ESET researchers discovered a series of attacks on a governmental organization in Europe using tools capable of targeting air-gapped systems. The campaign, which we attribute to GoldenJackal, a cyberespionage APT group that targets government and diplomatic entities, took place from May 2022 to March 2024. By analyzing the toolset deployed by the group, we were able to identify an attack GoldenJackal carried out earlier, in 2019, against a South Asian embassy in Belarus that, yet again, targeted the embassy’s air-gapped systems with custom tools.
This blogpost introduces previously undocumented tools that we attribute to GoldenJackal based on victimology, code, and functional similarities between the toolsets.
Key points of the blogpost:
- GoldenJackal used a custom toolset to target air-gapped systems at a South Asian embassy in Belarus since at least August 2019. In this blogpost, we describe these tools publicly for the first time.
- This blogpost also features the first public description of a highly modular toolset GoldenJackal deployed in Europe on various occasions between May 2022 and March 2024 against a European Union government organization.
- These toolsets provide GoldenJackal a wide set of capabilities for compromising and persisting in targeted networks. Victimized systems are abused to collect interesting information, process the information, exfiltrate files, and distribute files, configurations and commands to other systems.
- The ultimate goal of GoldenJackal seems to be stealing confidential information, especially from high-profile machines that might not be connected to the internet.
GoldenJackal profile
GoldenJackal is an APT group active since at least 2019. It targets government and diplomatic entities in Europe, the Middle East, and South Asia. The group is little known and has only been publicly described in 2023 by Kaspersky. The group’s known toolset includes several implants written in C#: JackalControl, JackalSteal, JackalWorm, JackalPerInfo, and JackalScreenWatcher – all of them used for espionage.
Overview
In May 2022, we discovered a toolset that we could not attribute to any APT group. But once the attackers used a tool similar to one of those publicly documented by Kaspersky, we were able to dig deeper and to find a connection between the publicly documented toolset of GoldenJackal and this new one.
Extrapolating from that, we managed to identify an earlier attack where the publicly documented toolset was deployed, as well as an older toolset that also has capabilities to target air-gapped systems. This blogpost shines a light on the technical aspects of the publicly undocumented toolsets, and shares some insights about GoldenJackal’s tactics, techniques, and procedures.
Victimology
GoldenJackal has been targeting governmental entities in Europe, the Middle East, and South Asia. We detected GoldenJackal tools at a South Asian embassy in Belarus in August and September 2019, and again in July 2021.
Kaspersky reported a limited number of attacks against government and diplomatic entities in the Middle East and South Asia, starting in 2020.
More recently, according to ESET telemetry, a European Union governmental organization was repeatedly targeted from May 2022 until March 2024.
Attribution
All the campaigns that we describe in this blogpost deployed, at some point, at least one of the tools attributed to the GoldenJackal APT group by Kaspersky. As was the case in the Kaspersky report, we can’t attribute GoldenJackal’s activities to any specific nation-state. There is, however, one clue that might point towards the origin of the attacks: in the GoldenHowl malware, the C&C protocol is referred to as transport_http, which is an expression typically used by Turla (see our ComRat v4 report) and MoustachedBouncer. This may indicate that the developers of GoldenHowl are Russian speakers.
Breaching air-gapped systems
In order to minimize the risk of compromise, highly sensitive networks are often air gapped, i.e., isolated from other networks. Usually, organizations will air gap their most valuable systems, such as voting systems and industrial control systems running power grids. These are often precisely the networks that are of most interest to attackers.
As we stated in a previous white paper titled Jumping the air gap: 15 years of nation-state effort, compromising an air-gapped network is much more resource-intensive than breaching an internet-connected system, which means that frameworks designed to attack air-gapped networks have so far been exclusively developed by APT groups. The purpose of such attacks is always espionage, perhaps with a side of sabotage.
