In this blogpost we discuss an uncommon type of phishing campaign targeting mobile users and analyze a case that we observed in the wild that targeted clients of a prominent Czech bank. This technique is noteworthy because it installs a phishing application from a third-party website without the user having to allow third-party app installation. For iOS users, such an action might break any “walled garden” assumptions about security. On Android, this could result in the silent installation of a special kind of APK, which on further inspection even appears to be installed from the Google Play store.
The phishing websites targeting iOS instruct victims to add a Progressive Web Application (PWA) to their home-screens, while on Android the PWA is installed after confirming custom pop-ups in the browser. At this point, on both operating systems, these phishing apps are largely indistinguishable from the real banking apps that they mimic. PWAs are essentially websites bundled into what feels like a standalone application, with this feeling being enhanced by the usage of native system prompts. PWAs, just like websites, are cross-platform, explaining how these PWA phishing campaigns can target both iOS and Android users.
This technique was first disclosed by CSIRT KNF in Poland in July 2023 and, in November 2023, observed in Czechia by ESET analysts working on the Brand Intelligence service. We also observed two cases of mobile campaigns against banks outside of Czechia: one case targeting the Hungarian OTP Bank and another targeting the Georgian TBC Bank.
Key points of the blogpost:
- Standard phishing delivery techniques were combined with a novel method of phishing; targeting Android and iOS users via PWAs, and on Android also WebAPKs.
- Insidiously, installing a PWA/WebAPK application does not warn the victim about installing a third-party application.
- On Android, these phishing WebAPKs even appear to have been installed from the Google Play store.
- Most of the observed applications targeted clients of Czech banks, but we also observed one phishing app that targeted a Hungarian bank and another targeting a Georgian bank.
- Based on the C&C servers utilized and backend infrastructure, we conclude that two different threat actors were operating the campaigns.
- Thanks to our discovery of operator panels on different domains, we were able to notify the victims’ banks in order to protect them.
Overview
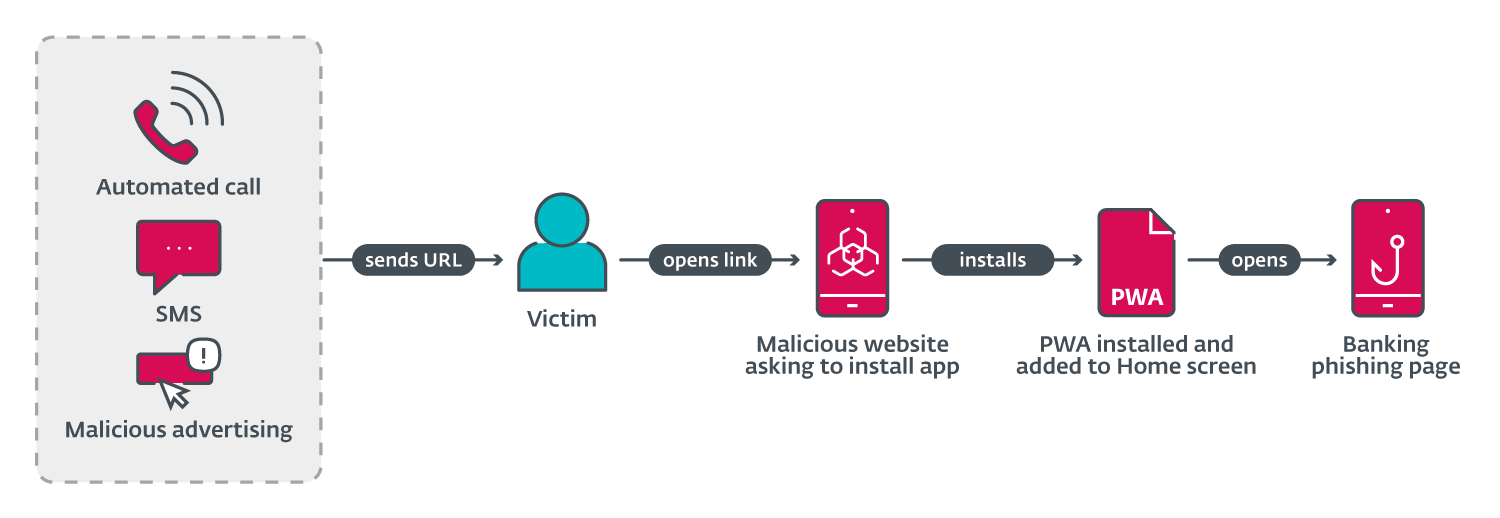
ESET analysts discovered a series of phishing campaigns targeting mobile users that used three different URL delivery mechanisms (shown in Figure 1). These mechanisms include automated voice calls, SMS messages, and social media malvertising.
