoor: one was detected and gathered, while the other was uploaded to VirusTotal from Iraq. Although these samples are nearly identical, we were able to deduce the likely identity of the VirusTotal uploader based on data within the Whisper sample and other samples uploaded by the same user.
Both versions of Whisper exhibit timestomped compilation timestamps (2090-04-11 23:38:14 and 2080-12-11 03:50:47) and are constructed using Costura, likely to ensure that the victim’s system utilizes the DLLs packaged with the binary rather than those in the Global Assembly Cache.
The operational workflow of Whisper involves multiple steps, including logging into compromised webmail accounts, checking for inbox rules, sending check-in email messages, fetching operator commands, and decrypting said commands. These steps are detailed in the subsequent paragraphs and illustrated in Figures 2 and 3. It is worth noting that Whisper is not the first instance where an OilRig subgroup has employed cloud services for its command and control protocol, as seen with Lyceum using email drafts for communication in 2022. To achieve this, the process begins by decoding the base64 encoded string containing the command, followed by decrypting the result using the .NET AES class with a 16-byte initialization vector and the encryption key specified in the configuration file (line 18, key=”enc_key” value=”cXdlcmFzZHp4Y3ZmZ2d0aGhsZGZvZ2g/bHZtZ2xrZyE=”). The decrypted commands are structured in the format
In the subsequent step, the system executes the backdoor commands and stores the results. These commands may involve actions like sending a file to the C&C server, where the data written to disk is encoded in base64 and saved in a specific format. Successful execution of this command returns a confirmation message specifying the file path where the data was written.
Additionally, there is a command to execute a PowerShell script, without any prefix, followed by appending Out-String. The output of this command is also saved in a base64-encoded format.
Finally, the process concludes by sending the command output via email to the C&C inbox, as per the details specified in the configuration file. This includes the sender’s email address, recipient’s email address, subject line, message body, and the attachment containing the output of the commands encrypted with the same encryption key mentioned earlier.
These steps are repeated in a loop, following the check-in schedule specified, until any changes are made to the hardcoded credentials in the configuration file. Laret and Pinar Configuration Variables
| Variable | Description | Example |
| Server | The IP address of the C&C server | 192.168.1.1 |
| Port | The port number for communication | 443 |
| ProxyType | Type of proxy to use | SOCKS5 |
| ProxyServer | Proxy server IP address | 192.168.1.2 |
| ProxyPort | Proxy server port number | 1080 |
| ProxyUsername | Username for proxy authentication | user123 |
| ProxyPassword | Password for proxy authentication | pass456 |
| ProxyDomain | Domain for proxy authentication | example.com |
The configuration file for Laret is named svchost.exe.config, and for Pinar, it is named updater.exe.config.
| Field | Description | Default value |
| ssh_host | C&C IP address. | N/A |
| ssh_port | 22 | |
| ssh_username | C&C username. | N/A |
| ssh_pass | C&C password. | N/A |
| local_port | 9666 | |
| process_file | File to execute before executing any reverse tunnel actions. | N/A |
| wait_time_minutes | Time to wait between check-ins with the C&C server. | 10f (271) |
| remote_port | Port number used for port forwarding. | 1234 |
To stop Hawking, operators simply need to send “stop” as the key in the QueryString with a non-null variable in the value. Hawking logs all interactions, runtime arguments, and command output to the file log.txt in its working directory.
P.S. Olala is a 32-bit .NET binary designed to execute PowerShell scripts, with its PDB path at G:\csharp\psExecuterService\ewsService\obj\Release\Olala.pdb. It does not accept any runtime arguments but uses the Run(ServiceBase[]) method of the .NET ServiceBase class to register itself as a service with the Service Control Manager for persistence. When called, it spawns a thread and executes the mainLoop function, which essentially executes the PowerShell script stored in %APPDATA%\Local\Microsoft\InputPersonalization\TrainedDataStore.ps1.
Unfortunately, the TrainedDataStore.ps1 scripts were not collected, but it is likely an executor of the Whisper backdoor or one of the reverse tunnels (Laret or Pinar). This flow (P.S. Olala → TrainedDataStore → Whisper/Laret/Pinar) is likely an elongated persistence chain aiming to maintain access.
Sheep Tunneler is a custom tunneling application observed in %APPDATA%\Local\Microsoft\Windows\Ringtones\RingService.exe and %APPDATA%\Local\Microsoft\Windows\Shell\mspsrv.exe. It can be executed in network tunneling mode (using the runtime argument “middle”) or connect back mode (using the arguments “cb
Whisper Protocol is a 64-bit Python-compiled Windows binary named Protocol.pdf.exe. It creates a folder in C:\ProgramData\VeeamUpdate and writes Whisper and its configuration file to that folder. It also copies itself to %APPDATA%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VeeamUpdate.lnk for persistence and executes Whisper before exiting gracefully.
In conclusion, BladedFeline is an advanced threat group targeting Iraqi and Kurdish governmental officials and organizations, likely a subgroup of OilRig. The group is expected to continue developing implants to maintain and expand access for cyberespionage purposes.
For inquiries about research published on WeLiveSecurity, contact threatintel@eset.com. ESET Research offers private APT intelligence reports and data feeds. If you have any questions regarding this service, feel free to check out the ESET Threat Intelligence page for more information.
