On October 28th, 2024, the Dutch National police, alongside the FBI, Eurojust, and several other law enforcement organizations, performed a takedown of the infamous RedLine Stealer malware-as-a-service (MaaS) operation, and its clone called META Stealer. This global effort, named Operation Magnus, resulted in the takedown of three servers in the Netherlands, the seizure of two domains, two people being taken into custody in Belgium, and the unsealing of charges against one of the alleged perpetrators in the United States.
Back in April 2023, ESET participated in a partial disruption operation of the RedLine malware, which consisted of the removal of several GitHub repositories used as dead-drop resolvers for the malware’s control panel. Around that time, we investigated previously undocumented backend modules of this malware family in collaboration with fellow researchers at Flare. These modules don’t interact directly with the malware, but rather handle authentication and provide functionality for the control panel.
Since RedLine has now been taken down, we are revealing our findings from 2023 publicly, along with some more recent discoveries that were made based on source code and samples shared with us by the Dutch National Police.
Note that even with the takedown, RedLine may continue working to some degree for a time: panels that were already running would still be able to receive data, even if unable to build new samples or reconnect after logging out. Moreover, there are also old, cracked copies of the malware that might still work. Because of these factors, we are describing the RedLine operation as if it is an ongoing activity.
Key points of the blogpost:
- In 2023, ESET researchers, in collaboration with law enforcement, collected multiple modules used to run the infrastructure behind RedLine Stealer.
- We analyzed these previously undocumented modules to provide insight into the internal workings of this malware-as-a-service empire.
- We were able to identify over 1,000 unique IP addresses used to host RedLine control panels.
- The 2023 versions of RedLine Stealer we investigated in detail used the Windows Communication Framework for communication between the components, while the latest version from 2024 uses a REST API.
- Based on our analysis of the source code and backend samples, we have determined that Redline Stealer and META Stealer share the same creator.
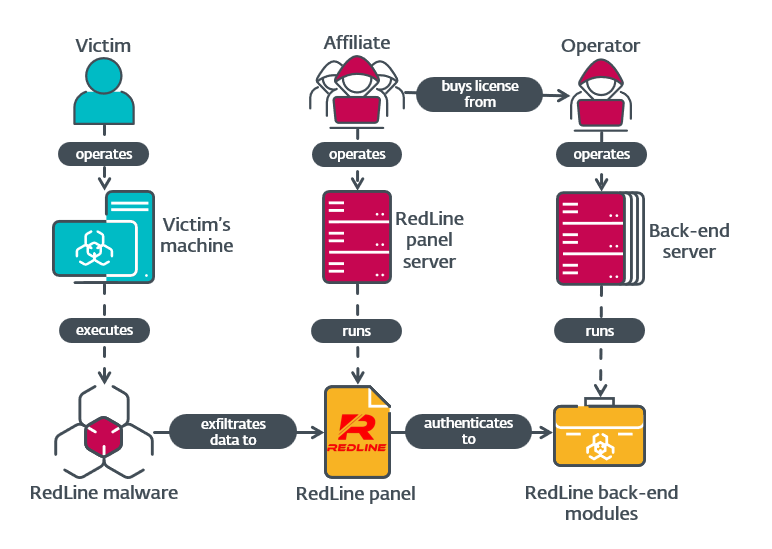
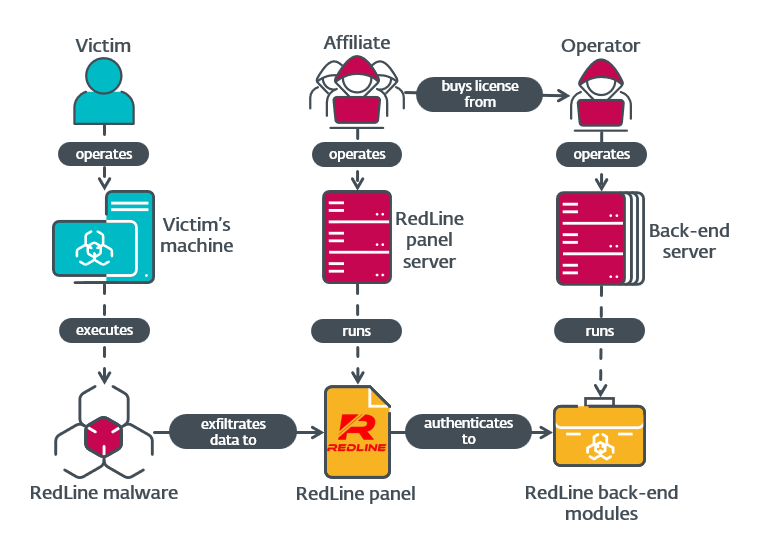
RedLine Stealer is information stealing malware first discovered in 2020 by Proofpoint. Rather than being centrally operated, RedLine operates on a MaaS model in which anyone can buy a turnkey infostealer solution from various online forums and Telegram channels. Clients, called affiliates, can opt for a monthly subscription, or a lifetime license; in exchange for their money, they get a control panel that generates malware samples and acts as a C&C server for them. The generated samples can collect a large variety of information, including local cryptocurrency wallets; cookies, saved credentials, and saved credit card details from browsers; and saved data from Steam, Discord, Telegram, and various desktop VPN applications.