The voice call delivery is done via an automated call that warns the user about an out-of-date banking app and asks the user to select an option on the numerical keyboard. After pressing the correct button, a phishing URL is sent via SMS. This was reported in a tweet, by Michal Bláha.
Initial delivery by SMS was performed by sending messages indiscriminately to Czech phone numbers. The message sent included a phishing link and text to socially engineer victims into visiting the link.
Spreading via malicious ads was done by registering advertisements on Meta platforms like Instagram and Facebook. These ads included a call to action, like a limited offer for users who “download an update below”. This technique allows threat actors to specify the target audience by age, gender, etc. The advertisements would then appear in a victim’s social media feed.
After opening the URL delivered in the first stage, Android victims are presented with a high-quality phishing page imitating the official Google Play store page for the targeted banking application, or a copycat website for the application. These were two distinct campaigns. It is possible that the campaign utilizing Google Play visuals would modify itself based on the received User-Agent, to imitate Apple Store visuals. We did not observe this technique in analyzed cases.
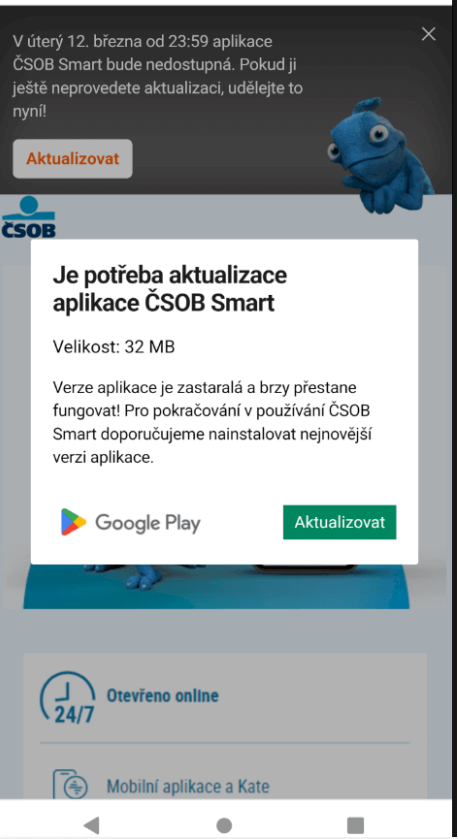
From here victims are asked to install a “new version” of the banking application; an example of this can be seen in Figure 2. Depending on the campaign, clicking on the install/update button launches the installation of a malicious application from the website, directly on the victim’s phone, either in the form of a WebAPK (for Android users only), or as a PWA for iOS and Android users (if the campaign is not WebAPK based). This crucial installation step bypasses traditional browser warnings of “installing unknown apps”: this is the default behavior of Chrome’s WebAPK technology, which is abused by the attackers.
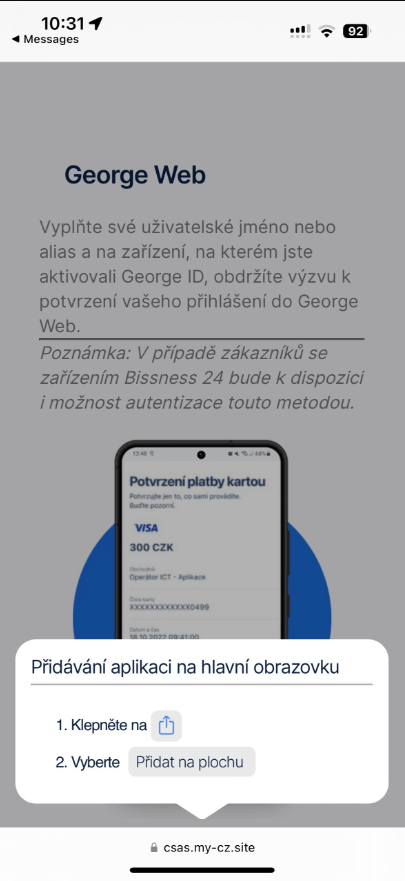
The process is a little different for iOS users, as an animated pop-up instructs victims how to add the phishing PWA to their home screen (see Figure 3). The pop-up copies the look of native iOS prompts. In the end, even iOS users are not warned about adding a potentially harmful app to their phone.