With the level of sophistication required, it is quite unusual that in five years, GoldenJackal managed to build and deploy not one, but two separate toolsets designed to compromise air-gapped systems. This speaks to the resourcefulness of the group. The attacks against a South Asian embassy in Belarus made use of custom tools that we have only seen in that specific instance. The campaign used three main components: GoldenDealer to deliver executables to the air-gapped system via USB monitoring; GoldenHowl, a modular backdoor with various functionalities; and GoldenRobo, a file collector and exfiltrator.
In the latest series of attacks against a government organization in Europe, GoldenJackal moved on from the original toolset to a new, highly modular one. This modular approach applied not only to the design of the malicious tools (as was the case with GoldenHowl), but also to their roles: they were used, among other things, to collect and process interesting information, to distribute files, configurations, and commands to other systems, and to exfiltrate files.
Technical analysis
Initial access
So far, we haven’t been able to trace back to the initial compromise vector in the campaigns seen in our telemetry. Note that Kaspersky reported in a blogpost that GoldenJackal used trojanized software and malicious documents for this purpose.
The mysterious toolset from 2019
The earliest attack that we have attributed to GoldenJackal, which targeted a South Asian embassy in Belarus, occurred in August 2019. The toolset used in this attack is, to the best of our knowledge, publicly undocumented. We’ve only observed the following custom tools once, and never again:
- A malicious component that can deliver executables to air-gapped systems via USB drives. We’ve named this component GoldenDealer.
- A backdoor, which we’ve named GoldenHowl, with various modules for malicious capabilities.
- A malicious file collector and exfiltrator, which we’ve named GoldenRobo.
An overview of the attack is shown in Figure 1.
The original attack vector is unidentified, so we assume that GoldenDealer and an undisclosed worm component are already present on a compromised PC with internet access. When a USB drive is inserted, the unknown component duplicates itself and the GoldenDealer component onto the drive. Although we have not directly observed this unknown component, we have seen similar components with comparable functions, such as JackalWorm, in other toolsets used in subsequent attacks by the same group.
It is likely that this unknown component locates the most recently modified directory on the USB drive, conceals it, and renames itself with the name of that directory, a tactic also employed by JackalWorm. Furthermore, we suspect that the component utilizes a folder icon to lure the user into running it when the USB drive is inserted into an air-gapped system, which is another technique used by JackalWorm.
Upon reinserting the drive into the internet-connected PC, GoldenDealer retrieves information about the air-gapped PC from the USB drive and transmits it to the C&C server. The server then responds with one or more executable files to be executed on the air-gapped PC. Subsequently, when the drive is reintroduced into the air-gapped PC, GoldenDealer retrieves the executables from the drive and executes them without requiring user interaction, as GoldenDealer is already operational.
Although we have witnessed GoldenDealer executing GoldenHowl on an internet-connected PC, we have not directly observed GoldenDealer running GoldenRobo. However, we have observed GoldenRobo operating on the connected PC, extracting files from the USB drive and sending them to its C&C server. There appears to be another unidentified component responsible for copying files from the air-gapped PC to the USB drive, which we have not yet observed. The malware can be used if it is configured to wait a minimum number of seconds before determining that the PC has no connectivity, but in the samples we observed, there was no wait.
The field “ltwnk” is unknown and not used by the malware. The field “rpk” contains a list of hashes of executables downloaded from the C&C server.
The downloader thread checks the network connectivity status every 30 minutes and only performs actions if the PC is connected to the internet. It sends GET requests to specific URLs to notify the C&C server and receive executable files. These executables are run based on certain conditions and their information is sent back to the server. The thread also collects system information and sends it to the C&C server.
The USB monitoring thread on connected PCs monitors the insertion of removable drives and patches the master boot record of the inserted USB drive. It creates a hidden directory on the drive to pass executables to air-gapped systems and gathers information from air-gapped PCs. The information in this file is added to the local file 130d-1154-30ce-be1e and will be sent to the C&C server by the downloader thread.
