ESET researchers discovered a code execution vulnerability in WPS Office for Windows (CVE-2024-7262), as it was being exploited by APT-C-60, a South Korea-aligned cyberespionage group. Upon analyzing the root cause, we subsequently discovered another way to exploit the faulty code (CVE-2924-7263). Following a coordinated disclosure process, both vulnerabilities are now patched – in this blogpost, we provide technical details.
Key points of the blogpost:
- APT-C-60 weaponized a code execution vulnerability in WPS Office for Windows (CVE-2024-7262) in order to target East Asian countries.
- A root cause analysis of this vulnerability is provided along with a description of its weaponization.
- The study of the exploit led ESET researchers to the discovery of an alternative path to exploit the vulnerability (CVE-2024-7263).
Overview
While investigating APT-C-60 activities, we found a strange spreadsheet document referencing one of the group’s many downloader components. Our analysis led us to the discovery of a code execution vulnerability in WPS Office for Windows being exploited in the wild by APT-C-60 to target East Asian countries. The final payload is a custom backdoor we internally named SpyGlace, publicly documented by ThreatBook as TaskControler.dll.
According to the WPS website, this software has over 500 million active users worldwide, which makes it a good target to reach a substantial number of individuals in the East Asia region. During our coordinated vulnerability disclosure process, DBAPPSecurity independently published an analysis of the weaponized vulnerability and confirmed that APT-C-60 has exploited the vulnerability to deliver malware to users in China.
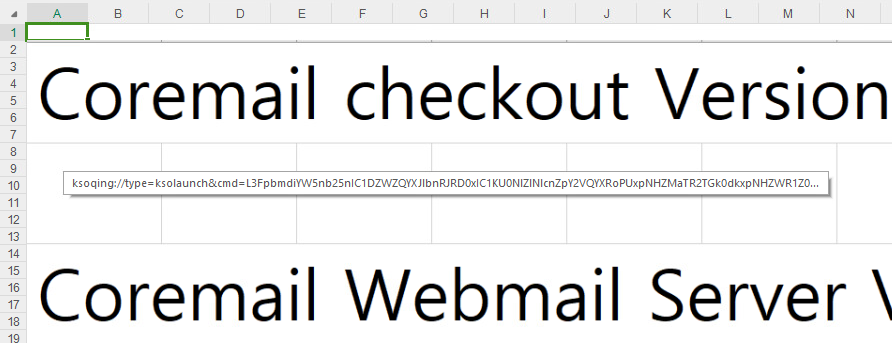
The malicious document (SHA-1: 7509B4C506C01627C1A4C396161D07277F044AC6) comes as an MHTML export of the commonly used XLS spreadsheet format. However, it contains a specially crafted and hidden hyperlink designed to trigger the execution of an arbitrary library if clicked when using the WPS Spreadsheet application. The rather unconventional MHTML file format allows a file to be downloaded as soon as the document is opened; therefore, leveraging this technique while exploiting the vulnerability provides for remote code execution. Figure 1 shows how the document is displayed in WPS Spreadsheet: an image of rows and columns referencing the Coremail email solution, used as a decoy. The image hides the malicious hyperlink.
Following our coordinated vulnerability disclosure policy, from the moment the weaponized document was uploaded to VirusTotal to the release of this blogpost, the following timeline was observed:
- 2024-02-29: The exploit document for CVE-2024-7262 was uploaded to VirusTotal.
- 2024-03-??: Kingsoft released an update that silently patched the CVE-2024-7672 vulnerability so that the 2024-02-29 exploit no longer worked. This was determined retrospectively, by analyzing all accessible WPS Office releases between 2024-03 and 2024-04, as Kingsoft was not especially forthcoming in providing precise details of its actions when attempting to repair this vulnerability.
- 2024-04-30: We analyzed the malicious document from VirusTotal and discovered it was actively exploiting CVE-2024-7262, which was a zero-day vulnerability at the time of the document’s initial use. We also discovered that Kingsoft’s silent patch addressed only one part of the faulty code, and the remaining flawed code was still exploitable.
- 2024-05-25: We contacted Kingsoft to report our findings. While the first vulnerability was already patched, we asked if they could create a CVE entry and/or a public statement as they had for CVE-2022-24934.
- 2024-05-30: Kingsoft acknowledged the vulnerabilities and told us they would keep us updated.
- 2024-06-17: We asked for an update.
- 2024-06-22: Kingsoft told us the development team was still working on it and was aiming to fix this in the coming version.
- 2024-07-31: Based on later tests, we found that CVE-2024-7263 was silently patched. We advised Kingsoft that we had reserved and were preparing CVE-2024-7262 and CVE-2024-7263.
- 2024-08-11: DBAPPSecurity team independently published its findings.
- 2024-08-15: CVE-2024-7262 and CVE-2024-7263 were published.
- 2024-08-16: We asked Kingsoft for another update.
