Memory forensics plays a crucial role in incident response and threat analysis in the ever-evolving cybersecurity landscape. Unlike traditional methods that focus on hard drive analysis, memory forensics delves into volatile memory to uncover evidence of malware infections and illicit activities that leave traces in a system’s RAM.
Investigators utilize memory forensics to gather valuable information and evidence from compromised systems. As threat actors employ various techniques to evade detection, fileless malware poses a significant challenge. Memory forensics proves to be a valuable tool in such scenarios.
Memory forensics involves analyzing a computer’s memory contents to identify potential security threats or forensic evidence. This analysis is crucial post-security breach or as part of a proactive security assessment. By examining raw binary data in memory, investigators can access information on running processes, network connections, previously executed commands, and malware artifacts.
Throughout our exploration of memory forensics, we will discuss its applications, challenges faced by practitioners, differences between in-memory and disk-based threats, and the leading tools and methodologies in this field. For those familiar with memory forensics basics, you can jump to the section on Memory Forensic Tools in Action.
Our aim is to emphasize the critical role of memory forensics in contemporary cybersecurity strategies and the ongoing battle against digital threats hidden in our systems’ memory.
What Is Memory Forensics?
Memory forensics involves capturing and analyzing a computer’s memory to uncover valuable digital artifacts. These artifacts can include details about running processes, open files, network connections, system configurations, and evidence of malware or hacker activity that may go undetected through traditional disk-based analysis.
Memory forensics is a specialized branch of digital forensics that focuses on volatile data in a computer’s memory (RAM), rather than data stored on hard drives or other permanent storage media. The transient nature of RAM data poses unique challenges and opportunities for forensic analysts.
Types of Data Retrieved
Memory forensics can retrieve various data types that provide insights into the system’s state at the time of capture. These data types include details about running processes, network connections, binary executables, loaded DLLs, registry keys, configuration settings, and digital artifacts.
On-Disk vs. In-Memory Cyber Attacks
The distinction between in-memory and on-disk threats lies in their operation and persistence mechanisms, presenting unique challenges for detection and mitigation. In-memory threats and fileless malware operate solely in a system’s volatile memory, evading traditional antivirus and disk-based forensics tools. On the other hand, on-disk threats involve malware or malicious activities that persist on non-volatile storage.
Challenges of Manual Memory Forensics
Despite its importance, manual memory forensics presents challenges due to technical, logistical, and operational factors. The volatile nature of memory, large data volume, and data integrity maintenance are some technical challenges. Logistical challenges include collection difficulties and the skill gap required for memory forensics.
There is a notable skill gap in the industry, as there is a shortage of professionals who understand advanced analysis techniques.
Moreover, the process of memory capture and analysis must consider legal and ethical considerations, particularly in relation to privacy and data protection laws. Analysts must ensure compliance with these regulations, adding complexity to forensic investigations.
To address these challenges, advancements in tools, techniques, and training are being utilized to make memory forensics more manageable. Automation and machine learning are being leveraged to analyze large datasets efficiently, while community-driven efforts are improving knowledge sharing and best practices. Additionally, the development of more intuitive and powerful forensic tools is making memory forensics more accessible to a wider range of professionals.
In terms of specific memory threats, examples include the use of tools like Cobalt Strike, Operation HamsaUpdate, and hijacking execution flow through DLL Side-Loading. These threats highlight the need for effective memory forensics tools and practices to detect and mitigate malicious activities.
Some existing tools for memory forensics include the Volatility Framework, YARA, WinPmem, Memoryze, and GRR, each offering unique capabilities for analyzing memory dumps and identifying suspicious activities. These tools play a crucial role in conducting manual analysis and investigation of memory artifacts.
Overall, memory forensics is a critical aspect of cybersecurity and requires a combination of expertise, tools, and best practices to effectively detect and respond to memory-based threats.
If you use Volatility, you can also examine all the network connections established at the time the image was captured. To make it easier to read, consider saving the results to a text file instead of scrolling through the terminal.
python3 vol.py -f <your_memory_dump.raw> windows.netscan > netscan.txtPerhaps the connection to 10.0.0.13 seems suspicious?
