Recent years have seen significant evolution in the UEFI threat landscape, especially in the realm of UEFI bootkits. The journey began with the proof of concept (PoC) of the first UEFI bootkit by Andrea Allievi in 2012, showcasing the deployment of bootkits on modern UEFI-based Windows systems. Subsequent PoCs like EfiGuard, Boot Backdoor, and UEFI-bootkit followed, leading to the discovery of real UEFI bootkits in the wild such as ESPecter and FinSpy bootkit in 2021, and the infamous BlackLotus in 2023 capable of bypassing UEFI Secure Boot on up-to-date systems.
These bootkits primarily targeted Windows systems. However, a new discovery has been unveiled – the first UEFI bootkit designed for Linux systems, named Bootkitty. While this bootkit is considered an initial proof of concept and has not been observed in the wild, it signifies a shift where UEFI bootkits are no longer limited to Windows systems.
The main objective of Bootkitty is to disable the kernel’s signature verification feature and preload two unknown ELF binaries via the Linux init process during system startup. Additionally, a related unsigned kernel module named BCDropper was discovered during analysis, suggesting a potential connection to the same author(s) as Bootkitty.
Key points highlighted in this blogpost:
- In November 2024, a previously unknown UEFI application, bootkit.efi, was uploaded to VirusTotal.
- The application was confirmed as Bootkitty, the first UEFI bootkit targeting Linux, specifically certain Ubuntu versions.
- Bootkitty is signed with a self-signed certificate, limiting its execution on systems with UEFI Secure Boot enabled unless the attacker’s certificates are installed.
- Bootkitty is designed to seamlessly boot the Linux kernel with or without UEFI Secure Boot by patching the necessary functions responsible for integrity verification before GRUB execution.
- bootkit.efi is more of a proof of concept, showing signs of being an initial version rather than the work of an active threat actor.
- A related kernel module named BCDropper was discovered, deploying an ELF program responsible for loading another unknown kernel module.
Overview of Bootkitty
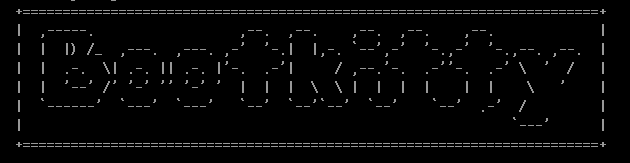
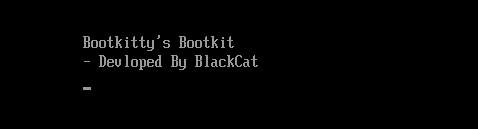
Bootkitty contains several artifacts indicating its nature as a proof of concept. It includes two unused functions capable of displaying special strings during execution. The first function prints ASCII art representing the bootkit’s name, while the second displays a list of possible authors or contributors involved in its development.
Another interesting feature is the printing of specific strings during each boot, indicating the presence of the bootkit.
Bootkitty’s functionality is currently limited to specific systems due to hardcoded byte patterns used for identifying functions to modify in memory. This limitation, along with the method of patching the decompressed Linux kernel, suggests that Bootkitty is more of a proof of concept rather than a fully operational threat.
Technical Analysis
The technical analysis of Bootkitty’s execution reveals its approach to patching the GRUB bootloader and the Linux kernel’s EFI stub loader. Additionally, the bootkit patches the decompressed Linux kernel image in memory to alter specific functionalities.