USB monitoring thread on air-gapped PCs
This thread complements the previous one by copying the contents of the file 37b3-ebe5-568e-0676 containing executables from the USB drive to the local file fb43-138c-2eb0-c651. It also takes the local file 130d-1154-30ce-be1e with information about the air-gapped system and appends its contents to the bc41-ac6f-e55e-61a8 file on the USB drive. This thread contains the code for obtaining system information and executing the malicious scripts.
GoldenHowl
Another tool from GoldenJackal’s 2019 toolset is GoldenHowl, a Python backdoor with various modules for malicious activities. It comes as a self-extracting archive with legitimate Python binaries, libraries, and malicious scripts. Figure 3 displays the contents of one of these archives, where the Python executable version 2.7.15 is renamed as WinAeroModule.exe. This component is designed for use on PCs with internet connectivity.
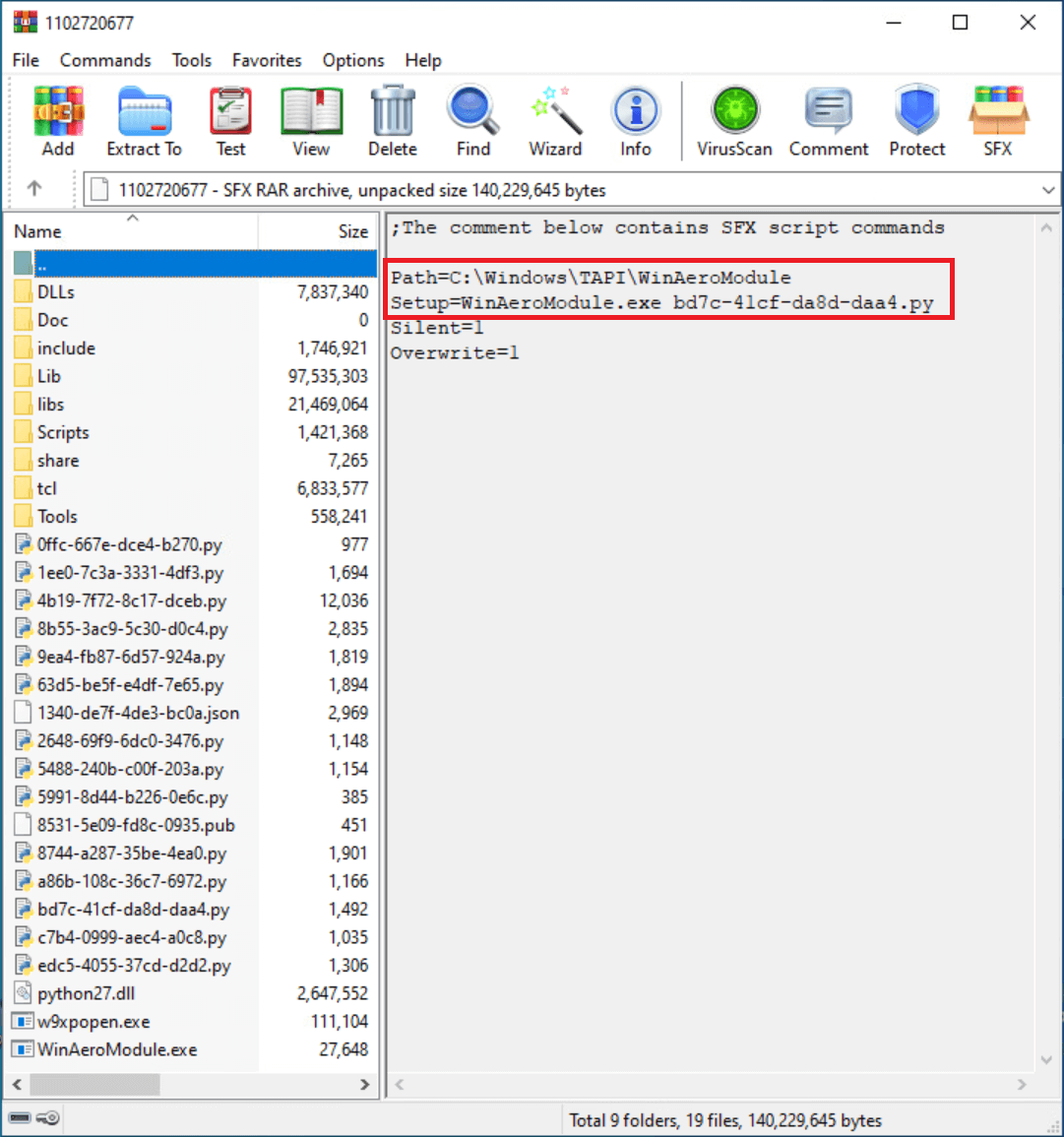
The initial script in GoldenHowl, known as core_script in the malware’s configuration file, carries out the following tasks:
- Decryption and loading of the malware’s configuration from a JSON file.