Using a ready-made solution makes it easier for the affiliates to integrate RedLine Stealer into larger campaigns. Some notable examples include posing as free downloads of ChatGPT in 2023, and masquerading as video game cheats in the first half of 2024.
Note on terminology used
Because of its MaaS model, any comprehensive discussion of RedLine will involve multiple different components and layers of network infrastructure. To limit any possible confusion, we will use the following terms consistently throughout the text:
- RedLine malware: The RedLine Stealer malware or a sample thereof.
- RedLine panel: GUI control panel used to manage infostealing campaigns.
- RedLine backend: Collection of modules that provide authentication and functionality for the RedLine panel.
- RedLine: The whole malware operation. This includes the RedLine malware, the RedLine panel, and the RedLine backend modules.
- Backend server: A server on which the RedLine backend runs.
- Victim: Entity targeted with the RedLine malware.
- Operator: The individual or team that develops RedLine, sells licenses, and operates the licensing and associated backend infrastructure.
- Affiliate: Entity that operates infostealing campaigns via an instance of the RedLine panel. They usually have a license bought from the operator, but may also use a cracked version of the panel.
Overview
In this blogpost we document modules running on RedLine’s backend servers to provide a greater understanding of the inner workings of this MaaS empire. We also provide some information on the RedLine panel. Figure 1 contains a simplified overview of the whole RedLine operation.
Ordinarily, known samples of RedLine panel distributed to affiliates are heavily packed and virtualized after the first layer of obfuscation is applied. But as we were looking through our telemetry for activity related to RedLine Stealer and its panel, we came across an old version of the RedLine panel that was only obfuscated with .NET Reactor, making it much easier to analyze.
RedLine’s toolset
All the components of RedLine, from the malware itself to the backend authentication server, are written in C# with the .NET framework. The versions we analyzed used the Windows Communication Foundation (WCF) framework to communicate with each other. This framework allows one to define an API using contracts, which are statements applied to classes and interfaces to specify how objects and actions are translated between their representation in the code and the network communications. Thus, programs that interact using this framework must share definitions of these data structures or classes. These shared models proved useful in our analysis of the obfuscated components.
Note that the latest 2024 RedLine version uses a REST API instead of WCF to communicate with the backend.
RedLine panel
This control panel is what affiliates can buy on forums and Telegram channels. Licenses sell for US$150 per month or US$900 for a lifetime license.
Affiliates receive a graphical user interface (GUI) to manage their campaigns in exchange for payment. This GUI includes features to customize data collection, create malware samples, view and manage collected information, and integrate with a Telegram bot for selling stolen data.
In our investigation, we found that the 2023 versions of the panel were heavily obfuscated using DNGuard and BoxedApp. Despite these protections, we were able to understand the panel’s functionality by analyzing shared elements with other components in the malware and backend. All RedLine panels from 2023 were signed with certificates issued to AMCERT, LLC by Sectigo, which were later revoked after our report.
Authentication for RedLine panels requires affiliates to authenticate first. We discovered that GitHub repositories were used as dead-drop resolvers for authentication servers. By removing these repositories with GitHub’s cooperation, we disrupted RedLine operations temporarily in April 2023. Subsequently, the operators shifted to using Pastebin and then their own domains for dead-drop resolvers.