- 2024-08-22: Kingsoft acknowledged it had fixed CVE-2024-7263 by the end of May, which contradicts the company’s claim on 2024-06-22 that its development team “are still working on it”.
- 2024-08-28: Kingsoft has acknowledged both vulnerabilities and that it has patched both. However, it has expressed no interest in publicizing the in-the-wild exploitation of CVE-2024-7262 so we are now publishing this blogpost to warn Kingsoft’s customers that they should urgently update WPS Office due to in-the-wild exploitation and third-party disclosure of the CVE-2024-7262 vulnerability and exploit, which increase the chances of further exploitation.
The CVE-2024-7262 vulnerability stemmed from the lack of sanitization of an attacker-provided file path and lack of validation of the plugin being loaded. After analyzing its patch, we discovered another way to exploit the vulnerability by leveraging a further logic bug.
CVE-2024-7262
This section describes the bug exploited by APT-C-60 that allows code execution via hijacking the control flow of the WPS Office plugin component promecefpluginhost.exe. We also explain how the vulnerability was triggered and weaponized in the shape of a legitimate-looking spreadsheet document.
Root cause analysis
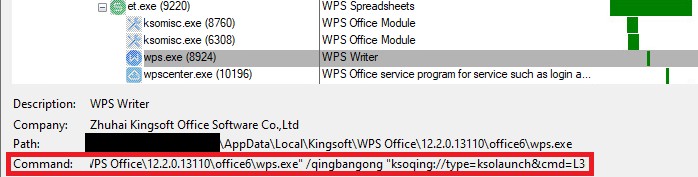
When installing WPS Office for Windows, the software suite registers a custom protocol handler called ksoqing that allows the execution of an external application whenever a user clicks on a URL starting with the URI scheme ksoqing://. In the Windows operating system, the registration of a custom protocol handler is done in the registry. In this case, the default value under the key HKCR\ksoqing\shell\open\command directs Windows to execute C:\Users\<USER>\AppData\Local\Kingsoft\WPS Office\<VERSION>\office6\wps.exe with the argument /qingbangong “%1” where %1 is replaced with the full URL. To illustrate this, Figure 2 shows what happens when a user clicks on a hyperlink using the custom protocol ksoqing inside the WPS Spreadsheet application (et.exe).
Exploiting this vulnerability hinges on the inclusion of the string libcef.dll in the file path. While we have not yet discovered a method to download a file and specify its filename, we have successfully leveraged a local network setup by hosting a library on a share and directing the variable CefPluginPathU8 to it. This approach works because LoadLibraryExW permits network paths to be designated. Figure 18 showcases how the control flow of promecefpluginhost.exe (version 12.2.0.16909 released in late April 2024) was manipulated using a network path.
Affected versions of WPS Office for Windows span from 12.2.0.13110, introduced around August 2023, up to the patch release at the end of May 2024 with version 12.2.0.17119.
In conclusion, the targeted exploitation of WPS Office by APT-C-60 underscores their commitment to infiltrating entities in East Asian regions. Whether the group developed or procured the CVE-2024-7262 exploit, it necessitated a deep dive into the software’s internals and an understanding of Windows loading mechanisms. The exploit is deceptively crafted to entice users into interacting with a seemingly legitimate spreadsheet, while also being highly effective and dependable. The selection of the MHTML file format enabled the attackers to transform a code execution vulnerability into a remote one.
Furthermore, the discovery of CVE-2024-7263 emphasizes the importance of diligent patch validation procedures to ensure that the root issue has been completely remedied.
We strongly recommend that WPS Office for Windows users update their software to the latest version. For any inquiries regarding our research on WeLiveSecurity, please reach out to threatintel@eset.com.
ESET Research offers private APT intelligence reports and data feeds. For further details on this service, visit the ESET Threat Intelligence page.
Indicators of Compromise (IoCs) can be found in our GitHub repository.
Files:
SHA-1: 7509B4C506C01627C1A4C396161D07277F044AC6
Filename: input.htm
Detection: HTML/Agent.HQ
Description: MHTML-formatted WPS Spreadsheet exploit – CVE‑2024‑7262
SHA-1: 08906644B0EF1EE6478C45A6E0DD28533A9EFC29
Filename: WPS_TEST_DLL.dll
Detection: Win32/TrojanDownloader.Agent.HRP
Description: Downloader component
Network:
IP: 162.222.214[.]48, 131.153.206[.]231
Domain: rammenale[.]com
Hosting provider: PhoenixNAP
First seen: 2024-03-08
Details: C&C server hosting next stages
MITRE ATT&CK Techniques:
Various techniques were employed by APT-C-60, including resource development and execution tactics according to the MITRE ATT&CK framework version 15.
For a detailed breakdown of the techniques utilized, please refer to the MITRE ATT&CK framework.
To learn more about ESET Threat Intelligence services, visit the provided link. message to make it more polite:
“Can you please send me the report by the end of the day?”
“Could you kindly provide me with the report by the end of the day?” Please rewrite the sentence so that I can assist you better.