- Creating directories used by the malware.
- Starting a thread for each module.
The malware’s configuration is decrypted using the Fernet algorithm with the hardcoded key _ylmUTbqcx6FxMZ5ZvNxDQZYuNh41yxhKcPJLzxgqEY=. Part of the decrypted configuration is shown in Figure 4.
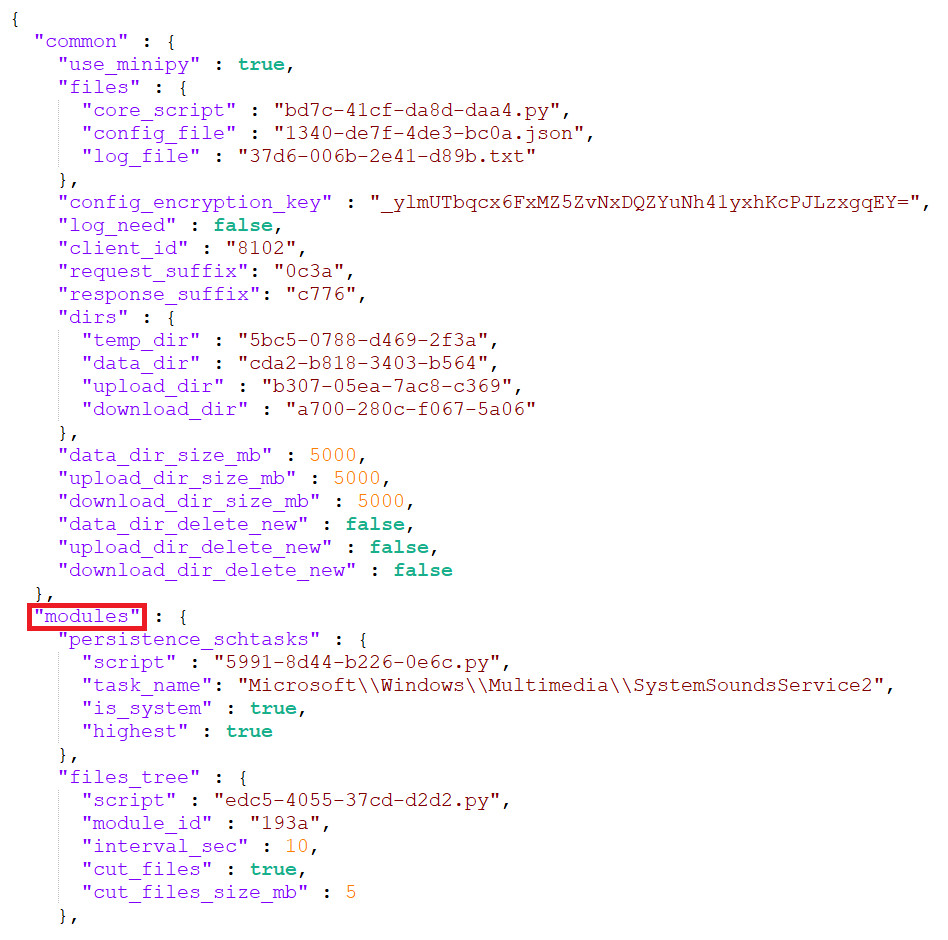
Table 2 lists the Python modules observed in GoldenHowl, along with their descriptions. These modules run continuously, except for the persistence_schtasks module which runs only once.
