Welcome, fellow Linux enthusiasts! Have you heard about the latest threat making waves in the Linux world? It’s called Auto-Color, and it’s causing quite a stir by targeting universities and government institutions.
Auto-Color Linux Malware: What You Need to Know
Auto-Color is a stealthy backdoor malware that has been discovered by the diligent researchers at Palo Alto Networks Unit 42. This malicious software is actively running campaigns aimed at Linux systems globally, so it’s essential to stay vigilant.
Once Auto-Color infiltrates a system, it cleverly renames itself using harmless file names like “door” or “egg” to evade detection. It employs advanced techniques to conceal its communications and configurations, making it a formidable threat. The malware is reminiscent of the notorious Symbiote malware, known for its elusive C&C hiding tactics.
After gaining a foothold in a system, Auto-Color grants attackers full remote access. By installing a malicious library implant (libcext.so.2), the malware ensures persistence, even mimicking legitimate system libraries to stay undetected.
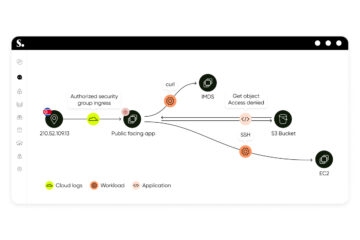
Following a successful attack, Auto-Color awaits commands from its C&C, enabling activities like opening reverse shells, executing commands, modifying files, and acting as a proxy for malicious traffic redirection. To cover its tracks, the malware features a “kill-switch” to erase all traces of infection.
For a deep dive into the technical aspects of Auto-Color, check out the detailed analysis by the Unit 42 team here.
Stay Alert, Linux Users!
The Unit 42 researchers first encountered Auto-Color in November 2024, noting its focus on educational and governmental institutions in Asia and North America. While the exact entry points remain elusive, the researchers have shared indicators of compromise (IoCs) to aid in system scans.
We’d love to hear your thoughts on this evolving cybersecurity landscape. Share your insights in the comments below!