After installation, victims are prompted to submit their internet banking credentials to access their account via the new mobile banking app. All submitted information is sent to the attackers’ C&C servers.
Timeline
We discovered the first phishing-via-PWA case in early November 2023, and noticed the transition to WebAPKs in mid-November 2023. C&C servers that received information from phishing applications were first discovered in March 2024 (as can be seen in Figure 4), with data in them confirming that they were probably not operational earlier.
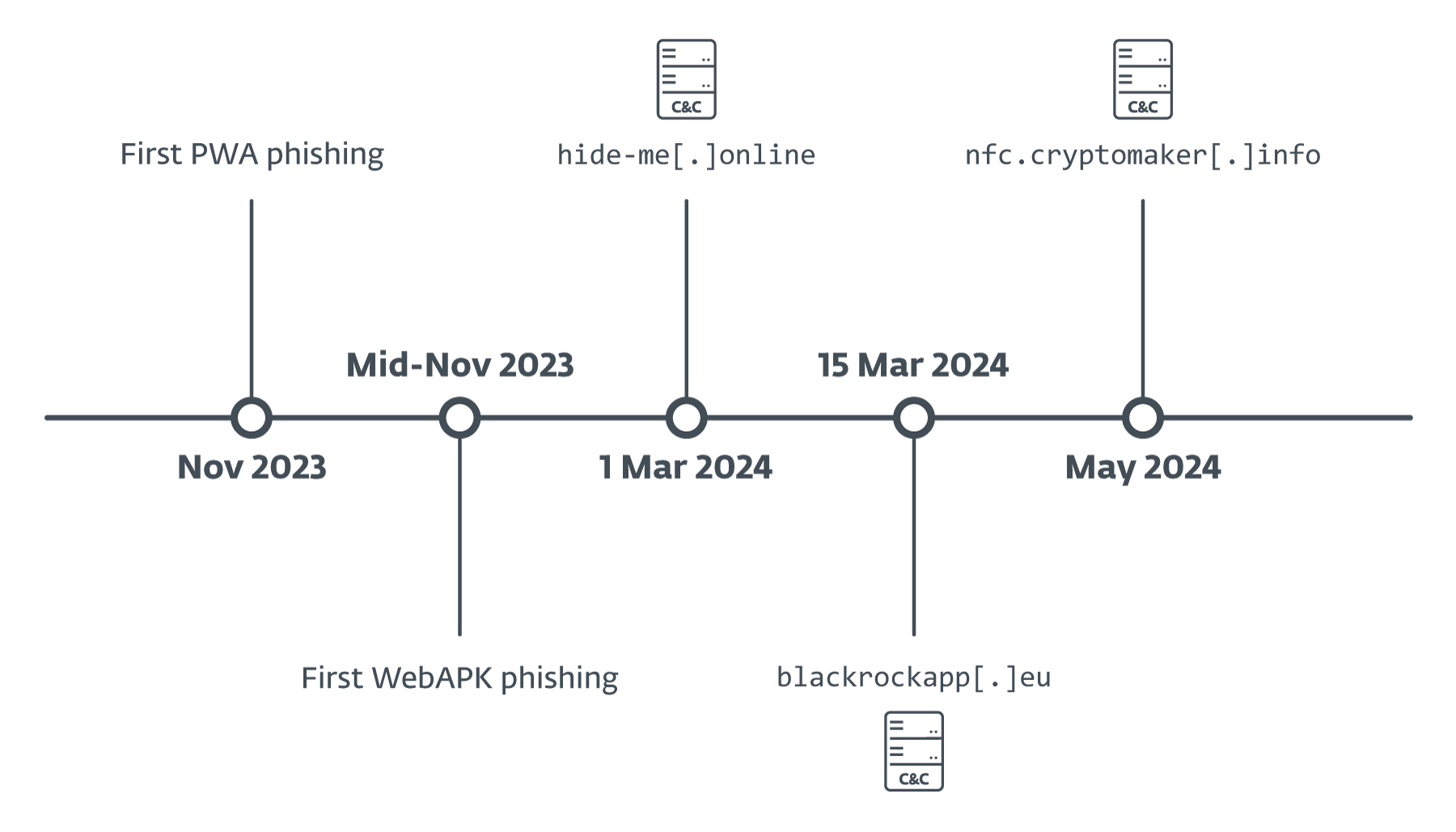
The only exception is the cryptomaker[.]info server, which we discovered in May 2024, but included activity from a campaign against the Georgian TBC Bank in February 2024.