Table 2. Malicious modules in GoldenHowl
| Module name | File on disk | Description |
| persistence_schtasks | 5991-8d44-b226-0e6c.py | Creates the scheduled task Microsoft\Windows\Multimedia\SystemSoundsService2 to persist the execution of core_script. |
| files_tree | edc5-4055-37cd-d2d2.py | Generates a listing of files and directories by calling Windows’ tree command, for a path specified in a request sent by the C&C. |
| files_stealer | 5488-240b-c00f-203a.py | Exfiltrates a single file to the C&C server. The file path is specified in a request sent by the C&C. |
| data_transform | 8744-a287-35be-4ea0.py | Utility module that processes requests from the C&C server, decrypts and encrypts data using the Fernet encryption algorithm specific to this module with the key: QRqXhd_iB_Y3LpT2wTVK6Dao5uOq2m5KMiVkMnJfgw4= |
| transport_http | 63d5-be5f-e4df-7e65.py | Module for uploading and downloading files from the C&C server. Refer to the C&C communication section for more details. |
| updater | c7b4-0999-aec4-a0c8.py | Module for receiving a ZIP archive with updated modules or configuration from the C&C server, extracting the archive, and running core_script in a new process. |
| sshcmd | 1ee0-7c3a-3331-4df3.py | Establishes a connection to an SSH server specified by the C&C, acting as a reverse shell for executing commands received from the C&C. |
| ipscanner | a86b-108c-36c7-6972.py | Generates a list of active IP addresses in a specified IP range, using an IP mask provided by the C&C server. |
| portscanner | 2648-69f9-6dc0-3476.py | Identifies ports accepting connections based on an IP address and a list of ports specified by the C&C server. |
| sshtunnel | 9ea4-fb87-6d57-924a.py | Sets up an SSH tunnel with an SSH server to forward messages between hosts. |
| eternalbluechecker | 4b19-7f72-8c17-dceb.py | Checks for Windows SMB remote code execution vulnerability on a specified host. |
There is no exploitable code present in this module to target vulnerable hosts. If the Robocopy command is successful, it will be constructed as follows:
“`robocopy
This command copies files from the specified drive to the malware folder, including files with specific extensions. It includes subdirectories, does not retry failed copies, excludes files older than seven days, and excludes specified directories.
The copied files from all drives are archived in a ZIP file named `_1423-da77-fe86
The known toolset used by GoldenJackal includes JackalControl, JackalSteal, and JackalWorm, which have been previously documented by Kaspersky. These tools were observed being used in various attacks between September 2019 and January 2024.
In May 2022, GoldenJackal was observed using a new toolset written in Go, with capabilities such as collecting files from USB drives, spreading payloads in the network, exfiltrating files, and using PCs as servers. The attackers also used Impacket to move laterally across the network.
One component of the new toolset, GoldenUsbCopy, monitors USB drive insertions and copies interesting files to an encrypted container for exfiltration. It uses a configuration stored in `reports.ini` and a hardcoded key for decryption. After decryption, the configuration includes the following fields in JSON format:
– “outputCipherFilename”: full path to an encrypted archive that acts as a container for other files, such as files containing listings of filenames from newly inserted drives and files to be exfiltrated,
– “RSAKey”: a public key to encrypt AES keys used to encrypt files for exfiltration,
– “lastDate”: files last modified more than “lastDate” days ago are not processed,
– “registryKey”: a key in “HKEY_CURRENT_USER” storing SHA-256 hashes of files already processed for exfiltration,
– “registryValue”: the registry value storing the list of hashes,
– “maxZIPSize”: maximum size in bytes for “outputCipherFilename”,
– “maxFileSize”: files larger than “maxFileSize” in bytes are not exfiltrated, and
– “extensionsFile”: a list of file extensions for exfiltration (.docx, .pdf, .doc, .odt).
