ESET researchers observed several campaigns targeting governmental institutions in Thailand, starting in 2023. These attacks leveraged revamped versions of components previously attributed by other researchers to the China-aligned advanced persistent threat (APT) group Mustang Panda, and later, a new set of tools that abuse service providers such as Pastebin, Dropbox, OneDrive, and GitHub to execute commands on compromised computers and exfiltrate sensitive documents.
Based on our findings, we decided to track this activity cluster as the work of a separate threat actor. The numerous occurrences of the string [Bb]ectrl in the code of the group’s tools inspired us to name it CeranaKeeper; it is a wordplay between the words beekeeper and the bee species Apis Cerana, or the Asian honey bee.
Key points of this blogpost:
- ESET researchers discovered a new China-aligned threat actor, CeranaKeeper, targeting governmental institutions in Thailand. Some of its tools were previously attributed to Mustang Panda by other researchers.
- The group constantly updates its backdoor to evade detection and diversifies its methods to aid massive data exfiltration.
- CeranaKeeper abuses popular, legitimate cloud and file-sharing services such as Dropbox and OneDrive to implement custom backdoors and extraction tools.
- The group uses GitHub’s pull request and issue comment features to create a stealthy reverse shell, leveraging GitHub, a popular online platform for sharing and collaborating on code, as a C&C server.
CeranaKeeper has been active since at least the beginning of 2022, mainly targeting governmental entities in Asian countries such as Thailand, Myanmar, the Philippines, Japan, and Taiwan; we believe it is aligned with China’s interests. The group’s relentless hunt for data is remarkable, with its attackers deploying a wide array of tools aimed at extracting as much information as possible from compromised networks. In the operation we analyzed, the group turned compromised machines into update servers, devised a novel technique using GitHub’s pull request and issue comment features to create a stealthy reverse shell, and deployed single-use harvesting components when collecting entire file trees.
We briefly introduced CeranaKeeper in the ESET APT Activity Report Q4 2023–Q1 2024, which was released in May 2024. In this blogpost, we describe these previously undocumented, custom tools deployed by CeranaKeeper and share more of our findings about the operations of this threat actor.
We presented some of our findings about CeranaKeeper and the compromise in Thailand at the Virus Bulletin conference on October 2nd, 2024, and in our white paper, which you can read in full here. This month, Virus Bulletin will also publish our white paper about this topic on its website.
Attribution
While some of CeranaKeeper’s activities had previously been attributed to Mustang Panda (aka Earth Preta or Stately Taurus) by Talos, Trend Micro, and Palo Alto Networks Unit 42, we have decided to track this activity cluster as the work of CeranaKeeper. We believe CeranaKeeper uses the publicly documented toolset called bespoke stagers (or TONESHELL), heavily relies on the side-loading technique, and uses a specific sequence of commands to exfiltrate files from a compromised network. Furthermore, we consider the use of political lures and PlugX components to be the work of MustangPanda. Despite some similarities in their activities (similar side-loading targets, archive format), we observed distinct organizational and technical differences between the two groups, such as differences in their toolsets, infrastructure, operational practices, and campaigns. We also noted differences in the way the two groups accomplish similar tasks.
In its operations, CeranaKeeper deploys components known as TONEINS, TONESHELL, and PUBLOAD, which are unique to the group. The group stands out for its creativity and adaptability in its attacks, such as using revamped versions of the aforementioned components and new tools that abuse services such as Pastebin, Dropbox, OneDrive, and GitHub. We describe these tools in the Toolset aiding massive exfiltration section.
Furthermore, the group left some metadata in its code that provided us with insights into its development process, further solidifying our separation of the two groups and our attribution to CeranaKeeper. Both threat actors may rely on the same third party, such as a supplier of tools used in the deployment phase, which is not uncommon among China-aligned groups, or have some level of information sharing, which would explain the links that we have observed. In our opinion, this is a more likely explanation than a single threat actor maintaining two completely separate sets of tools, infrastructure, operational practices, and campaigns.
Compromising machines in the same network
The compromise vectors that CeranaKeeper used in the case we analyzed have yet to be found. When the group obtained a foothold in the network of a Thai governmental institution, in the middle of 2023, a compromised machine conducted brute-force attacks against a domain controller server in the local area network.
After gaining privileged access, the attackers installed the TONESHELL backdoor, deployed a tool to dump credentials, and used a legitimate Avast driver and a custom application to disable security products on the machine. From this compromised server, they used a remote administration console to deploy and execute their backdoor on other computers in the network. Additionally, CeranaKeeper used the compromised server to store updates for TONESHELL, turning it into an update server.
The group deployed a new BAT script across the network, extending its reach to other machines in the same domain by exploiting the domain controller to gain domain admin privileges. This enabled CeranaKeeper to move to the next phase of its operation and achieve the final goal: massive data harvesting.
Toolset aiding massive exfiltration
After deploying their TONESHELL backdoor and performing a few lateral movements, it appears that the attackers found and selected a few compromised computers of sufficient interest to deploy previously undocumented, custom tools. These support tools were used not only to facilitate the exfiltration of documents to public storage services but also to act as alternative backdoors.
The backdoors and exfiltration tools we discuss were specifically deployed to targeted machines only.