Upon logging in, affiliates are greeted with ads on the RedLine panel. The “Black Lists” tab allows affiliates to ignore data from specific countries, IP addresses, Build IDs, or HWIDs. The “Telegram” tab enables configuration of a Telegram bot to share stolen data with specific recipients.
The “Builder” tab allows affiliates to create new RedLine Stealer samples by providing necessary details, such as a server address, Build ID, error message, and an icon image. The Build ID serves as a campaign identifier and is sent along with stolen information.
The RedLine backend we analyzed in 2023 consists of two modules, with the first one managing affiliate and advertisement data. Despite its name, this module does not utilize a traditional database. Instead, it stores records as Protobuf-encoded objects in individual files, with a specific subdirectory for each type of data. The second module, known as RedLine.Nodes.LoadBalancer, acts as the server and provides most of the functionality used by the RedLine panel.
We also came across a module called RedLine.MainServer, which is likely the predecessor of RedLine.Nodes.DbController and RedLine.Nodes.LoadBalancer. In later versions, it was separated into a distinct module that manages user and advertisement data.
In the 2024 version of the backend, DbController and LoadBalancer have been replaced by a single module named Nodes.Api.
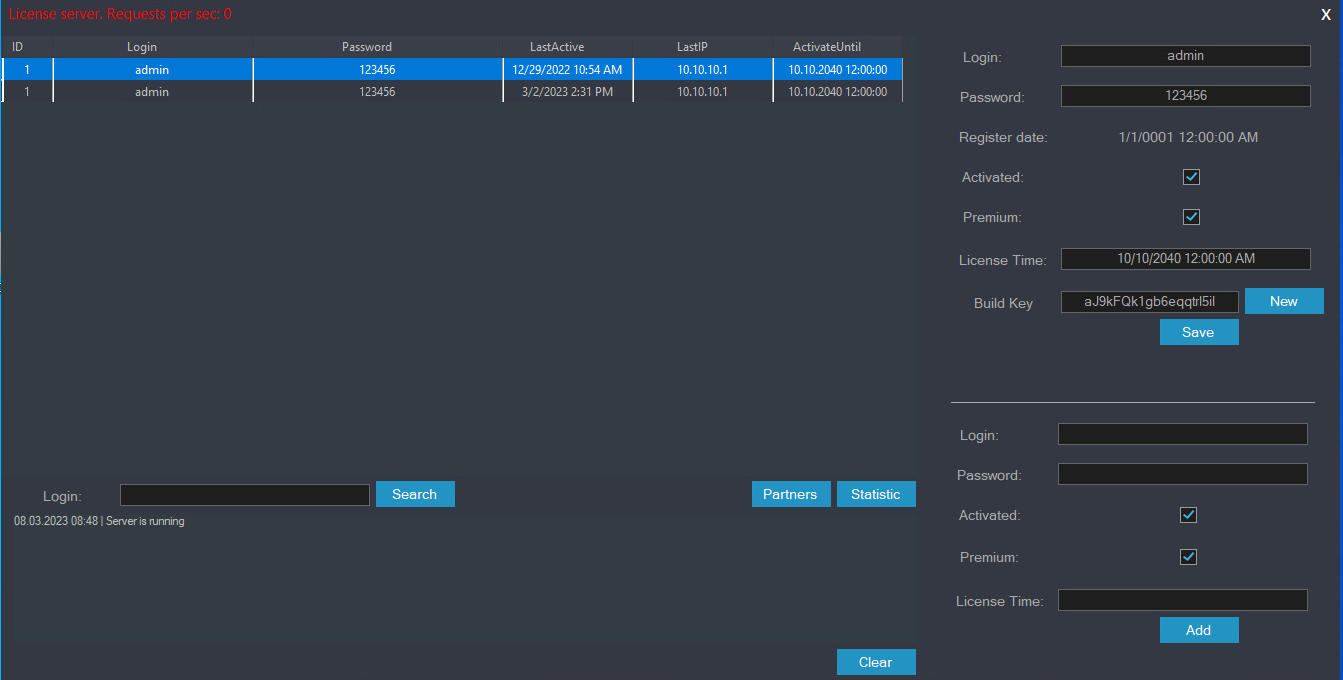
In DbController, affiliate data is represented by a class named ClientData, as detailed in Table 1. This class includes attributes such as ID, Login, Password, RegistrationDate, Activated, LastActive, LastIP, Premium, ActivateUntil, and BuildKey.