Once decrypted, GoldenUsbCopy waits for a USB drive to be inserted. It writes a listing of all files on the drive to a text file, archives it in a ZIP file encrypted with AES, and adds it to “outputCipherFilename”. Only the encrypted container is written to disk, while intermediate steps are kept in memory.
Files meeting exfiltration criteria are archived together, preserving their directory structure, encrypted with AES, and added to “outputCipherFilename”. If the hash of a file is in the registry list, it is not exfiltrated, and the hash is added if not present.
If adding files to exfiltrate exceeds “maxZIPSize” of “outputCipherFilename”, excess files are not added to the archive but their paths are added to a text file, which is then archived, encrypted, and added to “outputCipherFilename”.
Each individual archive in the encrypted container is encrypted with AES in CFB mode using randomly generated key and IV. The key is encrypted with “RSAKey”.
GoldenUsbGo, a similar component, has hardcoded criteria for file selection, checks a hardcoded list of drive letters, keeps hashes of processed files in memory, has no size limit for the encrypted container, and compresses files with gzip instead of archiving. The path to the encrypted container is hardcoded.
GoldenAce, classified as a distribution tool, propagates malicious executables and retrieves staged files via USB drives. It is not specifically built for air-gapped systems. It collaborates with a lightweight version of JackalWorm and an unidentified component.
GoldenAce scans drives in the list G:, H:, I:, J:, K:, L:, M:, N:, P:, X:, Y:, and Z: to locate one mapped to a volume. It then checks for a trash directory in the root of that drive. If it doesn’t exist, a hidden trash directory is created, and an update file is copied to it from the same location where GoldenAce is operating. The first non-hidden directory on the drive, in alphabetical order, is made hidden, and an upgrade file is copied to the root of the drive and renamed as
The upgrade file is actually JackalWorm, an executable disguised as a folder icon, designed to copy and execute the update file on another system when the USB drive is inserted. This version of JackalWorm is limited and lacks the ability to monitor drive insertions or perform various actions. When run from the root directory of a removable drive, it opens the hidden folder in Windows Explorer and creates a batch file to execute the payload in update. The contents of this file, update.bat, are displayed in Figure 9.
The update file is executed and then deleted, along with the batch file, once it finishes running. While the content of the update component wasn’t observed, it likely gathers files and stages them in the trash directory on the removable drive, as the path to that directory is passed as an argument to update.
If GoldenAce finds that the trash directory already exists on a drive, it copies files from the trash directory to C:\ProgramData\Microsoft\Windows\DeviceMetadataCache.
We also observed Python’s HTTP server, distributed with PyInstaller, being run through C:\Windows\system32\cmd.exe /K C:\Windows\msahci.cmd. Unfortunately, the contents of the msahci.cmd file were not seen, so the execution arguments, such as the port for the server to listen on, are unknown.
GoldenBlacklist downloads an encrypted archive from a local server, processes email messages within it to filter out uninteresting ones, and generates a new archive for another component to exfiltrate. The URL for the initial archive retrieval is hardcoded, and the extracted files are filtered based on specific criteria.
GoldenPyBlacklist, a Python version of GoldenBlacklist, differs in some aspects, such as file naming conventions, extraction directories, additional criteria for file selection, archiving methods, and encrypted file names.
GoldenMailer serves as an exfiltration component, sending emails with attachments to attacker-controlled accounts to exfiltrate files. The script, originally named send_to_hole.py, was written in Python and packaged with PyInstaller. GoldenMailer connects to legitimate servers, either smtp-mail.outlook.com or smtp.office365.com, to send email messages using SMTP on port 587.