IoCs
Files
| SHA-1 | Filename | Detection | Description |
| 01B99FF47EC6394753F9 |
Avamer.pdf.exe | Python/Trojan |
Python-compiled dropper for Spearal |
| 1C757ACCBC2755E83E53 |
Win_Updates.exe | MSIL/Agent.EUM | Spearal, a BladedFeline backdoor. |
| 272CF34E8DB2078A3170 |
scr8B45.ps1 | PowerShell/Trojan |
PowerShell script to install Spearal. |
| 37859E94086EC47B3665 |
ncms_demo.msi | MSIL/Agent.EUM | MSI inside the zip archive that drops and executes a PowerShell script that in turn drops and executes Spearal. |
| 3D21E1C9DFBA38EC6997 |
flogon.aspx | ASP/Agent.BI | Flog webshell. |
| 4954E8ACE23B48EC55F1 |
winsmsrv.exe | MSIL/HackTool |
Pinar, a reverse tunnel. |
| 562E1678EC8FDC1D83A3 |
LogonUl.exe | Win64/OilRig_ |
RDAT backdoor. |
| 66BD8DB40F4169C7F0FC |
Protocol.pdf.exe | Python/Trojan |
Whisper Protocol, the dropper that writes and executes the Whisper backdoor. |
| 6973D3FF8852A3292380 |
VeeamUpdate.exe | MSIL/Agent.ERR | Whisper backdoor. |
| 73D0FAA475C6E489B2C5 |
winhttpproxy.exe | MSIL/HackTool |
Pinar, a reverse tunnel. |
| B8AFC21EF2AA854896B9 |
RunExeActionAllowed |
MSIL/Agent.ERR | Whisper backdoor. |
| BB4FFCDBFAD40125080C |
MFTD.exe | MSIL/Tiny.GL | Hawking Listener. |
| BE0AD25B7B4834798490 |
videosrv.exe | Generik.BKYYERR | VideoSRV, a reverse shell. |
| E8E6E6AFEF3F574C1F52 |
wincapsrv.exe | MSIL/HackTool |
Laret, a reverse tunnel. |
| F28D8C5C2283019E6ED7 |
N/A | MSIL/Agent.EUM | Zip archive that contains an MSI that drops and executes a PowerShell script that in turn drops and executes Spearal. |
Network
| IP | Domain | Hosting provider | First seen | Details |
| 178.209.51[.]61 | N/A | Nine Internet Solutions AG | 2023‑12‑18 | Distribution server for BladedFeline’s Laret reverse tunnel. |
| 185.76.78[.]177 | N/A | EDIS GmbH – Noc Engineer | N/A | C&C used by Spearal. |
MITRE ATT&CK techniques
This table was created using version 17 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Reconnaissance | T1595.002 | Active Scanning: Vulnerability Scanning | BladedFeline probably conducts vulnerability scanning against targets to identify potentially vulnerable, exposed applications. |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains | BladedFeline registers domains to use for C&C servers. |
| T1583.003 | Acquire Infrastructure: Virtual Private Server | BladedFeline uses VPS services to host C&C servers. | |
| T1583 | Acquire Infrastructure | BladedFeline uses IPs for network infrastructure, including distributing malware and C&C servers. | |
| T1586.002 | Compromise Accounts: Email Accounts | BladedFeline uses compromised email accounts as C&C servers. | |
| Initial Access | T1190 | Exploit Public-Facing Application | BladedFeline probably exploits vulnerable public-facing applications for initial access. |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell | BladedFeline uses the Windows Command Shell to execute commands on compromised endpoints. |
| T1059.007 | Command and Scripting Interpreter: JavaScript | BladedFeline uses JavaScript webshells to execute commands on compromised endpoints. | |
| T1059.001 | Command and Scripting Interpreter: PowerShell | BladedFeline uses PowerShell to execute commands on compromised endpoints. | |
| T1059.006 | Command and Scripting Interpreter: Python | BladedFeline uses Python as a dropper for deploying backdoors to compromised endpoints. | |
| T1559 | Inter-Process Communication | BladedFeline uses IPC as a means of local code execution in its malicious IIS module. | |
| T1569.002 | System Services: Service Execution | BladedFeline uses Windows services for malware execution with Whisper and PrimeCache. | |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | The Whisper backdoor creates a LNK file in the startup folder for persistence. |
| T1546 | Event Triggered Execution | PrimeCache is loaded by an IIS Worker Process (w3wp.exe) when the IIS server receives an inbound HTTP request. | |
| Defense Evasion | T1078 | Valid Accounts | BladedFeline uses legitimate accounts to exfiltrate data and bypass defenses, and as C&C servers. |
| T1140 | Deobfuscate/Decode Files or Information | The Whisper backdoor uses base64 encoding to obfuscate data. | |
| T1070.004 | Indicator Removal: File Deletion | The Python dropper for Whisper deletes itself and other install files after a successful installation. | |
| T1070.006 | Indicator Removal: Timestomp | BladedFeline routinely timestomps the compilation timestamps of malware that the group develops. | |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory | BladedFeline dumps LSASS from memory to steal credentials. |
|
|