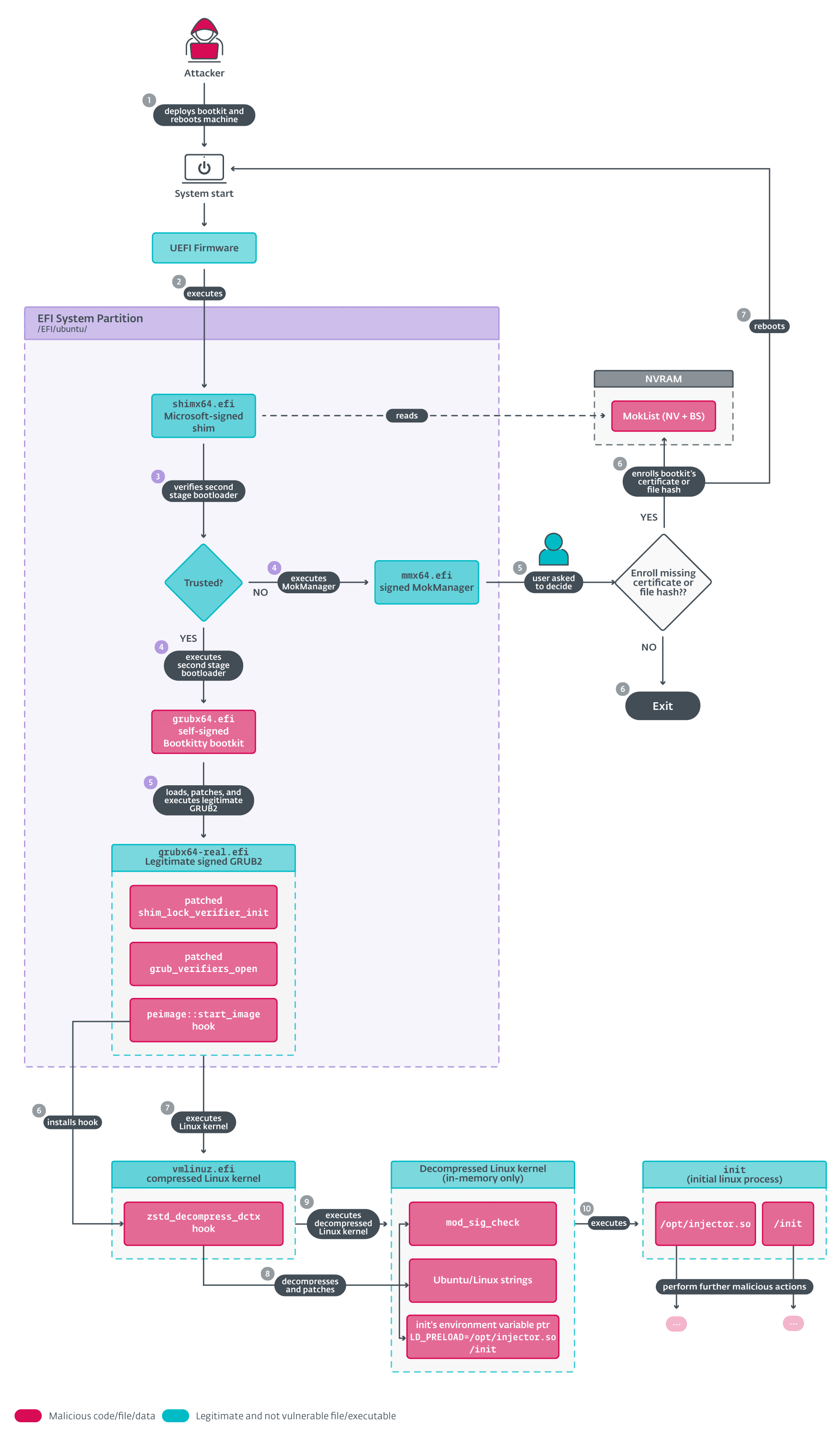
Initialization and GRUB Hooking
Bootkitty checks for the status of UEFI Secure Boot and proceeds to hook authentication protocols within GRUB to enable the loading and execution of the bootkit. It modifies functions responsible for file authentication and verification to bypass security checks.