Technical analysis
In this section we focus on the analysis of a campaign against a prominent Czech bank, utilizing WebAPK technology.
We also provide a brief explanation of the underlying technology behind progressive web applications (PWAs) and WebAPKs.
PWAs are applications developed using traditional web application technologies that can operate on various platforms and devices. These apps are installed on the user’s mobile phone after a pop-up installation prompt is displayed or the user manually selects the “Install app” option from a supported browser’s menu. The key feature of PWAs is their installation, which allows for seamless usage in a separate window and the ability to be launched from the menu bar or home screen. PWAs also use a single codebase across multiple platforms and can operate offline using service workers. These workers act as a proxy system, retrieving data from the local cache when there is no internet connection.
WebAPKs are an enhanced version of PWAs where the Chrome browser generates a native Android application (APK) from a PWA. These WebAPKs resemble regular native apps and do not trigger warnings about installation from untrusted sources. The generation of WebAPKs is currently supported only by Google Chrome. In a phishing scheme, WebAPKs are used to deceive users into thinking that the installed phishing app is a legitimate banking application.
Overall, PWAs and WebAPKs utilize modern browser APIs, service workers, and native code to provide a seamless and interactive user experience across different platforms and devices. Android users were directed to download a WebAPK, while iOS users were guided towards PWAs.
Once installed, the phishing PWA/WebAPK was placed on the user’s home screen, leading them to a phishing login page directly within the application. This can be seen in Figure 13.
Additionally, the app’s information tab indicated that it was downloaded from the Google Play store by default, as shown in Figure 14. This behavior applied to all WebAPK apps.
The phishing application and URL mentioned in this article were reported to ČSOB and were never available on the Google Play store.
C&C Infrastructure
Two separate groups operated the PWA/WebAPK phishing campaigns against Czech and other banks, utilizing different C&C infrastructures. One group used a Telegram bot to log user information, while the other utilized a traditional C&C server with an administrative panel.
Telegram bots were employed to log all entered data into a Telegram group chat via the official Telegram API. On the other hand, the traditional C&C server contained an administrative panel with sensitive victim information, active phishing URLs, and a history of victims.
The threat actors behind these campaigns were active in setting up new domains and launching new malicious campaigns. The information gathered from the C&C infrastructure allowed us to notify affected banks and protect their clients.
In conclusion, a novel phishing method combining social engineering techniques with PWA applications was identified. It primarily targeted Android users, with a few instances outside of Czechia. Due to the different C&C infrastructures used, it was determined that multiple groups were responsible for spreading these phishing apps.
As more copycat applications are expected to surface, it becomes challenging to distinguish between legitimate and phishing apps post-installation. All sensitive information discovered during our research was promptly shared with the relevant banks for further action.
For any inquiries regarding our research featured on WeLiveSecurity, please reach out to us at threatintel@eset.com. ESET Research also provides private APT intelligence reports and data feeds, which can be explored on the ESET Threat Intelligence page.
IoCs
Files:
– SHA-1
– Filename
– Detection
– Description
Network:
– IP
– Domain
– Hosting provider
– First seen
– Details
MITRE ATT&CK Techniques
Tactic
ID
Name
Description
Initial Access
T1660
Phishing
Applications are distributed through malicious advertising or mass phishing, with the application itself used for phishing post-installation.
Credential Access
T1417.002
Input Capture: GUI Input Capture
Credentials are harvested by mimicking the login pages of targeted banks.
Command and Control
T1437.001
Application Layer Protocol: Web Protocols
PWA/WebAPK phishing apps transmit login data via JavaScript interfaces and track data.
Feel free to reach out for more information on our research or services. text to make it more concise:
Please rewrite the text to be more concise. sentence to improve clarity:
The new manager is not only responsible for overseeing the daily operations of the department but also for implementing new strategies for growth.