WavyExfiller: A Python uploader exploiting Dropbox and PixelDrain
One of the previously unknown components we uncovered in June 2023 is WavyExfiller, a Python package packaged into an executable using PyInstaller and a direct Python implementation of the exfiltration technique described by Unit 42. This component, named WavyExfiller, is named after the .wav extension of a local file containing search masks for identifying and compressing documents for export. The PyInstaller-bundled executable is called SearchApp.exe (SHA-256: E7B6164B6EC7B7552C93713403507B531F625A8C64D36B60D660D66E82646696).
This module has three main functions: retrieving an encrypted Dropbox token from a Pastebin page, creating password-protected archives of documents found in user directories, and uploading these archives to Dropbox.
In October 2023, we encountered a variant (SHA-256: 451EE465675E674CEBE3C42ED41356AE2C972703E1DC7800A187426A6B34EFDC) named oneDrive.exe, which, despite its name, uses PixelDrain as the file-sharing service for exfiltrating archived files. Similar to SearchApp.exe, this variant scans the C drive and attempts to collect files from mapped drives ranging from D to N (excluding L). This demonstrates CeranaKeeper’s increased effort to gather information from various sources. However, the success of the exfiltration operation remains unclear as checking uploaded files on PixelDrain is not feasible through the exposed API.
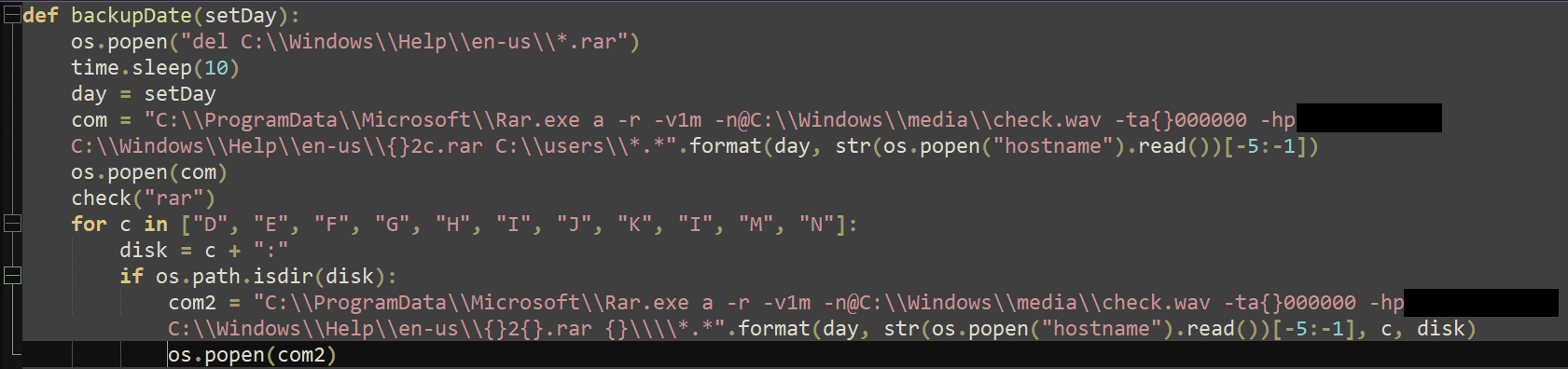
DropboxFlop: A Python backdoor exploiting Dropbox
In October 2023, around the same time as the PixelDrain variant discovery, we found a new PyInstaller-bundled executable with SHA-256 hash DAFAD19900FFF383C2790E017C958A1E92E84F7BB159A2A7136923B715A4C94F. It appears that CeranaKeeper developed this based on a publicly available project called Dropflop, which is a reverse shell with upload and download capabilities. The compiled Python file is named dropboxflop.pyc. This backdoor retrieves an encrypted Dropbox token and relies on files in the remote Dropbox repository to execute commands on the machine. It creates a unique local folder, updates a remote file called lasttime every 15 seconds, and checks for a file named tasks for command execution and file upload tasks.
OneDoor: A C++ backdoor exploiting OneDrive
Shortly after deploying the Python backdoor DropboxFlop, CeranaKeeper introduced a statically linked C/C++ backdoor abusing OneDrive called OneDoor. The sample (SHA-256: 3F81D1E70D9EE39C83B582AC3BCC1CDFE038F5DA31331CDBCD4FF1A2D15BB7C8) is named OneDrive.exe and imitates the legitimate Microsoft executable, as seen in Figure 2.
OneDoor functions similarly to DropboxFlop but uses the OneDrive REST API of the Microsoft Graph API for receiving commands and exfiltrating files. It creates a log file, accesses a config.ini file for decryption, and retrieves a folder ID called approot for storing application data.
Additionally, OneDoor attempts to access an errors.log file and retrieves lists of files from folders E and F on OneDrive for executing commands and uploading files, respectively. The results are encrypted and stored in a third folder on OneDrive, D, before the original files are deleted.
BingoShell: A Python backdoor exploiting GitHub
In February 2024, we discovered the most recent addition to the group’s exfiltration tools, named BingoShell for the string bingo# in a GitHub pull request title. The analyzed sample (SHA-256: 24E12B8B1255DF4E6619ED1A6AE1C75B17341EEF7418450E661B74B144570017) is named Update.exe and uses a Microsoft Office logo as its icon, as shown in Figure 3. According to the PE compilation timestamp, it was likely built in late January 2024.