However, there are some interesting quirks in how passwords and lifetime licenses are handled within this module. For example, passwords are stored in cleartext, without any hashing function being involved in the authentication process.
Additionally, a lifetime license, which affiliates can purchase for US$900, is represented by setting the expiration date of a given license to any date after 2025, referred to as a Pro License in the code.
The LoadBalancer module listens on port 8778 and delegates requests related to affiliate and advertisement data to the corresponding handler in DbController. It also includes handlers for checking connectivity to the C&C server and creating malware samples.
To create samples of the RedLine Stealer malware, the OnCreateLastBuild handler in LoadBalancer uses the CreateBuild method from the VSBuilder class. This method logs the cleartext password for the affiliate’s account to the console, indicating a lack of adherence to standard security practices.
Furthermore, a token is derived from the campaign’s Build ID and the affiliate account’s Build Key to filter out connections from samples not created by the current account. This token value is likely used in communication between the samples and panel.
Some of the source files are read into memory to replace specific values before being written back to disk. The decompiler output for this method, along with that of a RedLine Stealer sample, provide enough context to understand that the modified values are:
- C&C address (encrypted),
- Build ID (encrypted),
- fake error message (encrypted),
- decryption key,
- flag to indicate whether to send stolen information in parts or all at once,
- authentication token, and
- assembly name.
After replacing these values, Visual Studio is invoked to build the project.
If the affiliate has selected the corresponding option and has a lifetime license, the compiled executable is obfuscated with the commercially available Babel Obfuscator. In the 2024 version, obfuscation is implemented for all users and is done via .NET Reactor instead.
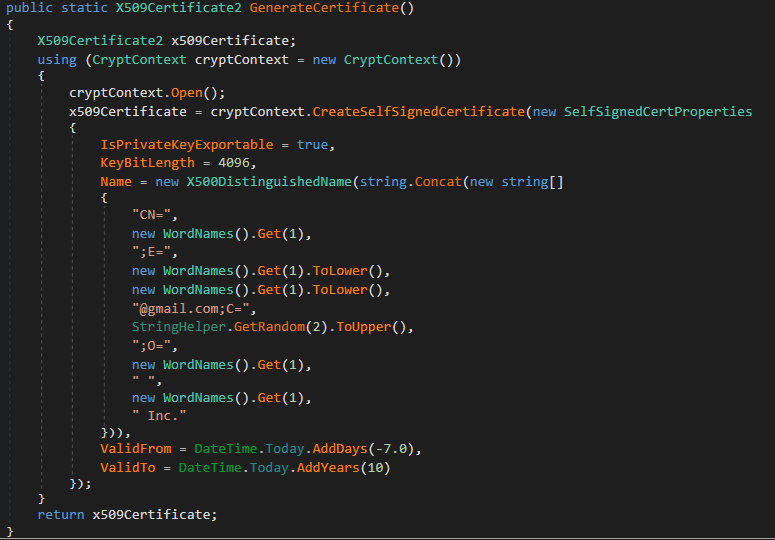
Subsequently, a self-signed certificate is generated using the code from Figure 13, and utilized to sign the executable. The Distinguished Name (DN) fields of the certificate are filled with random dictionary words. These certificates have a validity period extending from seven days before their generation to 10 years after. They are secured with the hardcoded password 123321.
The LoadBalancer module also included an OnCreateClipper handler, used to generate clipboard hijacking malware. This feature has been removed in the latest versions of the Redline backend.
In addition, the Builder class contained dead code for generating malware samples from a stub executable, a remnant from previous versions of RedLine Stealer. This code is no longer present in the latest version of the Redline backend.
