Enhance your file investigations with the latest string reuse capabilities in Intezer Analyze
Intezer Analyze users can now take advantage of the enhanced string features within the platform. These advanced string reuse capabilities simplify the process of analyzing suspicious files using Genetic Malware Analysis.
- Effortlessly search for relevant strings that offer valuable insights into the nature of a potential threat
- Filter strings by tags (such as network artifact, file path), family type (malware, admin tool, packer, library), and specific malware family (Lazarus, TrickBot)
- Easily pivot between related samples that share the same strings
Unveiling the secrets hidden within strings
Unlike binary code, strings are more straightforward to interpret. Extracting relevant strings can shed light on program functionality and provide clues about the indicators associated with a suspicious binary. Strings may include references to filenames, domain names, URLs, IP addresses, attack commands, registry keys, and more. While strings may not always offer a complete picture of a file’s purpose or capabilities, certain strings can hint at the potential actions of malware (via Packt>).
Discover revealing strings
Identifying pertinent strings, such as filenames or domain names, can bolster a security analyst’s understanding of a file’s intentions. In some instances, strings can aid in classifying malware.
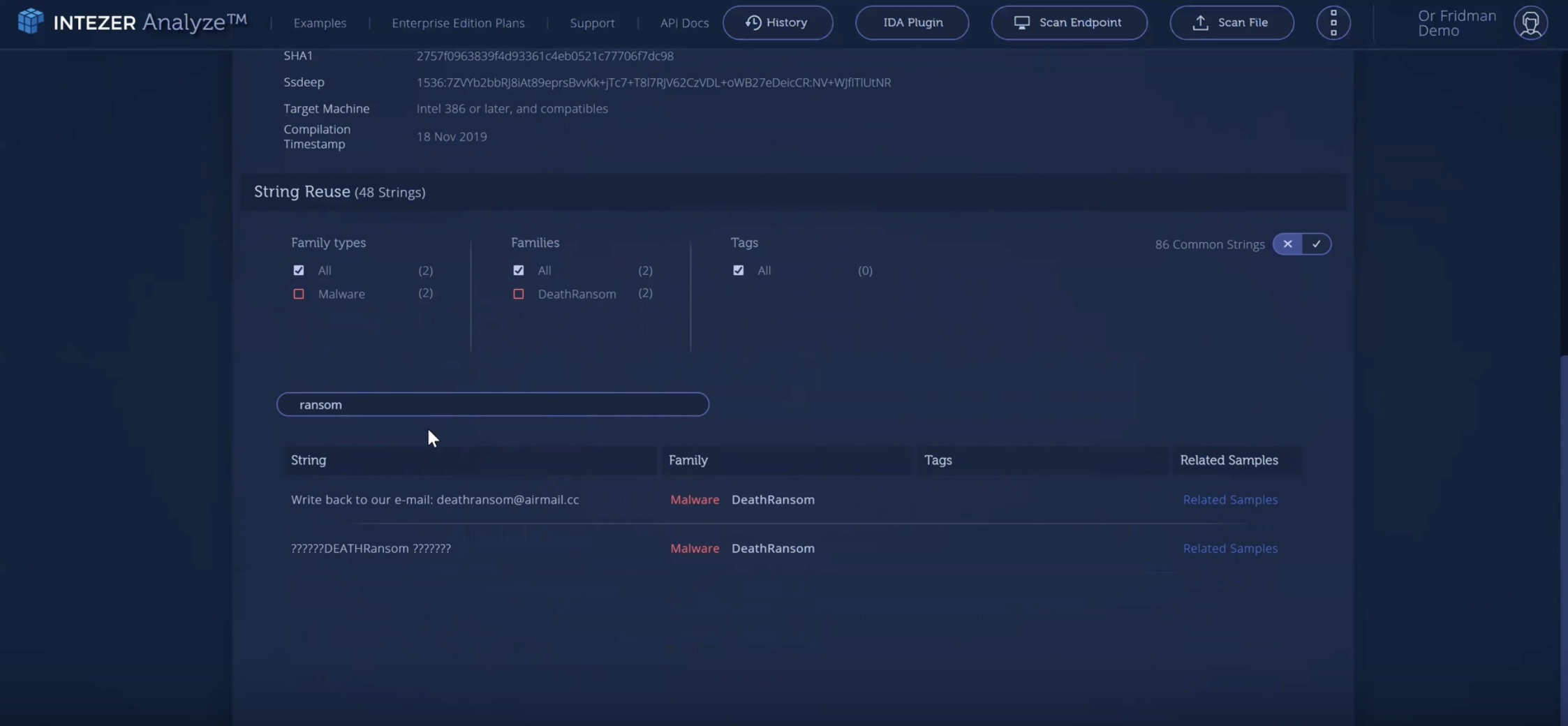
In Intezer Analyze, you can now perform targeted searches for specific text, eliminating the need to manually review each string. Try it out by searching for “ransom” in the analysis of DeathRansom below.

Two results indicating a ransomware attack further validate the findings. This information can expedite the investigation process, allowing organizations more time to strategize their response to the threat.
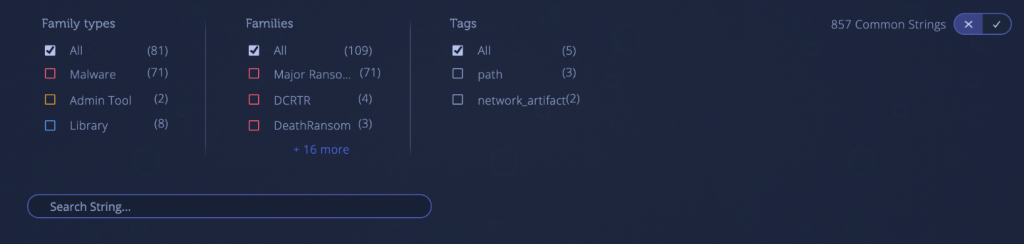
Efficiently filter strings by tags and malware family
Utilize tags to filter strings based on attributes like path and network artifact. You can also segregate strings by malware families that share common characteristics (such as Major Ransomware, DCRTR, and DeathRansom in the example below).

Seamlessly pivot between related samples
In addition to exploring related samples based on shared code, users can now navigate between malware samples that share common strings. This feature enriches investigations and provides additional insights into potential incidents or targeted attacks on your organization. Simply click on “related samples” on the right to view samples based on string reuse.
Intezer Analyze: Empowering all users
Do you have a suspicious file that demands investigation? Upload it to Intezer Analyze to uncover any malicious code it may contain. Try it for free now
Explore Intezer Analyze’s endpoint analysis feature while working remotely
Identify code similarities across all executable code running on your device to detect malicious code injections, fileless malware, and other potential threats. Experience it for free in the community edition.