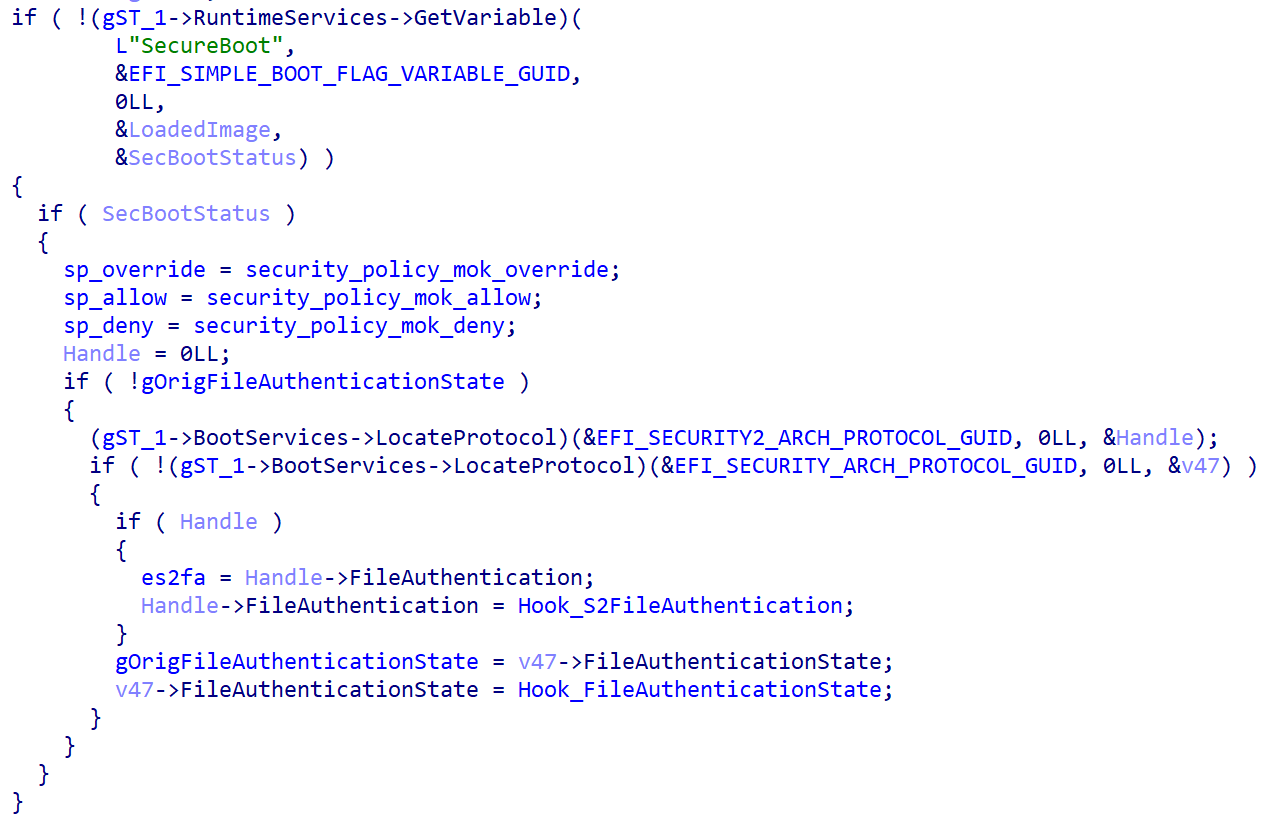
After loading the legitimate GRUB, Bootkitty proceeds to patch specific functions within GRUB’s memory to alter the behavior of loading and verifying files during boot.
Linux Kernel Image Decompression Hook
This hook in Bootkitty is responsible for patching the decompressed Linux kernel image, altering specific functionalities within the kernel. It modifies the kernel version, patches functions related to signature checks, and alters the execution flow of the init process.
