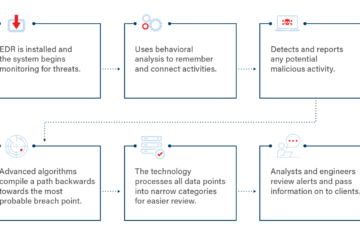
Is safeguarding your company’s sensitive information a key priority for you? Concerned about the increasing complexity and potential harm of cyber threats? If this resonates with you, it’s time to consider implementing an endpoint threat detection and response system. Having a dependable EDR system is crucial in today’s digital landscape, where businesses are constantly targeted by cybercriminals. But what exactly is EDR (Endpoint Detection Response) and why is it imperative for every company to have one? Let’s delve into these questions and explore the solutions they offer.
### What is Endpoint Detection Response?
In today’s world, businesses must proactively protect their data and assets from the ever-evolving cyber threats they face. When it comes to securing endpoints such as PCs, servers, and mobile devices from intrusions, nothing beats an Endpoint Detection Response (EDR) system.
Endpoint threat detection and response surpasses the capabilities of traditional antivirus software by continuously monitoring and analyzing endpoint behavior in real-time, a task that standard antivirus software isn’t equipped to handle. It acts as an additional layer of defense, constantly scrutinizing data transfers, file access, user activities, and system operations. This enables swift detection of any unusual or suspicious behavior that could indicate a potential attack.
Companies serious about enhancing their cybersecurity posture should invest in an endpoint detection response solution. It provides visibility into all activities on endpoints, enabling prompt responses to emerging threats before they can compromise the business.
### The Benefits of Endpoint Detection Response
Staying ahead of cybercriminals is essential for safeguarding your company’s data. What you require is an endpoint threat detection and response solution, also known as Endpoint Detection and Response (EDR). EDR offers several ways to bolster your organization’s defenses.
One primary advantage of EDR is real-time monitoring of your network’s endpoints. This enables immediate identification and mitigation of malicious activities or potential breaches before significant damage occurs.
Furthermore, endpoint threat detection and response tools deliver advanced threat analysis and detection capabilities. While traditional antivirus software may miss sophisticated threats, these technologies excel at detecting them by continuously monitoring network traffic and endpoint behavior patterns.
Another significant benefit is the automation of incident response processes. By automating tasks like malware removal and quarantine with EDR, the efficiency of your incident response is greatly enhanced. This not only eliminates inconsistencies in handling issues but also saves time.
Additionally, the analytical capabilities of EDR tools are invaluable. By analyzing data collected at endpoints, actionable intelligence on new threats and vulnerabilities in your network infrastructure can be obtained.
By demonstrating a proactive approach to cybersecurity through the adoption of an EDR solution, you can earn the trust of customers and other stakeholders. Implementing robust endpoint protection measures reassures customers that their personal information is secure with your organization.
If your company is in need of stronger cybersecurity defenses, investing in an Endpoint Detection Response solution is a wise decision. This technology equips businesses with the tools they need to maintain security in the face of evolving threats in the modern era, offering features such as real-time visibility and automated incident response workflows.
### The Different Types of Endpoint Detection Response
The cybersecurity landscape is rapidly evolving, requiring organizations to adapt swiftly to protect their data. Endpoint detection and response (EDR) solutions are gaining popularity among companies. However, did you know that there are several distinct endpoint threat detection and response tools available? Let’s explore a few of these options.
1. **Agent-based EDR**: This solution entails deploying software agents to all network endpoints, enabling real-time threat identification and response through constant vigilance.
2. **Cloud-based EDR**: Utilizing cloud resources to gather and analyze data from endpoints, this method offers scalability and flexibility, making it ideal for organizations with remote or decentralized teams.
3. **Hybrid EDR**: These systems combine cloud analytics with the robust security of agent-based EDR solutions to enhance endpoint security.
4. **Managed Detection Response (MDR)**: By entrusting tasks like endpoint security monitoring and incident response to a third party, MDR allows for proactive measures against new threats and frees up internal resources.
By exploring the various EDR options available, businesses can find a solution that suits their needs. Whether it’s agent-based, cloud-based, hybrid, or multi-domain reactive, there are options to enhance endpoint security.
As cybercriminals become more sophisticated, investing in robust cybersecurity measures like endpoint detection and response (EDR) is more critical than ever. In the next section, we’ll delve into the specifics of implementing an EDR system in your organization.
### Conclusion – Endpoint Detection Response
Having an endpoint threat detection and response strategy is no longer a luxury but a necessity for any company, given the increasing frequency and sophistication of cyber threats targeting endpoints. In today’s interconnected world, robust cybersecurity measures protect not only sensitive data but also reputation, consumer trust, and overall business continuity. Don’t delay securing your endpoints until tomorrow; take action today.
**See Also: Managed EDR**