Another handler, named OnSignFile, enables affiliates with lifetime licenses to sign arbitrary files using a certificate located on the backend server. The certificate used for signing RedLine panels and malware samples may be the one with the thumbprint 28F9A8E7601F5338BF6E194151A718608C0124A8, issued to Hangil IT Co., Ltd. This certificate, likely stolen, has been used to sign numerous malicious files and has been revoked.
RedLine.MainServer
The RedLine.MainServer module integrates functionalities from the LoadBalancer and DbController modules, providing a GUI for admin management of affiliate accounts and advertisement data. This version of MainServer appears to be an ancestor of LoadBalancer and DbController rather than a successor, as indicated by various factors.
- MainServer samples are compiled with an older version of the .NET framework (4.6.2 vs 4.8).
- The assembly’s copyright year is 2020 instead of 2021.
- Some MainServer samples lack functionality for advertisements.
- The main WCF service’s contract (MainPanelService) does not include the IsAlive handler present in LoadBalancer.
In later versions of the RedLine backend, the GUI administration panel has been separated into its own module, also named MainServer.
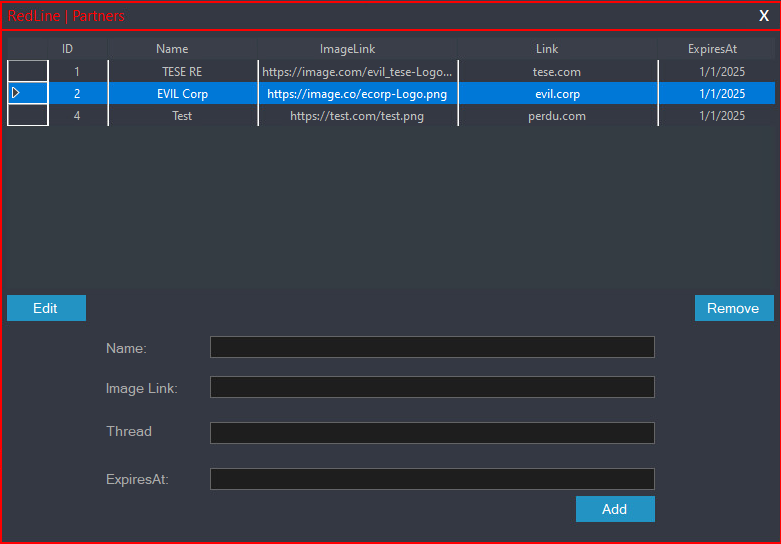
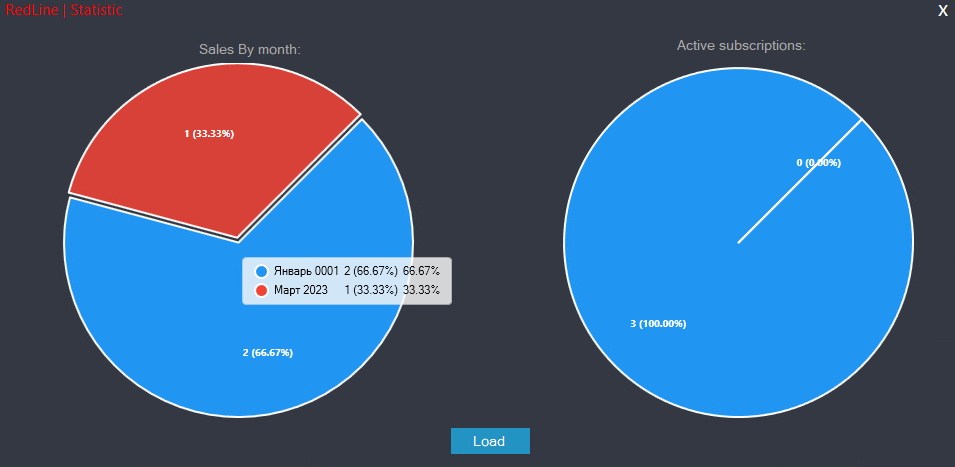
The GUI version examined provides insight into RedLine management, offering forms for creating and editing affiliate account data (Figure 14) and managing advertisements (Figure 15). The dashboard (Figure 16) gives an overview of license sales.
