When suspicious activity is detected on an endpoint, the incident response team is tasked with investigating to determine the cause of the potential security breach. Is it a rapidly spreading malware, or just a false positive? For individuals in digital forensics and incident response, it is crucial to quickly ascertain the nature of the threat, while also avoiding wasting time on false alarms.
There are various methods for collecting files and forensic evidence, which we will explore below along with tips and free tools to streamline each process during incident response. Here are three key areas where you can expedite investigations:
- HD forensics: Gathering suspicious files based on a predefined incident response plan
- Memory forensics: Extracting the memory dump of the compromised endpoint using tools
- Live forensics: Analyzing the runtime of the compromised endpoint
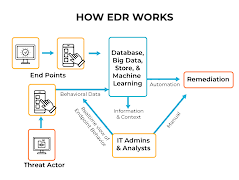
One of the most time-consuming processes in incident response is determining whether the suspicious activity was a false positive or an actual infection. Identifying the compromised endpoint(s) in the network and the malicious artifacts used in the attack can also be arduous. This analysis must be thorough to ensure no vital information is overlooked, akin to finding a needle in a haystack.
Given the importance of time in mitigating potential damage during incidents, the pressure to conduct efficient incident investigations is high. This necessitates having efficient procedures and tools at your disposal to prevent unnecessary delays.
Intezer Analyze is a free tool that aids in quickly classifying and analyzing files collected through various forensic methods. Let’s delve into how incident response teams leverage Intezer and other tools to gain insights into forensic artifacts promptly.
HD Forensics and Classifying Collected Files
One method of collecting forensic evidence involves imaging the compromised endpoint’s filesystem. While this captures a copy of the entire filesystem, the extracted data can be voluminous and time-consuming to analyze. Signature-based analysis is often used to compare extracted data against known malicious hashes, but this approach may miss new malware variants.
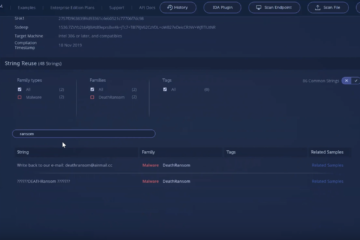
Intezer Analyze employs a unique code comparison technology that breaks down executable files into binary code patterns, known as code genes. These genes are compared against Intezer’s extensive database of code pieces from both trusted and malicious sources. By identifying shared code, Intezer can quickly flag a file as malicious and classify it into the corresponding malware family.
Submitting files for analysis with Intezer Analyze can be done online via the web interface or through scripts that handle bulk submissions. The output provides details on files identified as malicious or suspicious, saving time on manual classification and analysis.
Analyzing Memory Dumps to Improve Incident Response Time
Another source of forensic evidence is the volatile memory of compromised endpoints. By leveraging tools like Volatility with Intezer’s plugin, incident responders can conduct a full code reuse analysis of memory dumps swiftly. This approach enhances the efficiency of classifying threats and their capabilities compared to traditional methods.
Scan Compromised Endpoints to Detect Threats Loaded In-Memory
Scanning the runtime environment of compromised endpoints enables the detection of malicious processes that may have evaded other security tools. Using tools like Intezer Analyze’s endpoint scanner, investigators can quickly identify and analyze loaded processes, streamlining the incident response process.
The tools and features discussed in this article are designed to simplify and optimize the incident response process. Whether it’s file analysis, memory dump examination, or endpoint scanning, these tools can help incident responders save time and make informed decisions during investigations.
Tools mentioned in this article:
File analysis with Intezer Analyze
IDA Pro plugin
Ghidra plugin
Endpoint scanner
Intezer’s SDK