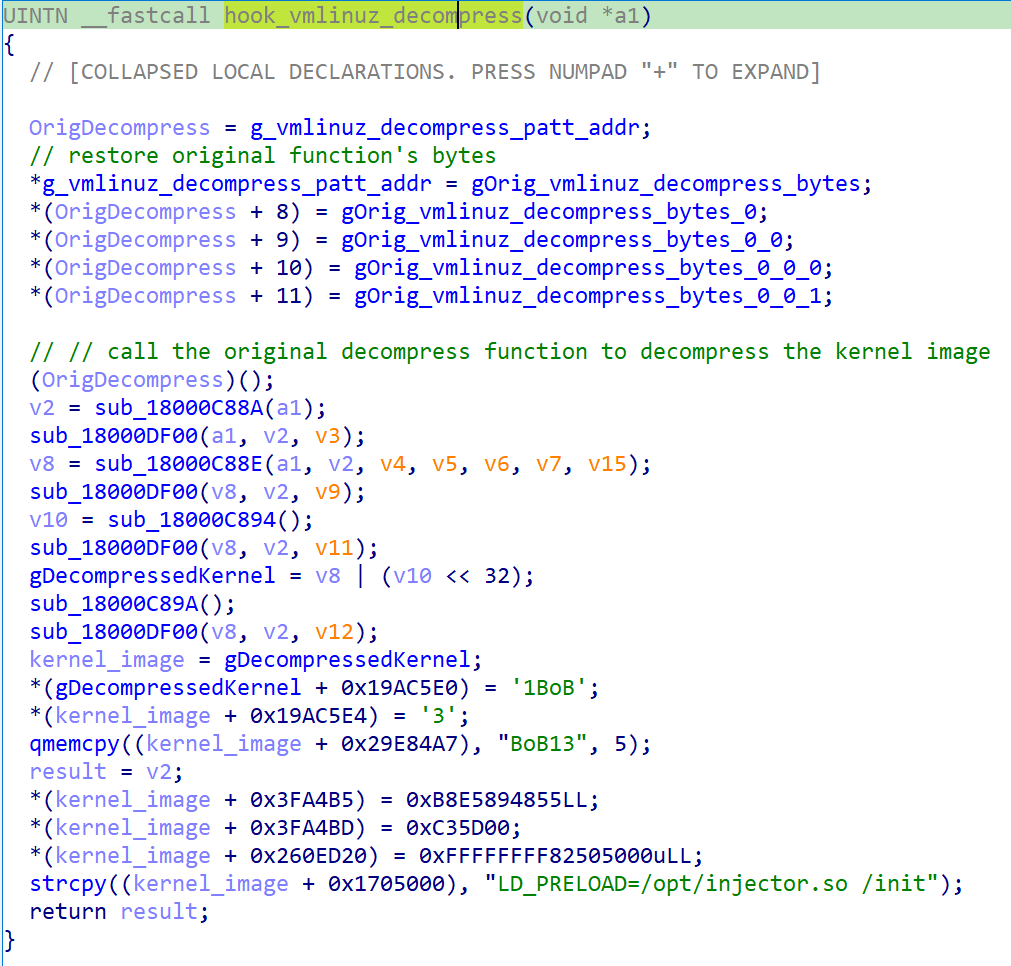
Bootkitty’s impact on the system includes modifications to kernel strings, the execution of unknown ELF shared objects, and alterations to the system’s integrity verification processes. Remediation steps involve restoring the original GRUB file and ensuring UEFI Secure Boot is enabled for system protection.
BCDropper and BCObserver
Additionally, a related kernel module named BCDropper was discovered, hinting at a potential connection to Bootkitty. BCDropper drops an embedded ELF file named BCObserver, which executes specific commands via /bin/bash after waiting for the display manager to start.
While the connection between BCDropper and Bootkitty is not confirmed, the presence of these modules suggests a coordinated effort to load malicious components into the system.
Conclusion
Bootkitty represents a significant development in the UEFI threat landscape by introducing the first UEFI bootkit designed for Linux systems. While currently a proof of concept, Bootkitty highlights the need for enhanced security measures to protect against potential future threats.
To safeguard Linux systems from such threats, it is essential to enable UEFI Secure Boot, keep system firmware and software up-to-date, and maintain an updated UEFI revocations list.
For inquiries about the research published on WeLiveSecurity, contact threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For inquiries about this service, visit the ESET Threat Intelligence page.
Indicators of Compromise (IoCs)
A detailed list of indicators of compromise (IoCs) and samples can be found in our GitHub repository.
MITRE ATT&CK Techniques
This table incorporates the MITRE ATT&CK framework version 16 to outline the tactics and techniques employed by Bootkitty and related components in the attack chain.