Nodes.Api
Recent RedLine versions combine the functionalities of the LoadBalancer and DbController modules into a new module named Nodes.Api. Packaged as a single-file .NET application, Nodes.Api utilizes the WebApplication class from ASP.NET to provide the REST API for RedLine and META servers. The shared functionality indicates that the two infostealers are operated by the same group.
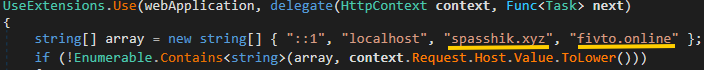
Table 2 outlines the endpoints exposed by the REST API along with their corresponding WCF handlers from previous versions.
Table 2. RedLine endpoints
| Endpoint | Corresponding WCF Handler | Description |
| /api/test | N/A | Probably used to test connectivity. |
The value “OK” is simply returned. Figure 23 displays the distribution of hosted panels geographically. Approximately 20% each of the total panels are located in Russia, Germany, and the Netherlands, with Finland and the United States each representing around 10%. While this data is based on samples targeting our customers, we believe it provides a fairly accurate overview of the malware distribution.
Figure 24 illustrates the geographical distribution of multiple distinct backend servers we identified. About a third of these servers are located in Russia, with the UK, the Netherlands, and the Czech Republic each accounting for approximately 15% of the total servers.
Our analysis revealed that the RedLine panel utilized GitHub repositories as dead-drop resolvers for its authentication servers in the 2023 versions. The files in these repositories were encrypted using a custom RSA module. Subsequent versions, up to at least mid-2024, employed RSA encryption instead. We were able to extract an RSA private key from a panel sample, enabling us to obtain lists of authentication servers for sharing with law enforcement agencies.
Hey there! So, we had a bunch of panel and server addresses that we used to collect information. These were pretty handy for law enforcement agencies in their operations, but now they’re no longer active.
| IP | Domain | Hosting provider | First seen | Details |
| N/A | spasshik[.]xyz | N/A | 2024-06-02 | META backend REST server. |
| N/A | fivto[.]online | N/A | 2024-08-03 | RedLine backend REST server. |
MITRE ATT&CK techniques
This table was created using version 15 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1583.003 | Acquire Infrastructure: Virtual Private Server | Instances of the RedLine back end are hosted on leased virtual private servers. |
| T1583.004 | Acquire Infrastructure: Server | Instances of the RedLine back end are hosted on servers that appear to be exclusive to RedLine. | |
| T1587.001 | Acquire Infrastructure: Web Services | Operators of RedLine have created multiple GitHub accounts and repositories. | |
| T1587.002 | Develop Capabilities: Malware | Operators of RedLine have developed their own malware families, control panels, and back-end servers. | |
| T1588.003 | Develop Capabilities: Code Signing Certificates | The RedLine back end automatically generates self-signed certificates when creating samples. | |
| T1608.002 | Obtain Capabilities: Code Signing Certificates | RedLine panels are signed with valid certificates issued to AMCERT,LLC. | |
| T1608.001 | Stage Capabilities: Upload Malware | Back-end components of RedLine are uploaded to private servers. | |
| Defense Evasion | T1622 | Debugger Evasion | The RedLine panel automatically terminates itself if it detects a debugger or analysis tools. |
| T1027.002 | Obfuscated Files or Information: Software Packing | Samples of the RedLine panel are packed using DNGuard and BoxedApp. | |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding | RedLine makes extensive use of base64 encoding in its network communications. Network communication uses the standard binary encoder of the WCF framework. |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Communications between the panel and back-end server use AES encryption. In some cases, dead-drop resolver content is encrypted with AES-CBC. |
|
| T1573.002 | Encrypted Channel: Asymmetric Cryptography | Communications between the panel and back-end server use RSA encryption. In some cases, dead-drop resolver content is encrypted with RSA. |
|
| T1071.001 | Application Layer Protocol: Web Protocols | Network communication in recent versions is done via a REST API over HTTPS. | |
| T1095 | Non-Application Layer Protocol | Network communication is done with the WCF Framework over TCP. | |
| T1102.001 | Web Service: Dead Drop Resolver | The RedLine panel uses GitHub repositories as dead-drop resolvers to obtain the address of back-end servers. | |
| T1571 | Non-Standard Port | By default, the RedLine panel’s Guest Links functionality runs an HTTP server on port 7766. |