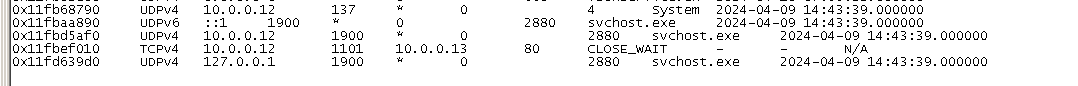
Another useful plugin in Volatility is the “malfind” plugin. It helps identify hidden or injected code/DLLs in user mode memory by analyzing characteristics like VAD tag and page permissions. The malfind plugin detects anomalies or indicators that suggest the presence of injected code, such as executable code in non-executable memory regions or unexpected changes in memory protection flags.
python3 vol.py -f <your_memory_dump.raw> windows.malfind.Malfind > malfind.txtThe malfind results show various findings, including some from legitimate programs like Microsoft Edge. However, one result stands out, which is “my_payload.exe”.

One noticeable snippet is the shellcode resembling the Reflective Loader Stub for Cobalt Strike. This annotated snippet provides insights into the potential Cobalt Strike infection.
pop r10 ; MZ Header push r10 ; undo action above
push rbp ; save the stack base pointer
mov rbp, rsp ; create a new stack frame
sub rsp, 0x20 ; create shadow space (x64 __fastcall)
lea rbx, [rip – 0x16] ; obtain shellcode base address
mov rdi, rbx ; save shellcode base address
add rbx, 0x16EA4 ; add file offset of ReflectiveLoader to shellcode base
call rbx ; call ReflectiveLoader (returns DllMain address)
mov r8d, 0X56A2B5F0 ; EXITFUNC value
push 4 ; push 4 to stack
pop rdx ; pop the value into rdx (second argument of call)
mov rcx, rdi ; move shellcode base address to rcx (first argument of call)
call rax ; call DllMain
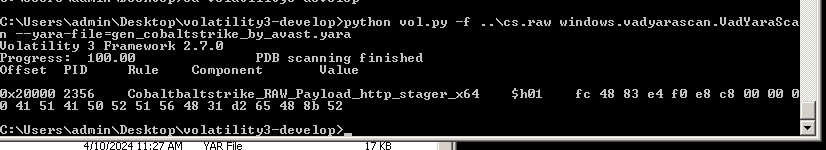
We can further confirm the Cobalt Strike infection using YARA. Utilizing the VadYaraScan plugin in Volatility with YARA rules from Avast Security’s repository can help identify Cobalt Strike instances.
Upon detecting a CobaltStrike HTTP stager in memory, consider using the dumpfiles module in Volatility to isolate the memory of the target process. Additionally, the Beacon parser by SentinelOne can be a useful tool for further investigation.
While tools like Volatility are beneficial for memory analysis, they come with challenges like a steep learning curve and manual analysis requirements. To address these challenges, automating memory forensics processes at scale can be valuable for SOC teams.
Automating Memory Forensics, At Scale
In a Security Operations Center (SOC), handling numerous daily alerts efficiently is crucial. Automating memory acquisition and forensic processes upon receiving suspicious behavior alerts can streamline investigations and responses.
At Intezer, we automate memory forensics using our Endpoint Scanner to quickly analyze memory for potential threats. This automated approach allows for timely and thorough investigations based on alerts received.
By initiating the Endpoint Scanner, users can easily scan processes, detect injected memory modules, and isolate suspicious code within seconds. The user-friendly interface facilitates the identification of suspicious processes for further analysis.

Upon scanning with the Endpoint Scanner, clear identification of Cobalt Strike injected into memory and the process involved can aid in further investigation. The automated memory forensics process simplifies and accelerates threat detection and response.
Discover the unexpected treasures hidden in memory!
The endpoint scanner not only provides IOCs and persistence checkpoints but also works for Linux. Just like in Windows, you can download the scanner and run it with your API key.
After running the scan, you can view the results and see the analysis of the memory.
Best Practices for Memory Forensics Automation
Our scanner is built with automation in mind to cater to incident response and proactive hunting workflows. Analysts often struggle with manual endpoint scans due to time constraints. By integrating with Endpoint Detection and Response (EDR) or Mobile Device Management (MDM) products, our scanner offers an automated analysis process.
Integration with endpoint protection and XDR products like SentinelOne and CrowdStrike is seamless, providing detailed instructions for easy setup.
For added convenience, scripts for Windows and Linux platforms are available for easy integration within EDR products like SentinelOne.
Conclusion
Memory forensics plays a crucial role in combating cyber threats, especially in detecting stealthy attacks that leave no trace. With advanced solutions like Intezer’s endpoint memory scanner for Windows and Linux, memory forensics is now more accessible for every analyst and incident investigation.
Try Intezer for free or schedule a demo to learn more.
Ryan Robinson, a security researcher, and Nicole Fishbein, a malware analyst, contributed to this article. following sentence:
The quick brown fox jumps over the lazy dog.
The fast brown fox leaps over the inactive dog.