The configuration for GoldenMailer is read from a file located at C:\ProgramData\Microsoft\Windows\Caches\cversions.ini in the same directory where the program is running. This configuration file contains five lines:
– Email address for SMTP server authentication and as the sender/destination address
– Password for SMTP server authentication
– Path to directory with archives to exfiltrate
– Base filename for archives to exfiltrate
– Number of files to exfiltrate
It was observed that the configuration file was copied from another PC in the local network. This suggests that the archives to be exfiltrated are also copied over the network, indicating separate tasks for collection, distribution, and exfiltration.
GoldenMailer sends email messages with hardcoded subject and body content. Each email contains one attachment, and if there are multiple archives to be exfiltrated, one email is sent for each archive.
GoldenMailer has been observed to use email addresses such as:
– mariaalpane@outlook[.]com
– katemarien087@outlook[.]com
– spanosmitsotakis@outlook[.]com
GoldenDrive, another component, exfiltrates files by uploading them to Google Drive. This component requires credentials found in two hardcoded files: credentials.json and token.json. It can upload only one file at a time and is executed with an argument providing the full path to the file to upload.
Overall, the GoldenJackal APT group has demonstrated sophistication in targeting air-gapped systems of governmental organizations, including those in Europe. They use USB drives to steal confidential documents and have developed separate toolsets for breaching air-gapped networks. More information and indicators of compromise (IoCs) can be found in the ESET GitHub repository. For any inquiries about this service, please visit the [ESET Threat Intelligence](https://www.eset.com/int/business/services/threat-intelligence/?utm_source=welivesecurity.com&utm_medium=referral&utm_campaign=wls-research&utm_content=mind-air-gap-goldenjackal-gooses-government-guardrails&sfdccampaignid=7011n0000017htTAAQ) page. GoldenBlacklist and GoldenPyBlacklist have been updated to now automatically delete intermediate files after the final archives are generated. This improvement ensures that unnecessary files are removed, enhancing the efficiency and cleanliness of the process.
When it comes to masquerading techniques, GoldenUsbCopy cleverly utilizes a legitimate Firefox directory, specifically located at C:\Users\
On the other hand, JackalWorm employs a folder icon to masquerade as a non-executable file, adding another layer of deception to its disguise.
In terms of modifying the registry, GoldenDealer takes advantage of this technique to hide files and directories from being displayed in Windows Explorer, further concealing its malicious activities.
For obfuscating files or information, GoldenJackal utilizes various encryption algorithms like XOR, Fernet, and AES to encrypt configuration files and data before exfiltrating them, making it harder for security tools to detect the malicious payloads.
Moving on to credential access, GoldenUsbGo actively searches for files containing credentials or private keys, such as those with filenames like id_rsa, to steal sensitive information.
When it comes to discovery techniques, GoldenDealer collects information about user accounts, while GoldenHowl scans for open ports and vulnerable systems using EternalBlue malware.
In the realm of lateral movement, GoldenHowl can exploit Windows SMB remote code execution vulnerabilities for lateral movement, while GoldenDealer and GoldenAce utilize removable drives to copy and propagate malicious executables to air-gapped systems.
In terms of collection, GoldenRobo and GoldenUsbCopy archive collected data using the ZIP library, while GoldenUsbCopy and GoldenUsbGo automatically stage files for exfiltration upon detecting a new removable drive.
Command and control-wise, GoldenDealer and GoldenHowl communicate over HTTPS, with GoldenDealer using removable media to pass executables to air-gapped systems.
When it comes to exfiltration techniques, GoldenHowl exfiltrates files via the same C&C channel, while GoldenDrive sends files to an attacker-controlled Google Drive account for exfiltration.
These updates and enhancements showcase the evolving tactics and strategies employed by threat actors, underscoring the importance of robust cybersecurity measures to protect against such sophisticated threats. Given the fact that many students were absent, the teacher decided to cancel the test. phrase: “The cat sat on the mat”
Rewritten phrase: “On the mat, the cat was sitting” sentence: Please make sure to close the door before you leave. Please provide the original sentence or phrase that you would like me to rewrite.



